|
|
Step-by-step Forms-Based Authentication (FBA) on SharePoint 2010
Posted on August 25, 2011byMorgan
This is an A-Z guide that helps you setup a web application with Forms-Based Authentication (FBA) in SharePoint Foundation 2010, using Claims-Based authentication. It uses MS SQL Server to store users. The SharePoint server is running in Windows Server 2008R2. Although this guide uses SharePoint Foundation 2010, the same steps apply to SharePoint Server 2010.
In this guide, you’ll create a SQL Server database to hold users and roles, create a SharePoint Web Application that uses FBA, configure IIS and the web.config files for the Web App, Central Admin and the Security Token Service, create a test user in thedatabase and test your setup.
Contents
- Setting up the ASP.NET Membership Provider database
- Creating the Web Application
- Modify IIS settings
- Add ConnectionString and Providers to STS and Central Admin.
- Creating a test user
- Test in Central Administration
- Create Site Collection and test
Setting up the ASP.NET Membership Provider database
Before we make any changes to SharePoint, let’s first create the database to store our users and groups.
Log on to your SharePoint server with a SharePoint admin account. Make sure this account has theDB creator server role on the SQL server that’ll hold the FBA users DB.
Navigate to the .NET v2 folder. The default location is: C:\Windows\Microsoft.NET\Framework\v2.0.50727
Here, locate the file aspnet_regsql.exe and run it.
You’ll be presented with the ASP.NET SQL Server Setup Wizard.
Click Next to continue to the Select a Setup Option step.
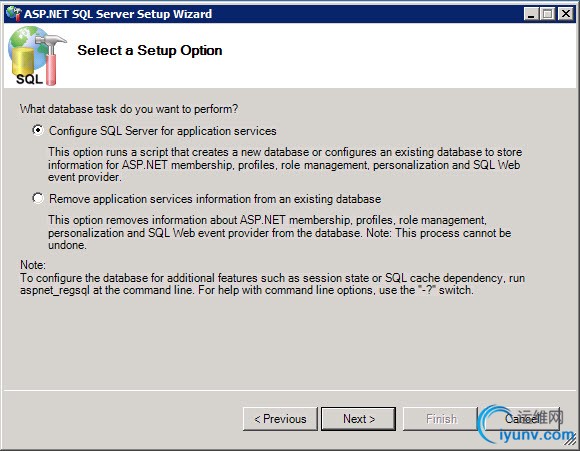
Select Configure SQL Server for application services. This is the default option.
Click Next to advance to the Select the Server and Database step.
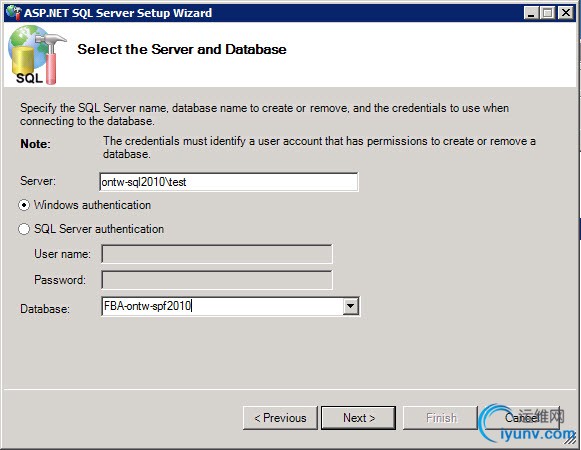
Specify the SQL Server name and instance where you want to create the database. Also specify the database name.
Click Next to advance to the Confirm Your Settings step.
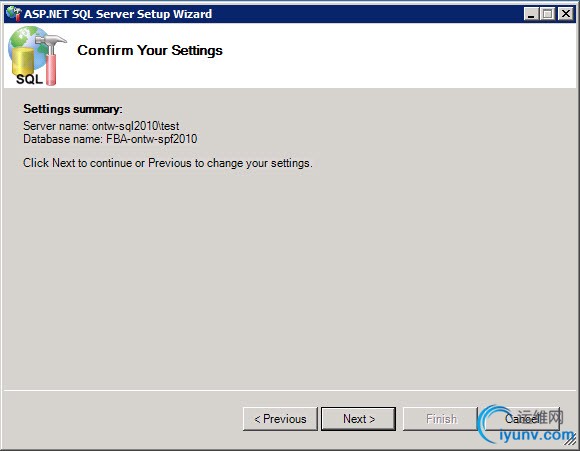
Check if you’ve specified the correct SQL Server name and instance and DB name. ClickNext to create the database.
