|
|
1、详细描述一次加密通讯的过程,结合图示最佳。
以Bob和Alice安全通讯为例:
Bob<--------->Alice
1. Bob要和Alice安全通信首先要取得对方的公钥,即对方的证书,并验证证书的合法性。验证过程和内容:
1)、用CA的公钥(双方已知)解密对方证书中CA的签名;能解密说明证书来原可靠;
2)、用证书中标记的“签名算法”来计算证书的相关信息,并将散列计算的结果与证书“发行者签名”解密的结果(证书特征码)进行比较,如果一致说明证书完整性可靠;
3)、检查证书的有效期限是否在合法范围内,防止证书过期;
4)、验证证书的“主体名称”和预通信的人是否对应;
5)、检查证书是否被吊销;
以上验证成功则说明对方证书可靠,并信任该证书。
2. 取得对方证书(即公钥)后进行如下操作:
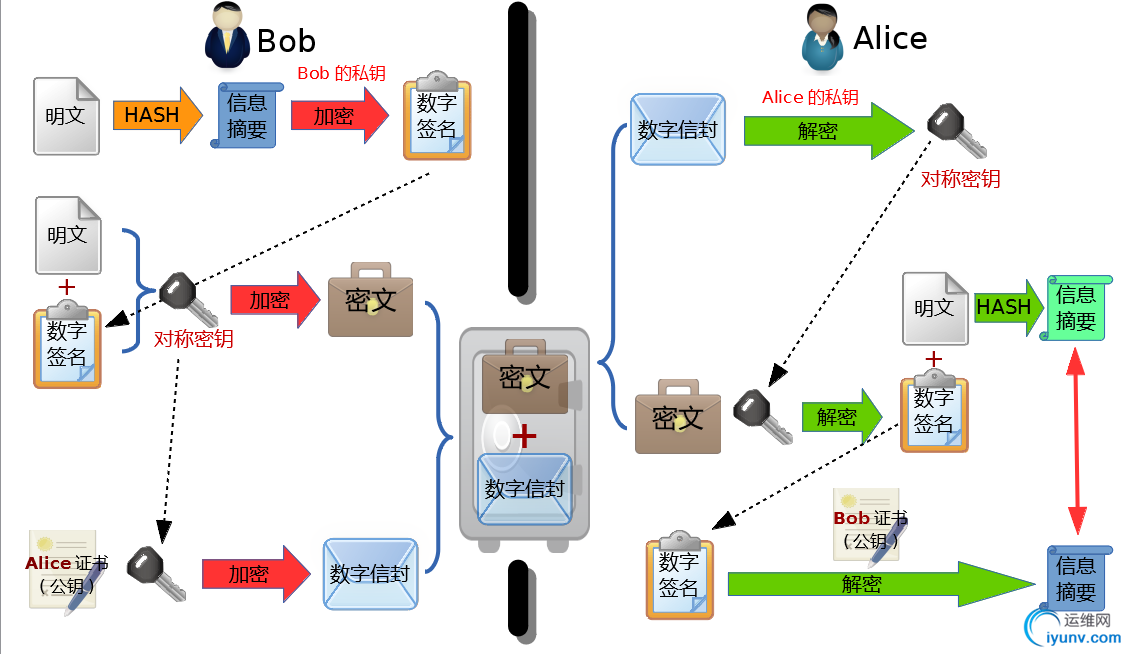
加密:
1)、Bob对明文数据进行散列计算,提取出数据指纹(特征码,也叫信息摘要);
2)、Bob使用自己的私钥对该数据指纹进行加密,生成数字签名,并将该数字签名附加在明文数据之后;
3)、Bob使用一个一次性的对称加密算法密钥对明文和数字签名进行加密,生成密文;
4)、Bob再使用Alice的公钥对对称加密算法的密钥进行加密,生成数字信封;
5)、Bob将密文和数字信封打包发送给Alice;
解密:
1)、Alice收到数据(密文+数字信封)后,使用自己的私钥解密数字信封,得到对称加密算法的密钥;
2)、使用对称加密密钥解密密文,得到明文数据和数字签名。保证了数据的私密性;
3)、使用Bob的公钥解密数字签名,得到明文的数据指纹(特征码)。如果能解出,说明数据为Bob发送,保证了数据的不可否认性;
4)、Alice使用同样的散列算法对明文计算得出数据指纹(特征码),并与Bob计算的数据指纹进行比对,如果一致,说明数据没有被篡改。保证的数据的完整性;
2、描述创建私有CA的过程,以及为客户端发来的证书请求进行办法证书。
应用服务器如果使用证书需向RA(证书注册机构)提出申请,RA对申请人信息进行核验,核验成功后由CA进行签署并生成证书。为了保证CA签署的证书可信,CA在签署客户证书前需要先生成自签证书,客户端会使用CA的证书来验证CA所签署的证书。
证书颁发过程:
1)、申请方向RA递交证书申请;
2)、RA会要求申请人递交自己的公钥和其它相关信息;
3)、RA核验该申请方的真实信息;
4)、核验通过后,RA会将请求转交给CA进行签署。由CA对这些信息进行散列,并用自己的私钥对散列结果进行加密,生成数字签名;
5)、将申请方的信息和数字签名一起封装到证书内,颁发给申请方;
证书申请及签署实例(使用自建CA签署证书时CA和RA可合并):
1) 构建私有CA:
(1) 检查安装openssl;
(2) 根据openssl的配置文件(/etc/pki/tls/openssl.cnf)创建所需要的文件;
# touch /etc/pki/CA/index.txt #创建证书索引文件
# echo 01 > /etc/pki/CA/serial #设置证书的序列号 (3) 自签证书:
# (umask 077; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048) #生成CA的私钥
# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem #生成自签证书签署请求,只有在生成自签证书时使用-x509选项
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Beijing
Locality Name (eg, city) [Default City]:Beijing
Organization Name (eg, company) [Default Company Ltd]:Yinkai
Organizational Unit Name (eg, section) []:Ops
Common Name (eg, your name or your server's hostname) []:ca.yinkai.site
Email Address []:caadmin@yinkai.site
2) 为客户端签发证书:
(1) 客户端提交证书签署请求:
# (umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048) #客户端生成私钥
# openssl req -new -key /etc/httpd/ssl/httpd.key -days 365 -out /etc/httpd/ssl/httpd.csr #客户端生成证书签署请求文件
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Beijing
Locality Name (eg, city) [Default City]:Beijing
Organization Name (eg, company) [Default Company Ltd]:Yinkai
Organizational Unit Name (eg, section) []:Tech
Common Name (eg, your name or your server's hostname) []:www.yinkai.site #此处的公共名需与实际使用的服务器访问名称一致
Email Address []:caadmin@yinkai.site
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []: (2) 将证书签署请求发给RA(此处RA与CA一致)