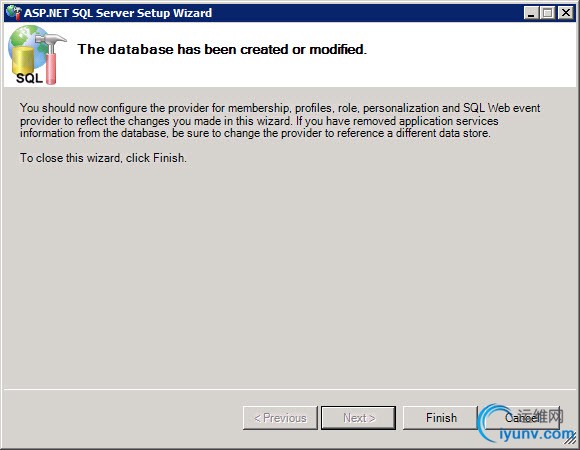
If all went well, you’ll see the success screen displayed above. Let’s check if the database was created as intended.
Start Microsoft SQL Server Management Studio and connect to the database server instance. If all went well, you’ll find your new database has been created, along with a bunch of tables to hold our users:
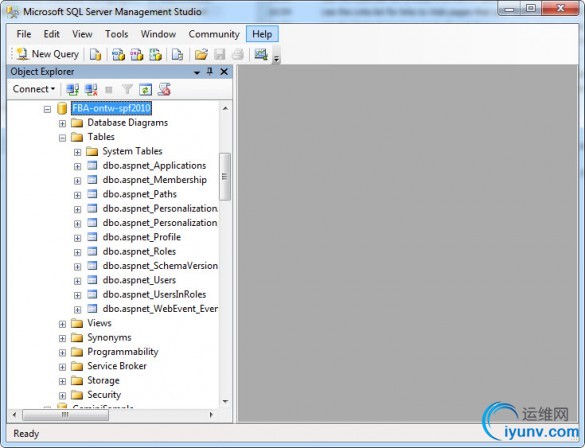
If you’re using Integrated Security, you’ll need to provide access to the database for the following service accounts in SharePoint:
- Service Account that’ll be used for the application pool for the SharePoint Web Application using FBA.
- Service Account used for the Security Token Service.
- Service Account used for the Application Pool of SharePoint Central Administration.
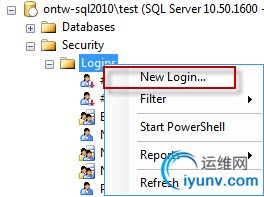 In this case, we’ll be using SQL Server authentication. So create a new Login on the SQL Server.From SQL Server Management Studio, use the Object Explorer to navigate to the Security → Logins folder. Right click on the Logins folder to open the context menu and choose the menu itemNew Login…
In this case, we’ll be using SQL Server authentication. So create a new Login on the SQL Server.From SQL Server Management Studio, use the Object Explorer to navigate to the Security → Logins folder. Right click on the Logins folder to open the context menu and choose the menu itemNew Login…
This will open the Login – New dialog. Here, you specify a Login name, i.e. FBAService and a SQL Server authentication password, i.e. pwd. You can set your membership provider database as the Default database. ClickOK to add the user. It will now show up in the list of logins.
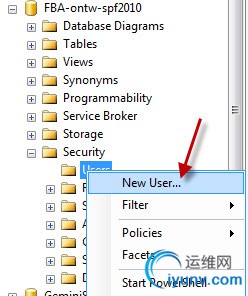 To give the login access to the database, locate the database in the ObjectExplorer, under the Databases folder and expand the folder Security. Open the context menu from theUsers folder and choose the optionNew User…
To give the login access to the database, locate the database in the ObjectExplorer, under the Databases folder and expand the folder Security. Open the context menu from theUsers folder and choose the optionNew User…
This opens the Database User – New dialog.
In this dialog, specify a name for the user and insert the login name that you created earlier (i.e.FBAService) in the Login name text field.
Assign the following Database roles to the user:
- aspnet_Membership_FullAccess
- aspnet_Roles_FullAccess
Click the OK button to add the user to the database.
Creating the Web Application
Now that the DB has been created, we’ll create a new Web Application on the SharePoint 2010 server.
Open Central Administration as a SharePoint Farm administrator user.
Under Application Management, select Manage Web Applications.
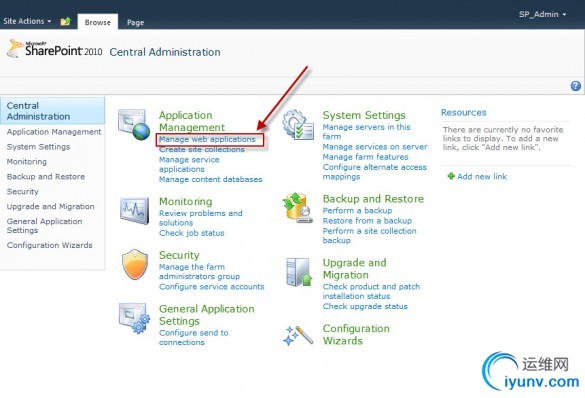
You’ll see a list of current Web Applications, Click the New button in the Contribute section of the Ribbon to create a new Web Application.
After a few seconds, you’ll see the Create New Web Application Modal window.
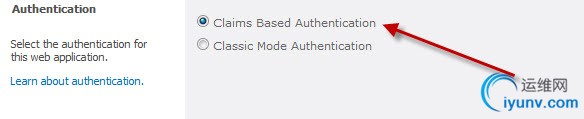
First, change the authentication mode to Claims Based Authentication.
Next, Specify the Name, Port and Host Header of your new IIS web site.
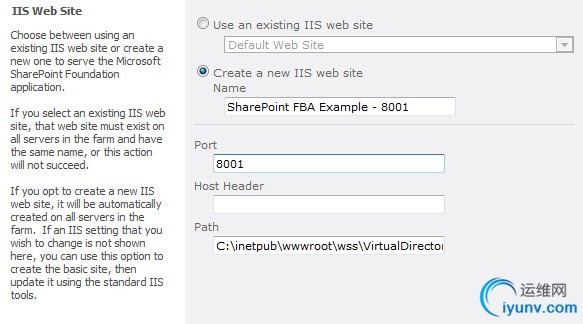
Leave the Security Configuration settings as default (no anonymous and no SSL).
Under Claims Authentication Types, leave the default settings for now (Enable Windows Authentication, using Integrated Windows Authentication via NTLM). We’ll modify these settings for FBA later.
Set the remaining settings for the new Web Application as you see fit.
Click OK button to create the new Web Application. Wait a few moments until the Application Created dialog is shown, and click theOK button to close it (don’t create a site collection just yet). The new Web Application willnow show up in the list of Web Applications.
Modify IIS settings
In your SharePoint 2010 Foundation server, start Internet Information Services (IIS) Manager.
Under your Web Server, navigate to the IIS site that we created in the previous step anddouble click on Connection Strings
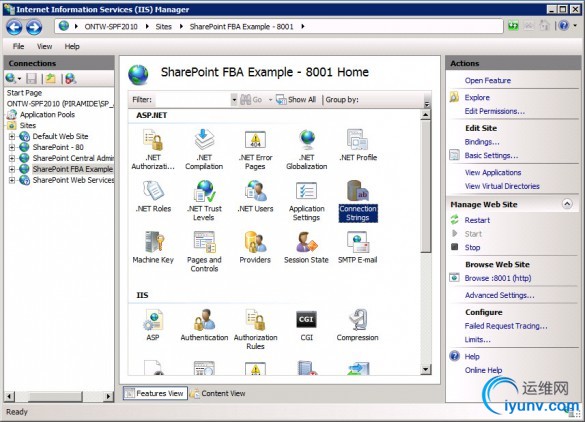
You’ll see a list of Connection Strings. In the Actions Pane, click Add…This opens the Add Connection String dialog.
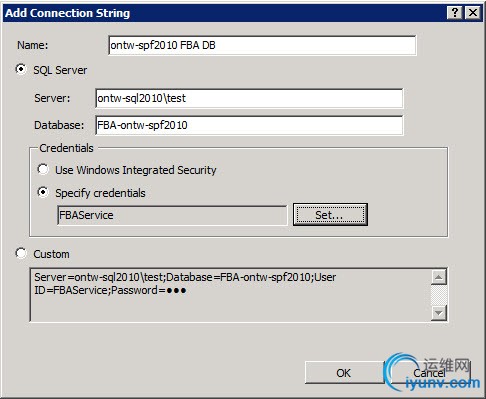
Here, specify a name for the connection string and give the SQL Server name and instance, and database name of the DB that we created earlier. Use theSet… button to specify the SQL Server authentication credentials for the SQL Server userthat will access the database.