# scp /etc/httpd/ssl/httpd.csr root@192.168.1.71:/tmp (3) CA签署请求:
# openssl ca -in /tmp/httpd.csr -days 365 -out /etc/pki/CA/certs/httpd.crt
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Oct 29 06:53:10 2016 GMT
Not After : Oct 29 06:53:10 2017 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijing
organizationName = Yinkai
organizationalUnitName = Tech
commonName = www.yinkai.site
emailAddress = caadmin@yinkai.site
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
4B:08:90:15:E3:FE:E2:44:AF:BD:C2:79:F9:13:4A:B8:FB:70:BF:4A
X509v3 Authority Key Identifier:
keyid:32:43:7A:30:8C:2E:22:87:85:63:04:F1:37:D4:8C:4D:3B:41:10:B8
Certificate is to be certified until Oct 29 06:53:10 2017 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated (4) 将证书发送给请求客户端:
# scp /etc/pki/CA/certs/httpd.crt root@192.168.1.61:/etc/httpd/ssl/
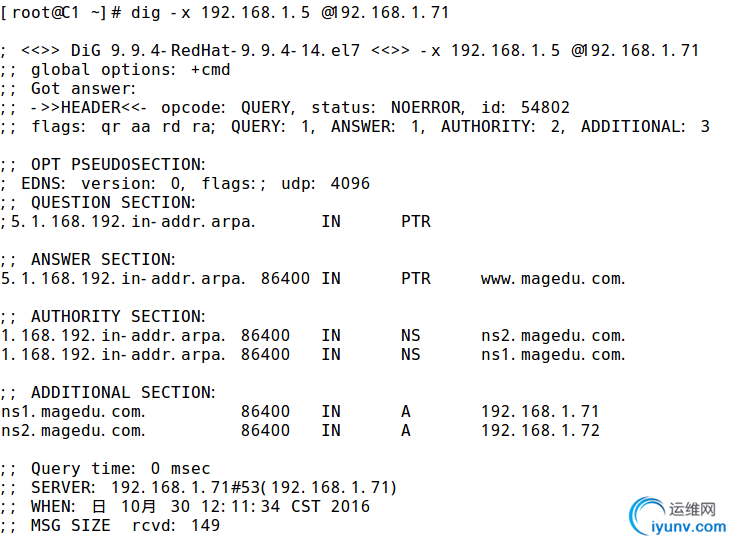
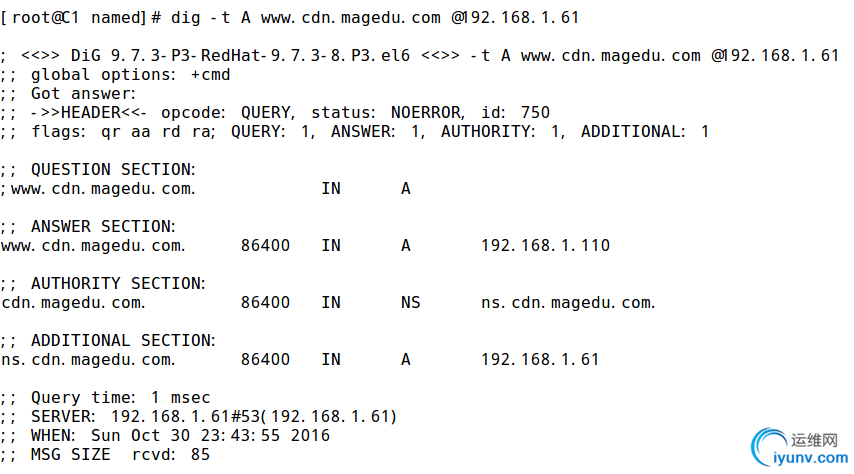
3、搭建一套DNS服务器,负责解析magedu.com域名(自行设定主机名及IP)
(1)、能够对一些主机名进行正向解析和逆向解析;
(2)、对子域cdn.magedu.com进行子域授权,子域负责解析对应子域中的主机名;
(3)、为了保证DNS服务系统的高可用性,请设计一套方案,并写出详细的实施过程
环境说明:
magedu.com主ns服务器IP:192.168.1.71
magedu.com辅助ns服务器:192.168.1.72
cdn.magedu.com子域ns服务器:192.168.1.61
主域名称服务器(192.168.1.71):
bind主配置文件(/etc/named.conf)如下:
acl slaves { //定义辅助ns
192.168.1.71;
192.168.1.72;
127.0.0.1;
};
acl mynet { //定义接受递归的服务器
192.168.1.71;
192.168.1.61;
127.0.0.1;
};
options {
listen-on port 53 { 127.0.0.1; 192.168.1.71; }; //定义监听的IP
//listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
forward first; //定义转发服务器。接受“mynet”递归请求,转发至8.8.8.8
forwarders { 8.8.8.8; };
allow-recursion { mynet; };
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key"; 编辑/etc/named.rfc1912.zones,添加以下区域:
zone "1.168.192.in-addr.arpa" IN {
type master;
file "192.168.1.zone";
allow-update { none; };
};
zone "magedu.com" IN {
type master;
file "magedu.com.zone";
allow-query { any; };
allow-transfer { slaves; }; //接受“slaves”传输请求
allow-update { none; };
}; 添加区域资源记录:
正向资源记录:
# cat magedu.com.zone
$TTL 1D
$ORIGIN magedu.com.
@ IN SOA ns1.magedu.com. admin.magedu.com (
2016103002
1H
5M
7D
1D )
IN NS ns1
IN NS ns2
IN MX 10 mx1
IN MX 20 mx2
ns1 IN A 192.168.1.71
ns2 IN A 192.168.1.72
mx1 IN A 192.168.1.100
mx2 IN A 192.168.1.200
www IN A 192.168.1.5
cdn IN NS ns.cdn
ns.cdn IN A 192.168.1.61
* IN A 192.168.1.100 反向资源记录:
# cat 192.168.1.zone
$TTL 1D
$ORIGIN 1.168.192.in-addr.arpa.
@ IN SOA ns1.magedu.com. admin.magedu.com. (
2016103001
1H
5M
7D
1D )
IN NS ns1.magedu.com.
IN NS ns2.magedu.com.