Click the OK button to add the connection string.
Go back to the IIS site screen and double click Providers.
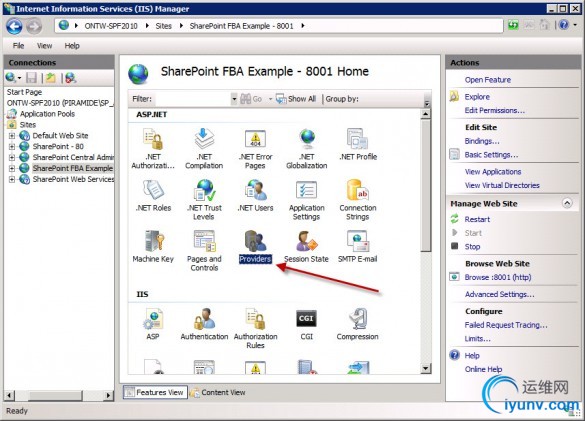
Under Feature:, select .NET Users and in the Actions Pane, click Add…
The Add Provider window opens…
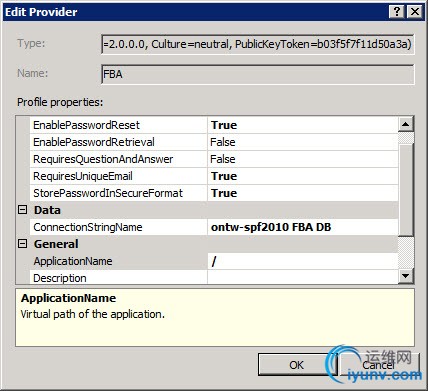
Here, we’ll modify a few settings:
- First of all, select SqlMembershipProvider from the Type dropdown listbox.
- Next, specify a name for the Provider, i.e. “FBA”.
- Under the Behaviour section, specify the desired behaviour for the SqlMembershipProvider.
- Under Data, select the Connectionstring we created in an earlier step.
- For the ApplicationName, enter “/”.
Click the OK button to add the provider. The new .NET Users provider will be visible in the list of Providers.
Now, Change the feature to .NET Roles and in the Action pane, clickAdd…
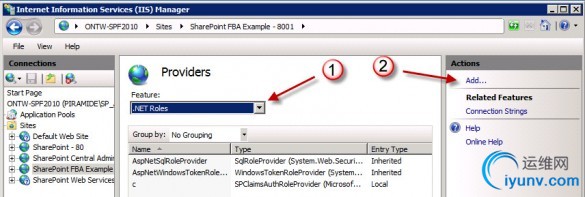
The Add Provider window opens…
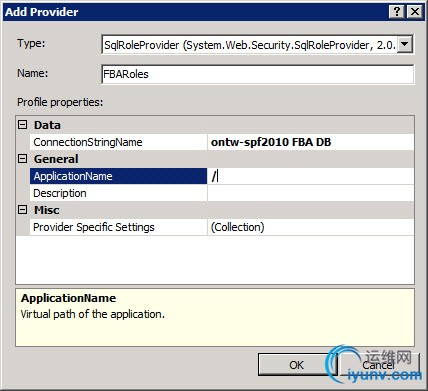
Here, set the following items:
- Under Type, select SqlRoleProvider
- Specify a name for the SqlRoleProvider, i.e. “FBARoles”
- Under Data, select the Connectionstring we created in an earlier step.
- For the ApplicationName, enter “/”.
Click the OK button to add the provider. The new .NET Roles provider will be visible in the list of Providers.
The changes we’ve made to the IIS settings so far, have actually been made in the ASP.NET Web.Config file.
In the IIS Manager, Switch to Content View, Open the Context menuby clicking below the list of files and folders andchoose Explore to open Windows Explorer.
From the new Windows Explorer window, open the web.config file in Notepad to view the changes.
The highlighted rows were added with our previous actions:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| <configuration>
[...]
<system.web>
[...]