71 IN PTR ns1.magedu.com.
72 IN PTR ns2.magedu.com.
100 IN PTR mx1.magedu.com.
200 IN PTR mx2.magedu.com.
5 IN PTR www.magedu.com.
61 IN PTR ns.cdn.magedu.com. 辅助名称服务器(192.168.1.72):
/etc/named.conf:
options {
listen-on port 53 { 127.0.0.1; 192.168.1.72; };
//listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key"; /etc/named.rfc1912.zones添加以下部分:
zone "magedu.com" IN {
type slave;
masters { 192.168.1.71; };
file "slaves/magedu.com.zone";
};
zone "1.168.192.in-addr.arpa" IN {
type slave;
masters { 192.168.1.71; };
file "slaves/192.168.1.zone";
}; cdn.magedu.com子域服务器(192.168.1.61):
/etc/named.conf:
options {
listen-on port 53 { 127.0.0.1; 192.168.1.61; };
//listen-on-v6 port 53 { ::1; };
directory "/var/named";
allow-query { any; };
recursion yes;
forward first; //定义全局转发服务器,当主服务器不予递归时再将请求转发至根域服务器
forwarders { 192.168.1.71; };
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones"; /etc/named.rfc1912.zones
zone "cdn.magedu.com" IN {
type master;
file "cdn.magedu.com.zone";
allow-update { none; };
};
//zone "magedu.com" IN { //定义区域转发服务器,与全局转发选其一。区域转发只转发magedu.com域的请求
// type forward;
// forward only;
// forwarders { 192.168.1.71; 192.168.1.72; };
//}; /var/named/cdn.magedu.com.zone:
$TTL 1D
$ORIGIN cdn.magedu.com.
@ IN SOA ns.cdn.magedu.com. admin.cdn.magedu.com. (
2016103001
1H
5M
7D
1D )
IN NS ns
IN MX 10 mx
ns IN A 192.168.1.61
mx IN A 192.168.1.101
www IN A 192.168.1.110
* IN A 192.168.1.111
重启named服务后验证:
主域服务器测试正反解析:

测试辅助服务器正反解析:


测试子域服务器:

4、请描述一次完整的http请求处理过程;
http请求处理过程:
1) 客户端递归请求服务器网站域名,DNS服务器解析到结果后返回给客户端;
2) 客户端使用IP地址向http服务器发起TCP三次握手;
3) 客户端封装http报文,并向http服务器发起请求;
4) http服务器解析请求,获取URL中指定资源,构建响应报文并封装为http响应报文返回给客户端;
5) 客户端收到http响应报文后由浏览器负责解析并渲染呈现给用户,并记录日志。完成一个http事务。在此过程中http返回的响应报文有可能引用了多个服务器资源,若服务器没有启用“KeepAlived”则每个资源的获取都需要一个tcp三次握手和四次断开过程。
5、httpd所支持的处理模型有哪些,他们的分别使用于哪些环境。
httpd支持以下三种处理模型(MPM):
prefork: 多进程模型。一个主进程负责生成多个工作进程,每个工作进程处理一个用户请求;即使没有用户请求也会预先生成多个工作进程,以便随时响应用户请求,默认8个,最大不会超过1024个;特点是工作稳定,进程间独立工作,某个进程挂起不会影响其它进程。用于请求量不大,但稳定性要求较高的环境;
worker: 多线程模型。一个主进程负责生成多个子进程(m,默认4个),每个子进程负责生成多个线程(n),由线程处理用户请求,同时可接受m×n个http请求。由于linux中进程的轻量化设计,进程与线程的效率无太大差别,所以工作效率与profork也没有太大差异,但一个工作进程中的多个线程共享一个内存数据区,某个线程故障会影响到同进程下的其它线程,故稳定性不如prefork;
event: 事件驱动模型。一个主进程负责生成多个工作进程(m),每个进程基于epoll事件通知机制直接响应多个用户请求(n)。同时可响应m*n个用户>请求,httpd2.4中可用于生产。
6、建立httpd服务器(基于编译的方式进行),要求:
提供两个基于名称的虚拟主机:
(a)www1.stuX.com,页面文件目录为/web/vhosts/www1;错误日志为/var/log/httpd/www1.err,访问日志为/var/log/httpd/www1.access;
(b)www2.stuX.com,页面文件目录为/web/vhosts/www2;错误日志为/var/log/httpd/www2.err,访问日志为/var/log/httpd/www2.access;
(c)为两个虚拟主机建立各自的主页文件index.html,内容分别为其对应的主机名;
(d)通过www1.stuX.com/server-status输出httpd工作状态相关信息,且只允许提供帐号密码才能访问(status:status);
在RHEL6上编译安装httpd2.4
(1) 环境准备:
httpd的运行依赖于apr1.4+和apr-util1.4(apr和apr-util(apr-util为apr的工具组件)相当于httpd的虚拟机)。httpd2.4依赖1.4版以上的apr和apr-util,而RHEL6默认安装的apr和apr-utils版本为1.3.9,为了不影响其他程序对apr-1.3.9的依赖,需单独编译安装apr和apr-util1.4以上版。
1).编译安装apr-1.5.2和apr-util-1.5.4:
[root@C1 ~]# tar xf /tmp/httpd/apr-1.5.2.tar.bz2 -C /usr/local/src/
[root@C1 ~]# cd /usr/local/src/apr-1.5.2/
[root@C1 apr-1.5.2]# ./configure --prefix=/usr/local/apr-1.5.2
[root@C1 apr-1.5.2]# make && make install[root@C1 httpd]# tar xf apr-util-1.5.4.tar.bz2 -C /usr/local/src/
[root@C1 httpd]# cd /usr/local/src/apr-util-1.5.4/
[root@C1 apr-util-1.5.4]# ./configure --prefix=/usr/local/apr-util-1.5.4 --with-apr=/usr/local/apr-1.5.2/
[root@C1 apr-util-1.5.4]# make && make install #创建apr和apr-util的链接文件,以便后期引用:
[root@C1 ~]# ln -s /usr/local/apr-1.5.2/ /usr/local/apr
[root@C1 ~]# ln -s /usr/local/apr-util-1.5.4/ /usr/local/apr-util 2).安装PCRE(Perl Compatible Regular Expressions)的开发库:
[root@C1 ~]# yum install -y pcre-devel 3).创建apache系统用户:
[root@C1 ~]# useradd -r apache (2) 编译安装httpd-2.4:
1).安装httpd程序:
[root@C1 httpd]# tar xv httpd-2.4.23.tar.bz2 -C /usr/local/src/
[root@C1 httpd]# cd /usr/local/src/httpd-2.4.23/
[root@C1 httpd-2.4.23]# ./configure --prefix=/usr/local/httpd24 --sysconf=/etc/httpd24 --enable-ssl --enable-cgi --enable-rewrite --with-zlib --with-pcre --with-apr=/usr/local/apr --with-apr-util=/usr/local/apr-util --enable-so --enable-modules=most --enable-mpms-shared=all --with-mpm=prefork #选项说明:
--prefix=/usr/local/httpd24:指定httpd的安装路径;
--sysconf=/etc/httpd24:指定httpd的配置文件路径,为了不与系统上已安装的httpd2.2相冲突,需另指一个目录;
--enable-ssl:启用SSL功能
--enable-cgi:启用cgi机制;
--enable-rewrite:启用URL重写机制;
--with-zlib:当使用compress压缩机制时,需加载压缩算所使用的压缩库;
--with-pcre:启用PCRE库。通常在使用URL重写或过滤时会用到。注意:在使用该选项编译httpd前需事先安装pcre-devel;
--with-apr=/usr/local/apr:指定apr的安装路径;
--with-apr-util=/usr/local/apr-util/:指定apr-util的安装路径;
--enable-so:启用动态模块加载机制;
--enable-modules=most:指定要编译的模块。可用选项:"all" | "most" | "few" | "none" | "reallyall";
--enable-mpms-shared=all:httpd支持DSO(共享模块编译机制),此处将编译所有支持的MPM模块。可用选项:"all" | "most" | "few" | "reallyall"
--with-mpm=prefork:指定httpd默认使用的MPM处理模块。MPM={event|worker|prefork|winnt}
[root@C1 httpd-2.4.23]# make && make install 2).将httpd-2.4的程序目录添加到PATH环境变量中:
[root@C1 init.d]# vim /etc/profile.d/httpd24.sh
export PATH=/usr/local/httpd24/bin:$PATH
[root@C1 init.d]# . /etc/profile.d/httpd24.sh
[root@C1 init.d]# echo $PATH
/usr/local/httpd24/bin:/usr/lib/qt-3.3/bin:/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin:/root/bin
[root@C1 init.d]# which httpd
/usr/local/httpd24/bin/httpd 3).启动httpd-2.4:
#注意:启动前要确保80/tcp端口没有被占用。
[root@C1 httpd-2.4.23]# apachectl start #测试httpd-2.4是否成功启动:
[root@C1 httpd-2.4.23]# ss -taln | grep :80
0 128 :::80 :::*
[root@C1 httpd-2.4.23]# ps aux | grep httpd
root 4415 0.0 0.3 4500 1828 ? Ss 16:59 0:00 /usr/local/httpd24/bin/httpd -k start
daemon 4416 0.0 0.2 4500 1228 ? S 16:59 0:00 /usr/local/httpd24/bin/httpd -k start
daemon 4417 0.0 0.2 4500 1228 ? S 16:59 0:00 /usr/local/httpd24/bin/httpd -k start
daemon 4418 0.0 0.2 4500 1228 ? S 16:59 0:00 /usr/local/httpd24/bin/httpd -k start
daemon 4419 0.0 0.2 4500 1228 ? S 16:59 0:00 /usr/local/httpd24/bin/httpd -k start
daemon 4420 0.0 0.2 4500 1228 ? S 16:59 0:00 /usr/local/httpd24/bin/httpd -k start
root 4443 0.0 0.1 4328 724 pts/0 S+ 17:02 0:00 grep httpd (3) 配置httpd服务器
1) 创建数据目录,并准备测试页面:
[root@C1 extra]# mkdir -vp /web/vhosts/www{1,2}
mkdir: created directory `/web'
mkdir: created directory `/web/vhosts'
mkdir: created directory `/web/vhosts/www1'
mkdir: created directory `/web/vhosts/www2'
[root@C1 extra]# echo "The vhost1 site." > /web/vhosts/www1/index.html
[root@C1 extra]# echo "The vhost2 site." > /web/vhosts/www2/index.html 2) 编辑httpd-2.4的配置文件:
[root@C1 httpd24]# cp -p httpd.conf{,bak}
#备份原始的配置文件 /etc/httpd24/httpd.conf:
[root@C1 ~]# egrep -v '^#|^$|^[[:space:]]+#' /etc/httpd24/httpd.conf
ServerRoot "/usr/local/httpd24"
Listen 80#定义httpd-2.4监听端口
LoadModule authn_file_module modules/mod_authn_file.so
LoadModule authn_core_module modules/mod_authn_core.so
LoadModule authz_host_module modules/mod_authz_host.so
LoadModule authz_groupfile_module modules/mod_authz_groupfile.so
LoadModule authz_user_module modules/mod_authz_user.so
LoadModule authz_core_module modules/mod_authz_core.so
LoadModule access_compat_module modules/mod_access_compat.so
LoadModule auth_basic_module modules/mod_auth_basic.so
LoadModule reqtimeout_module modules/mod_reqtimeout.so
LoadModule filter_module modules/mod_filter.so
LoadModule mime_module modules/mod_mime.so
LoadModule log_config_module modules/mod_log_config.so
LoadModule env_module modules/mod_env.so
LoadModule headers_module modules/mod_headers.so
LoadModule setenvif_module modules/mod_setenvif.so
LoadModule version_module modules/mod_version.so
LoadModule mpm_prefork_module modules/mod_mpm_prefork.so
LoadModule unixd_module modules/mod_unixd.so
LoadModule status_module modules/mod_status.so
LoadModule autoindex_module modules/mod_autoindex.so
<IfModule !mpm_prefork_module>
</IfModule>
<IfModule mpm_prefork_module>
</IfModule>
LoadModule dir_module modules/mod_dir.so
LoadModule alias_module modules/mod_alias.so
<IfModule unixd_module>
User apache#修改httpd的启动用户。编译安装的httpd-2.4默认使用deamon用户来启动httpd,需修改为apache:
Group apache
</IfModule>
ServerAdmin you@example.com
<Directory />
AllowOverride none
Require all denied
</Directory>
DocumentRoot "/web/vhosts"#修改httpd的主目录
<Directory "/web/vhosts">
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>
<IfModule dir_module>
DirectoryIndex index.html
</IfModule>
<Files ".ht*">
Require all denied
</Files>
ErrorLog "logs/error_log"
LogLevel warn
<IfModule log_config_module>
LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" combined
LogFormat "%h %l %u %t \"%r\" %>s %b" common
<IfModule logio_module>
LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\" %I %O" combinedio
</IfModule>
CustomLog "logs/access_log" common
</IfModule>
<IfModule alias_module>
ScriptAlias /cgi-bin/ "/usr/local/httpd24/cgi-bin/"
</IfModule>
<IfModule cgid_module>
</IfModule>
<Directory "/usr/local/httpd24/cgi-bin">
AllowOverride None
Options None
Require all granted
</Directory>
<IfModule mime_module>
TypesConfig /etc/httpd24/mime.types
AddType application/x-compress .Z
AddType application/x-gzip .gz .tgz
</IfModule>
Include /etc/httpd24/extra/httpd-vhosts.conf#加载虚拟主机配置文件
<IfModule proxy_html_module>
Include /etc/httpd24/extra/proxy-html.conf
</IfModule>