<membershipdefaultProvider="i">
<providers>
<add name="i" type="Microsoft.SharePoint.Administration.Claims.SPClaimsAuthMembershipProvider, Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c"/>
<addname="FBA"type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a"connectionStringName="ontw-spf2010FBA DB"enablePasswordReset="true"enablePasswordRetrieval="false"passwordFormat="Hashed"requiresQuestionAndAnswer="false"requiresUniqueEmail="true"applicationName="/"/>
</providers>
</membership>
<roleManagerdefaultProvider="c"enabled="true"cacheRolesInCookie="false">
<providers>
<add name="c" type="Microsoft.SharePoint.Administration.Claims.SPClaimsAuthRoleProvider, Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c"/>
<addname="FBARoles"type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0,Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a"connectionStringName="ontw-spf2010 FBA DB"applicationName="/"/>
</providers>
</roleManager>
[...]
</system.web>
[...]
<connectionStrings>
<addconnectionString="Server=ontw-sql2010\test;Database=FBA-ontw-spf2010;User ID=FBAService;Password=pwd"name="ontw-spf2010FBA DB"/>
</connectionStrings>
[...]
</configuration>
|
As you can see, there are also other providers there, named ”i” and “c”. These are there by default and required for Claims Based Authentication.Be sure not to modify them!
The membershipprovider also supports additional settings, such as the minimum required password length and number of non-alphanumeric characters required in a password. For a full list of properties that can be set, seehttp://msdn.microsoft.com/en-us/library/9x1zytyd(v=VS.90).aspx
Add ConnectionString and Providers to STS and Central Admin.
In order for FBA to work, the ConnectionString, .NET Roles provider and .NET Users provider also need to be added to the web.config files of the Security Token Service and the web.config file of the Central Administration Web Application.
We could do this using the dialogs we used from the previous steps, but we can also make the changes in the web.config files directly.
First up: the Security Token Service.
From the IIS Manager, locate the web.config file location by following these steps:
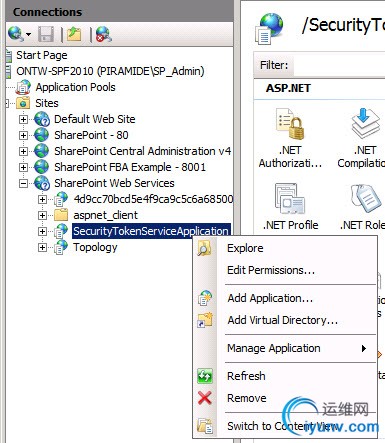
Under the SharePoint Web Services IIS site, Select SecurityTokenServiceApplication, open the context menu by right-clicking the SecurityTokenServiceApplication node and chooseExplore.
This will open a Windows Explorer dialog with the location of the STS web.config file. The default location is C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\14\WebServices\SecurityToken.
Open the web.config in a text editor, like Notepad and make the following changes:
In the <configuration> section, see if there is a <connectionStrings> element present. If not, add a <connectionStrings> element. Next, add the element containing the connection string to the FBA database as highlighted in the Web App’s web.config file above,i.e.:
1
2
3
| <connectionStrings>
<addconnectionString="Server=ontw-sql2010\test;Database=FBA-ontw-spf2010;UserID=FBAService;Password=pwd"name="ontw-spf2010 FBA DB"/>
</connectionStrings>
|
Next, check if there is a <system.web> element, with <membership> and <roleManager> elements present in the web.config, and add it if not, add them. Now add the membership and role manager providers, as highlighted in the Web App’s web.config snippet, i.e.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| <system.web>
<membershipdefaultProvider="FBA">
<providers>
<addname="FBA"
type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a"
connectionStringName="ontw-spf2010 FBA DB"
enablePasswordReset="true"
enablePasswordRetrieval="false"
passwordFormat="Hashed"
requiresQuestionAndAnswer="false"
requiresUniqueEmail="true"
applicationName="/"/>
</providers>
</membership>
<roleManagerenabled="true"defaultProvider="FBARoles">
<providers>
<addname="FBARoles"
type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a"
connectionStringName="ontw-spf2010 FBA DB"
applicationName="/"/>
</providers>
</roleManager>
</system.web>
|
Save your changes to the web.config file.
Return to IIS Manager and locate the web.config file for Central Administration:
Select the SharePoint Central Administration v4 IIS site from the list of sites,open the context menu for this site and chooseExplore.
From the Windows Explorer window, open the web.config file in a text editor like Notepad.
Here, also add the ConnectionString snippet to the <configuration> section and add the .NET Users and .NET Roles providers, just like you did for the STS site.