<IfModule ssl_module>
SSLRandomSeed startup builtin
SSLRandomSeed connect builtin
</IfModule>
/etc/httpd24/extra/httpd-vhosts.conf:
[root@C1 ~]# egrep -v '^#|^$' /etc/httpd24/extra/httpd-vhosts.conf<VirtualHost *:80>
ServerName www1.stuX.com
DocumentRoot "/web/vhosts/www1"#定义www1虚拟主机的数据目录
ErrorLog "/web/vhosts/www1.err"#定义错误日志文件
CustomLog "/web/vhosts/www1.access" common#定义访问日志文件
<Location /server-status>#定义"www1.stuX.com/server-status"
SetHandler server-status
AuthType Basic#认证类型为Basic
AuthName "Administrator Private."#认证时的提示信息
AuthBasicProvider file#认证方式
AuthUserFile "/etc/httpd24/extra/.htpasswd"#认证文件,用于存储用户名和密码
<RequireAll>
Require valid-user#允许账号文件中的所有用户登录访问
</RequireAll>
</Location>
</VirtualHost>
<VirtualHost *:80>
ServerName www2.stuX.com
DocumentRoot "/web/vhosts/www2"
ErrorLog "/web/vhosts/www2.err"
CustomLog "/web/vhosts/www2.access" common
</VirtualHost>
3) 配置用户认证:
添加认证用户:
[root@C1 ~]# cd /etc/httpd24/extra/
[root@C1 extra]# htpasswd -c -s -b .htpasswd yinkai yinkaipass
Adding password for user yinkai 选项说明:
-c: 创建用户文件,只在第一次使用
-s: 强制使用SHA加密用户密码
-b: 从命令行读取用户密码
测试:
[root@C1 httpd24]# ps aux | grep httpd#检查httpd是否以apache用户成功启动
root 4415 0.0 0.4 4500 2148 ? Ss 16:59 0:00 /usr/local/httpd24/bin/httpd -k start
apache 4495 0.0 0.2 4500 1232 ? S 17:18 0:00 /usr/local/httpd24/bin/httpd -k start
apache 4496 0.0 0.2 4500 1232 ? S 17:18 0:00 /usr/local/httpd24/bin/httpd -k start
apache 4497 0.0 0.2 4500 1232 ? S 17:18 0:00 /usr/local/httpd24/bin/httpd -k start
apache 4498 0.0 0.2 4500 1232 ? S 17:18 0:00 /usr/local/httpd24/bin/httpd -k start
apache 4499 0.0 0.2 4500 1232 ? S 17:18 0:00 /usr/local/httpd24/bin/httpd -k start
root 4501 0.0 0.1 4328 720 pts/0 S+ 17:18 0:00 grep httpd

7、为第6题中的第2个虚拟主机提供https服务,使得用户可以通过https安全的访问此web站点;
(1)要求使用证书认证,证书中要求使用的国家(CN)、州(HA)、城市(ZZ)和组织(MageEdu);
(2)设置部门为Ops,主机名为www2.stuX.com,邮件为admin@stuX.com;
1. 创建私有CA服务器
(1) 根据openssl配置文件(/etc/pki/tls/openssl.cnf)准备CA服务器环境:
[root@C1 ~]# cd /etc/pki/CA/ //切换到CA根目录
[root@C1 CA]# touch index.txt //创建证书数据库索引文件
[root@C1 CA]# echo 01 > serial //设置当前证书(第一个)序列号 (2) 生成CA的私钥
[root@C1 CA]# (umask 077; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus
......+++
..........................................+++
e is 65537 (0x10001) (3) 生成CA自签证书
[root@C1 CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HA
Locality Name (eg, city) [Default City]:ZZ
Organization Name (eg, company) [Default Company Ltd]:MageEdu
Organizational Unit Name (eg, section) []:Ops
Common Name (eg, your name or your server's hostname) []:ca.stuX.com
Email Address []:admin@stuX.com (4) 检查CA自签证书内容:
[root@C1 CA]# openssl x509 -in /etc/pki/CA/cacert.pem -noout -subject
subject= /C=CN/ST=HA/L=ZZ/O=MageEdu/OU=Ops/CN=ca.stuX.com/emailAddress=admin@stuX.com 2. http服务器申请签署证书
(1) 客户端生成证书签署请求:
[root@C1 ~]# mkdir /etc/httpd24/ssl
[root@C1 ~]# cd /etc/httpd24/ssl
[root@C1 ssl]# (umask 077; openssl genrsa -out httpd.key 2048)
Generating RSA private key, 2048 bit long modulus
.................................................................................................................................................................................................................................................................................................................+++
...........+++
e is 65537 (0x10001)
[root@C1 ssl]# openssl req -new -key httpd.key -days 3650 -out httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HA
Locality Name (eg, city) [Default City]:ZZ
Organization Name (eg, company) [Default Company Ltd]:MageEdu
Organizational Unit Name (eg, section) []:Ops
Common Name (eg, your name or your server's hostname) []:www2.stuX.com
Email Address []:admin@stuX.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []: (2) 将证书签署请求发送给CA(RA):
[root@C1 ssl]# scp httpd.csr root@192.168.1.97:/tmp (3) CA为http服务器签署证书:
[root@C1 CA]# openssl ca -in /tmp/httpd.csr -days 3650 -out /etc/pki/CA/certs/httpd.crt
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Nov 17 09:22:25 2016 GMT
Not After : Nov 15 09:22:25 2026 GMT
Subject:
countryName = CN
stateOrProvinceName = HA
organizationName = MageEdu
organizationalUnitName = Ops
commonName = www2.stuX.com
emailAddress = admin@stuX.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
BD:64:23:20:D3:3B:79:0C:C4:2B:AB:F4:47:84:6F:54:38:78:68:5B
X509v3 Authority Key Identifier:
keyid:C1:CA:83:F5:FA:CC:BA:15:CE:BC:D2:A1:13:1D:6F:17:5F:C9:59:0C
Certificate is to be certified until Nov 15 09:22:25 2026 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated (4) 检查http服务器证书,并将该证书传递给http服务器:
[root@C1 CA]# openssl x509 -in /etc/pki/CA/certs/httpd.crt -noout -subject
subject= /C=CN/ST=HA/O=MageEdu/OU=Ops/CN=www2.stuX.com/emailAddress=admin@stuX.com
[root@C1 CA]# scp /etc/pki/CA/certs/httpd.crt root@192.168.1.83:/etc/httpd24/ssl/ #重启名虚拟主机的证书和私钥文件,以便后期引用:
[root@C1 ~]# cd /etc/httpd24/ssl/
[root@C1 ssl]# mv httpd.crt www2.stuX.com.crt
[root@C1 ssl]# mv httpd.key www2.stuX.com.key 3. 配置http服务器使用证书使之支持https
(1) 为httpd安装mod_ssl模块:
[root@C1 ~]# yum install -y mod_ssl (2)检查httpd主配置文件/etc/httpd24/httpd.conf是否存在并启用以下条目:
LoadModule ssl_module modules/mod_ssl.so
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so
Include /etc/httpd24/extra/httpd-ssl.conf (3) 修改ssl相关的配置文件/etc/httpd24/extra/httpd-ssl.conf:
[root@C1 extra]# egrep -v '^#|^$' httpd-ssl.conf
Listen 443
SSLCipherSuite HIGH:MEDIUM:!MD5:!RC4
SSLProxyCipherSuite HIGH:MEDIUM:!MD5:!RC4
SSLHonorCipherOrder on
SSLProtocol all -SSLv3
SSLProxyProtocol all -SSLv3
SSLPassPhraseDialog builtin
SSLSessionCache "shmcb:/usr/local/httpd24/logs/ssl_scache(512000)"
SSLSessionCacheTimeout 300
<VirtualHost *:443>#定义基于443端口的虚拟主机
DocumentRoot "/web/vhosts/www2"
ServerName www2.stuX.com:443
ServerAdmin you@example.com
ErrorLog "/web/vhosts/www2.err"
TransferLog "/web/vhosts/www2.access"
SSLEngine on
SSLCertificateFile "/etc/httpd24/ssl/www2.stuX.com.crt"#指定www2.stuX.com.crt虚拟主机的证书文件
SSLCertificateKeyFile "/etc/httpd24/ssl/www2.stuX.com.key"#指定www2.stuX.com.crt虚拟主机的私钥文件
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory "/usr/local/httpd24/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
BrowserMatch "MSIE [2-5]" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
CustomLog "/usr/local/httpd24/logs/ssl_request_log" \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost> (4) 在虚拟主机相关的配置文件/etc/httpd24/extra/httpd-vhosts.conf中注释掉80端口的www2.stuX.com主机。可选:
#<VirtualHost *:80>
# ServerName www2.stuX.com
# DocumentRoot "/web/vhosts/www2"
# ErrorLog "/web/vhosts/www2.err"
# CustomLog "/web/vhosts/www2.access" common
#</VirtualHost>
4. 检查配置文件,重启服务并检查443端口:
[root@C1 ~]# httpd -t
Syntax OK
[root@C1 ~]# apachectl restart
[root@C1 ~]# ss -tanl | grep :443
0 128 :::443 :::*
5. 测试:

8、建立samba共享,共享目录为/data,要求:(描述完整的过程)
1)共享名为shared,工作组为magedu;
2)添加组develop,添加用户gentoo,centos和ubuntu,其中gentoo和centos以develop为附加组,ubuntu不属于develop组;密码均为用户名;
3)添加samba用户gentoo,centos和ubuntu,密码均为“mageedu”;
4)此samba共享shared仅允许develop组具有写权限,其他用户只能以只读方式访问;
5)此samba共享服务仅允许来自于172.16.0.0/16网络的主机访问;
安装samba服务器程序、samba客户端工具和公共库:
[root@C1 ~]# yum install -y samba samba-common samba-client 添加系统用户和组:
[root@C1 ~]# groupadd develop
[root@C1 ~]# useradd -G develop gentoo; echo "gentoo" | passwd --stdin gentoo
Changing password for user gentoo.
passwd: all authentication tokens updated successfully.
[root@C1 ~]# useradd -G develop centos; echo "centos" | passwd --stdin centos
Changing password for user centos.
passwd: all authentication tokens updated successfully.
[root@C1 ~]# useradd ubuntu; echo "ubuntu" | passwd --stdin ubuntu
Changing password for user ubuntu.
passwd: all authentication tokens updated successfully. 创建共享目录并编辑权限:
[root@C1 ~]# mkdir -v /data
mkdir: created directory ‘/data’
[root@C1 ~]# setfacl -m g:develop:rwx /data/
[root@C1 ~]# getfacl /data/
getfacl: Removing leading '/' from absolute path names
# file: data/
# owner: root
# group: root
user::rwx
group::r-x
group:develop:rwx
mask::rwx
other::r-x 添加samba用户:
[root@C1 ~]# smbpasswd -a gentoo
New SMB password:
Retype new SMB password:
Added user gentoo.
[root@C1 ~]# smbpasswd -a centos
New SMB password:
Retype new SMB password:
Added user centos.
[root@C1 ~]# smbpasswd -a ubuntu
New SMB password:
Retype new SMB password:
Added user ubuntu.
[root@C1 ~]# pdbedit -L//列出所有的samba用户
gentoo:1039:
ubuntu:1041:
centos:1040: 修改samba配置文件创建编辑共享:
[root@C1 ~]# cp -p /etc/samba/smb.conf{,.bak}
[root@C1 ~]# cp -p /etc/samba/smb.conf{,.bak}
[global]
workgroup = magedu
server string = Samba Server Version %v
netbios name = MYSERVER
hosts allow = 192.168.1.0/24#环境所限,此处代替172.16.0.0/16网络
log file = /var/log/samba/log.%m
max log size = 50
security = user
passdb backend = tdbsam
load printers = yes
cups options = raw
[homes]
comment = Home Directories
browseable = no
writable = yes
[shared]
comment = develop's directory
path = /data
guest ok = yes
writable = yes
write list = +develop 测试samba配置文件是否有语法错误:
[root@C1 ~]# testparm
Load smb config files from /etc/samba/smb.conf
rlimit_max: increasing rlimit_max (1024) to minimum Windows limit (16384)
Processing section "[homes]"
Processing section "[shared]"
Loaded services file OK.
Server role: ROLE_STANDALONE
Press enter to see a dump of your service definitions
[global]
workgroup = MAGEDU
netbios name = MYSERVER
server string = Samba Server Version %v
log file = /var/log/samba/log.%m
max log size = 50
idmap config * : backend = tdb
hosts allow = 192.168.1.0/24
cups options = raw
[homes]
comment = Home Directories
read only = No
browseable = No
[shared]
comment = develop's directory
path = /data
write list = +develop
read only = No
guest ok = Yes 启动并检查smb服务:
[root@C1 ~]# systemctl start smb.service
[root@C1 ~]# systemctl start nmb.service
[root@C1 ~]# ss -tnlap | grep smb
LISTEN 0 50 *:139 *:* users:(("smbd",pid=2259,fd=34))
LISTEN 0 50 *:445 *:* users:(("smbd",pid=2259,fd=33))
LISTEN 0 50 :::139 :::* users:(("smbd",pid=2259,fd=32))
LISTEN 0 50 :::445 :::* users:(("smbd",pid=2259,fd=31)) 验证:
[root@C1 ~]# smbclient -L 192.168.1.71 -U centos
Enter centos's password:
Domain=[MAGEDU] OS=[Unix] Server=[Samba 4.1.1]
Sharename Type Comment
--------- ---- -------
IPC$ IPC IPC Service (Samba Server Version 4.1.1)
shared Disk develop's directory
centos Disk Home Directories
Domain=[MAGEDU] OS=[Unix] Server=[Samba 4.1.1]
Server Comment
--------- -------
MYSERVER Samba Server Version 4.1.1
Workgroup Master
--------- -------
MAGEDU MYSERVER
WORKGROUP YINKAI-NB-X230
从Windows登陆\\192.168.1.71,并创建测试文件:
[root@C1 tmp]# ll /data/
total 0
-rwxr--r-- 1 centos centos 0 11月 16 22:05 centos.txt
-rwxr--r-- 1 gentoo gentoo 0 11月 16 22:05 gentoo.txt9、搭建一套文件vsftp文件共享服务,共享目录为/ftproot,要求:(描述完整的过程)
1)基于虚拟用户的访问形式;
2)匿名用户只允许下载,不允许上传;
3)禁锢所有的用户于其家目录当中;
4)限制最大并发连接数为200:;
5)匿名用户的最大传输速率512KB/s
6)虚拟用户的账号存储在mysql数据库当中。
7)数据库通过NFS进行共享。
环境说明:
FTP服务器:192.168.1.71
Mariadb服务器:192.168.1.71
NFS服务器:192.168.1.72
1. 在192.168.1.72上搭建NFS服务器
(1). 创建nfs目录,用户实际存储数据:
[root@C2 ~]# mkdir -vp /shared/nfs
mkdir: created directory `/shared'
mkdir: created directory `/shared/nfs'
[root@C2 ~]# useradd -r -M -s /sbin/nologin mysql
[root@C2 ~]# chown -R mysql.mysql /shared/nfs/ (2). 修改nfs配置文件,定义导出目录:
[root@C2 ~]# vim /etc/exports
/shared/nfs 192.168.1.0/24(rw,no_root_squash) (3). 启动nfs服务:
[root@C2 ~]# systemctl start nfs.service
[root@C2 ~]# ss -tnlp | egrep '2049|rpc'
LISTEN 0 128 *:111 *:* users:(("rpcbind",pid=1645,fd=8))
LISTEN 0 128 *:20048 *:* users:(("rpc.mountd",pid=2098,fd=8))
LISTEN 0 128 *:46620 *:* users:(("rpc.statd",pid=1643,fd=9))
LISTEN 0 64 *:2049 *:*
LISTEN 0 128 :::37518 :::* users:(("rpc.statd",pid=1643,fd=11))
LISTEN 0 128 :::111 :::* users:(("rpcbind",pid=1645,fd=11))
LISTEN 0 128 :::20048 :::* users:(("rpc.mountd",pid=2098,fd=10))
LISTEN 0 64 :::2049 :::* 2. 在192.168.1.71上搭建Mariadb服务器,并使用NFS作为存储
(1). 使用NFS文件系统,并挂载为数据库目录:
[root@C1 ~]# showmount -e 192.168.1.72 #查看NFS服务器导出的目录
Export list for 192.168.1.72:
/shared/nfs 192.168.1.0/24
[root@C1 ~]# mkdir /data #作为数据库存储目录
[root@C1 ~]# mount -t nfs 192.168.1.72:/shared/nfs /data/ (2). 安装配置MariaDB:
[root@C2 ~]# id mysql
uid=992(mysql) gid=989(mysql) 组=989(mysql)
[root@C1 ~]# groupadd -r -g 989 mysql
[root@C1 ~]# useradd -r -s /sbin/nologin -M -u 992 -g 989 mysql #与NFS服务器上的mysql用户对应,以便标识
[root@C1 ~]# yum install -y mariadb mariadb-server
[root@C1 ~]# cp -p /etc/my.cnf.d/server.cnf{,.bak}
[root@C1 ~]# vim /etc/my.cnf
[mysqld]
datadir=/data/mysql
socket=/var/lib/mysql/mysql.sock
symbolic-links=0
skip_name_resolve = on
innodb_file_per_table = on
character-set-server = utf8
[mysqld_safe]
log-error=/var/log/mariadb/mariadb.log
pid-file=/var/run/mariadb/mariadb.pid
!includedir /etc/my.cnf.d
[root@C1 ~]# systemctl start mariadb.service #启动mariadb服务
[root@C1 ~]# ss -tnl | grep 3306
LISTEN 0 50 *:3306 *:*
[root@C1 ~]# mysql_secure_installation #初始化MariaDB数据库
[root@C1 ~]# mysql -uroot -p
MariaDB [(none)]> SHOW VARIABLES LIKE '%datadir%'; //检查数据文件的存储路径是否生效
+------------------------------+-----------------------------+
| Variable_name | Value |
+------------------------------+----------------------------+
| datadir | /data/mysql/ |
+------------------------------+-----------------------------+
1 row in set (0.00 sec) 3. 搭建FTP服务器
(1).安装vsftpd和pam_mysql:
[root@C1 ~]# yum --enablerepo=epel install vsftpd pam_mysql 编译安装pam_mysql:
下载pam_mysql源文件:pam_mysql-0.7RC1.tar.gz
[root@C1 tmp]# tar xf pam_mysql-0.7RC1.tar.gz -C /usr/local/src/
[root@C1 tmp]# cd /usr/local/src/pam_mysql-0.7RC1/