Note: the Central Admin’s web.config should already contain the <roleManager> and <membership> elements in <system.web>. Be sure not to modify any existing providers.
Important: the default provider for the roleManager must be set to “AspNetWindowsTokenRoleProvider”. (also see the highlighted row below)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| <membershipdefaultProvider="FBA">
<providers>
<addname="FBA"
type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral,PublicKeyToken=b03f5f7f11d50a3a"
connectionStringName="ontw-spf2010 FBA DB"
enablePasswordReset="true"
enablePasswordRetrieval="false"
passwordFormat="Hashed"
requiresQuestionAndAnswer="false"
requiresUniqueEmail="true"
applicationName="/"/>
</providers>
</membership>
<roleManagerenabled="true"defaultProvider="AspNetWindowsTokenRoleProvider">
<providers>
<addname="FBARoles"
type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a"
connectionStringName="ontw-spf2010 FBA DB"
applicationName="/"/>
</providers>
</roleManager>
|
To enable wildcards in the people picker, locate the <PeoplePickerWildCards> element (inside the <SharePoint> element), andadd a key with the name of your Membership provider and value “%”. It will look like this (the highlighted line isthe key we added):
1
2
3
4
5
| <PeoplePickerWildcards>
<clear/>
<addkey="AspNetSqlMembershipProvider"value="%"/>
<add key="FBA" value="%" />
</PeoplePickerWildcards>
|
Creating a test user
It’s hard to test FBA if you don’t have any users, so we’ll add a test user first. One way of doing this is via the IIS manager.
First, we add a role to assign to the users. In IIS Manager, select the Web Application that will use FBA and from the Features View, double click on .NET Roles.
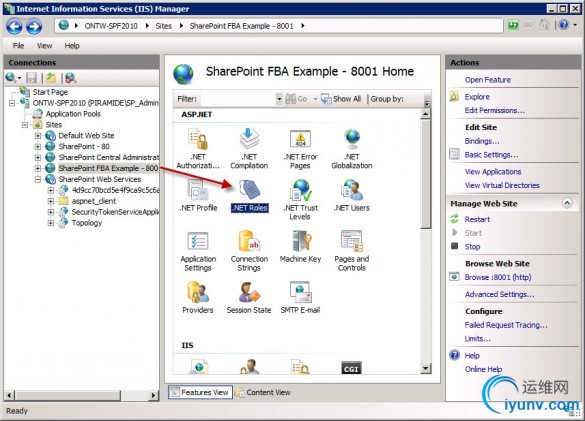
You’ll receive an error message, saying the the feature cannot be used, because the default provider is not a trusted provider. The default provider is “c”, which is the SPClaimsAuthRoleProvider. Click on theOKbutton to close the dialog.
We’ll temporarily set the default provider to our FBARoles provider. Click Set Default Provider… from in the actions pane andselect the RoleProvider you created earlier (i.e.FBARoles). Click theOK button.
Click the Add… link in the Actions pane. In the Add .NET Role dialog, enter a name for a role, i.e.FBAUsers. Click theOK button to add the role. The new role is now visible, with 0 users.
We’ll leave the default roles provider this way for now, otherwise we’d not be able to add a .NET user via IIS Manager.
Now, let’s add a user. Go back in IIS Manager to the Features View for your Web Application and double click on .NET Users.
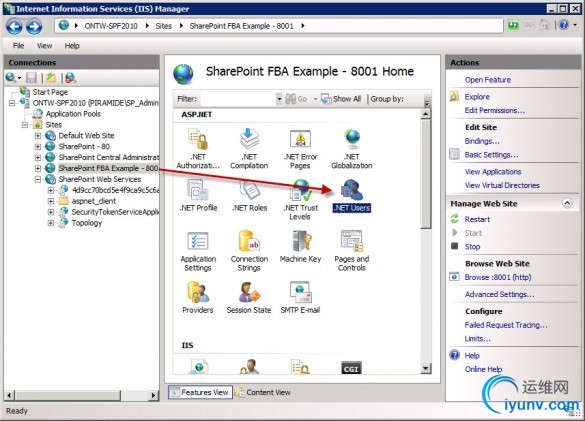
You’ll receive a similar error message, because the default provider (“i”) is not trusted. Click theOK button to ignore.
Now click the Set Default Provider… link in the Actions pane and change the default provider to the Membership Provider you created earlier (i.e.FBA).
Click the Add… link in the actions Pane, to add a new user.
The Add .NET User wizard appears. Enter the credentials for your test user (i.e. a User NameFBAtest). ClickNext to advance to the next step.
Now assign a role to the new user by clicking the checkbox(es) for the role(s). ClickFinish to add the user.
Important:Return the Default Provider for the .NET users to “i” and for the .NET Roles to “c”.
Test in Central Administration
Now that we have the membership and roles provider set up in the Web Application, Central Admin and STS, we can test if it works.
In Central Administration, go to Application Management → Manage web applications.
Select the Web Application you created earlier by clicking on it in the list. Its row will highlight Now click theAuthentication Providers button.
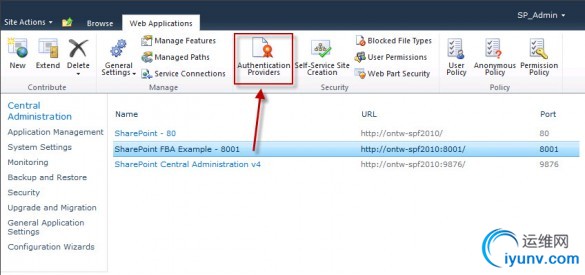 The Authentication Providers modal dialog will open. Click on the Default zone.
The Authentication Providers modal dialog will open. Click on the Default zone.
Scroll down to the Claims Authentication Types section. Here,deselect Enable Windows Authenticationand select Enable Forms Based Authentication (FBA).
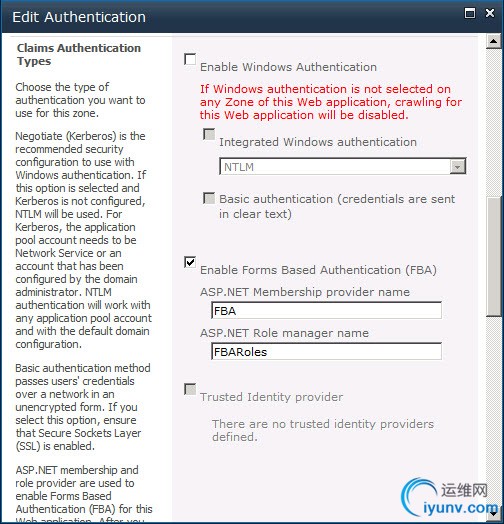
Fill the ASP.NET Membership provider and ASP.NET Role manager names text boxes, with the names you defined earlier (i.e. FBA and FBARoles).
Note: you can also use both Windows Authentication and FBA simultaneously, should you want to.
Leave the other settings and scroll down to click the Save button.
After a few seconds, you’ll see the Authentication Providers modal dialog again. Close the dialog. You’ll return to the Web Applications list.
With the FBA Web Application still selected, click the User Policy button in the ribbon.
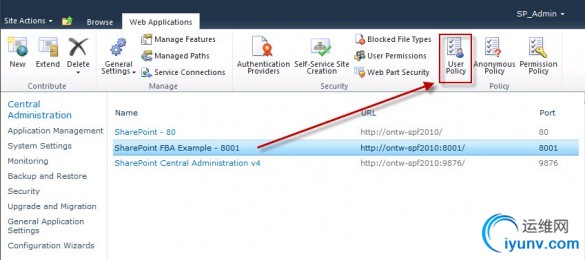
The Policy for Web Application modal dialog opens. Click on the Add Users link.
The Add Users wizard opens, click Next >.
In the next page, the cursor will show up in the people picker field. Click theBrowse button to open the Select People and Groups dialog.
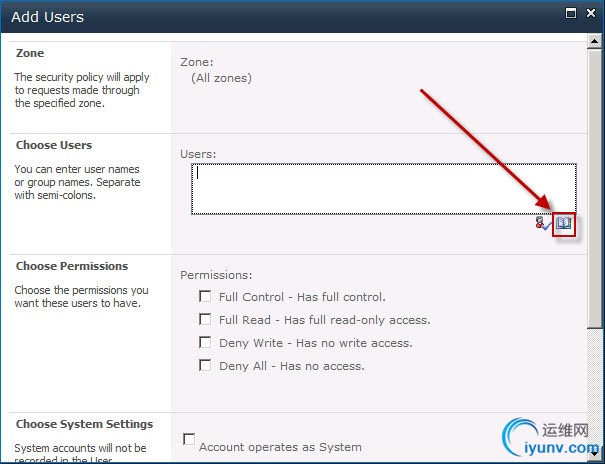
In the select People and Groups dialog, type (a part of) the name of the FBA test user you added from IIS Manager in the Find text box and press the search button. You should find the user in the Forms Auth search results.