[root@C1 pam_mysql-0.7RC1]# yum install -y pam-devel.x86_64 mariadb-devel #在编译前确保已经安装了mariadb-devel、pam-devel.x86_64
[root@C1 pam_mysql-0.7RC1]# ./configure --with-pam-mods-dir=/usr/lib64/ #手工指定pam模块目录
[root@C1 pam_mysql-0.7RC1]# make && make install (2). 创建虚拟用户数据库.表,插入用户数据,并授权查询:
CREATE DATABASE vsftpd;
GRANT SELECT ON vsftpd.* TO 'vsftpd'@'192.168.1.%' IDENTIFIED BY 'vsftpdpass';
GRANT SELECT ON vsftpd.* TO 'vsftpd'@'localhost' IDENTIFIED BY 'vsftpdpass';
GRANT SELECT ON vsftpd.* TO 'vsftpd'@'127.0.0.1' IDENTIFIED BY 'vsftpdpass';
FLUSH PRIVILEGES;
USE vsftpd
CREATE TABLE `users` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`name` char(20) CHARACTER SET utf8 COLLATE utf8_bin NOT NULL,
`password` char(48) CHARACTER SET utf8 COLLATE utf8_bin NOT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8 #添加虚拟用户:
INSERT INTO users(name,password) VALUES('yinkai',password('yinkaipass')),('chris',password('chrispass')); (3). 配置vsftpd:
1) 建立pam认证所需文件:
[root@C1 ~]# vim /etc/pam.d/vsftpd.mysql
auth required /usr/lib64/pam_mysql.so user=vsftpd passwd=vsftpdpass host=localhost db=vsftpd table=users usercolumn=name passwdcolumn=password crypt=2
account required /usr/lib64/pam_mysql.so user=vsftpd passwd=vsftpdpass host=localhost db=vsftpd table=users usercolumn=name passwdcolumn=password crypt=2 说明:auth行用于认证,检查用户名和密码是否匹配;account行用于审查,检查用户是否在有效期限内
/usr/lib64/pam_mysql.so为pam_mysql的模块;user=vsftpd(登陆mysql数据库的用户名) passwd=www.magedu.com(登陆mysql数据库的密码) host=localhost(mysql数据库服务器主机) db=vsftpd(指定存储用户表的数据库) table=users(指定表) usercolumn=name(登陆vsftpd用户的用户名字段) passwdcolumn=password(登陆vsftpd用户的密码字段) crypt=2(密码使用MySQL PASSWORD()加密)
2) 建立虚拟用户映射的系统用户及对应的目录
[root@C1 ~]# useradd -s /sbin/nologin -d /var/ftp/ftproot vuser
[root@C1 ~]# chmod go+rx /var/ftp/ftproot/
[root@C1 ~]# chmod -w /var/ftp/ftproot/ #由于安全限制vsftpd不允许ftp用户根目录有写权限,否则登陆FTP服务器时会报:500 OOPS: vsftpd: refusing to run with writable root inside chroot()
[root@C1 ~]# mkdir /var/ftp/ftproot/test #创建一个可上传数据的目录
[root@C1 ~]# chown -R vuser.vuser /var/ftp/ftproot/test 3) 修改vsftpd的配置文件,使其使用mysql认证:
[root@C1 ftproot]# egrep -v '^#|^$' /etc/vsftpd/vsftpd.conf
anonymous_enable=YES
local_enable=YES
write_enable=YES
local_umask=022
anon_upload_enable=NO
anon_mkdir_write_enable=NO
anon_other_write_enable=NO
dirmessage_enable=YES
xferlog_enable=YES
connect_from_port_20=YES
xferlog_file=/var/log/xferlog
xferlog_std_format=YES
ftpd_banner=Welcome to blah FTP service.
chroot_local_user=YES
listen=NO
listen_ipv6=YES
pam_service_name=vsftpd.mysql
userlist_enable=YES
userlist_deny=YES
tcp_wrappers=YES
max_clients=200
anon_max_rate=5120
guest_enable=YES
guest_username=vuser
user_config_dir=/etc/vsftpd/vusers
[root@C1 ftproot]# cat /etc/vsftpd/vusers/yinkai
anon_upload_enable=YES
anon_mkdir_write_enable=YES
anon_other_write_enable=YES
[root@C1 ftproot]# cat /etc/vsftpd/vusers/chris
anon_upload_enable=YES
anon_mkdir_write_enable=YES
anon_other_write_enable=YES
测试:
yinkai@yinkai-NB-X230 ~ $ ftp 192.168.1.71
Connected to 192.168.1.71.
220 Welcome to blah FTP service.
Name (192.168.1.71:yinkai): chris #使用虚拟用户登陆
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> pwd
257 "/" #已禁锢用户
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw------- 1 1000 1000 1124 Nov 19 17:29 fstab
drwxr-xr-x 1 1000 1000 0 Nov 20 13:49 test
226 Directory send OK.
ftp> cd test
250 Directory successfully changed.
ftp> lcd /etc
Local directory now /etc
ftp> put issue
local: issue remote: issue
200 PORT command successful. Consider using PASV.
150 Ok to send data.
226 Transfer complete. #虚拟用户可上传数据
27 bytes sent in 0.00 secs (418.5 kB/s)
ftp> bye
221 Goodbye.
yinkai@yinkai-NB-X230 ~ $ ftp 192.168.1.71
Connected to 192.168.1.71.
220 Welcome to blah FTP service.
Name (192.168.1.71:yinkai): ftp #匿名用户登陆
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> pwd
257 "/" #已禁锢匿名用户
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
dr-xr-xr-x 1 1000 1000 98 Nov 20 13:44 ftproot
drwxrwxr-x 1 0 0 14 Nov 19 16:47 pub
-rw-r--r-- 1 0 0 0 Nov 19 16:49 tf1
226 Directory send OK.
ftp> mkdit testdir #匿名用户不可写
?Invalid command
ftp> get tf1
local: tf1 remote: tf1
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for tf1 (0 bytes).
226 Transfer complete.
ftp> bye
221 Goodbye. |
|