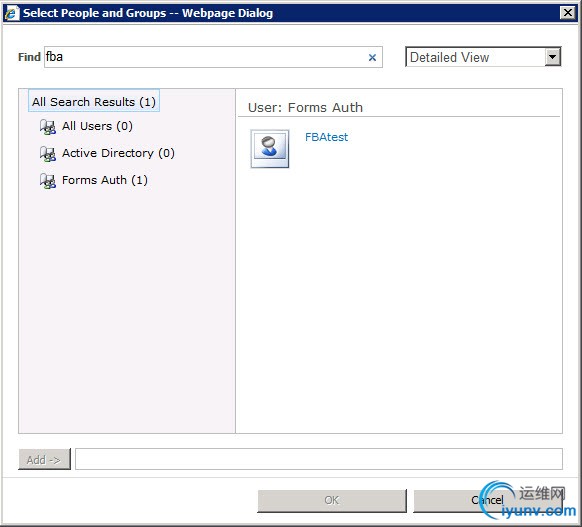
This verifies that the FBA membership provider works from Central Admin. As we don’t want to add this user, press theCancelbutton and Close the Add Users dialog.
Create Site Collection and test
So far, we only created and configured the Web Application. To test FBA in the SharePoint site, we need to create a site collection.
In Central Administration, go to Application Management → Create site collections.
Make sure you select the right Web Application, and specify a Title and Template for the top-level site.
Select a Primary Site Collection Administrator, i.e. the FBA user you created earlier.
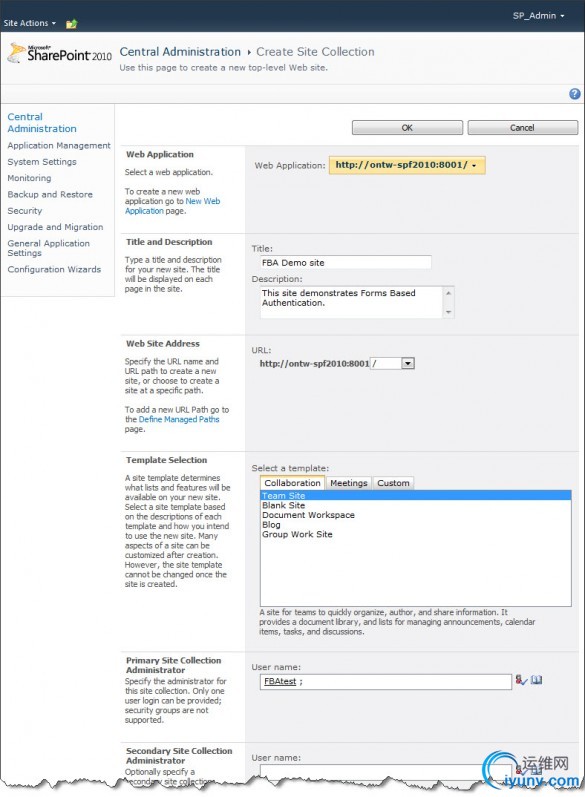
Click the OK button to create the site collection.
Now navigate to the newly created Site Collection. You’ll see a login page for the FBA credentials.
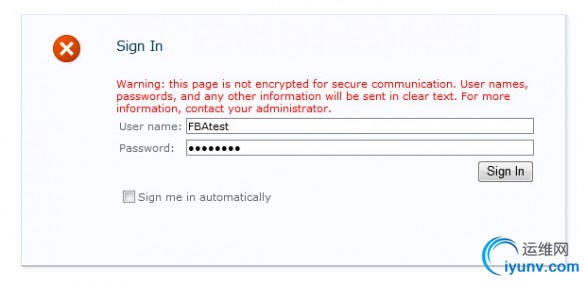 Note:if you chose to use multiple authentication methods for the Web Application’s Authentication Providers, you’ll be asked to select an authentication method from a dropdown listbox first.
Note:if you chose to use multiple authentication methods for the Web Application’s Authentication Providers, you’ll be asked to select an authentication method from a dropdown listbox first.
Sign in the the FBA user you declared as the Site Collection Administrator.
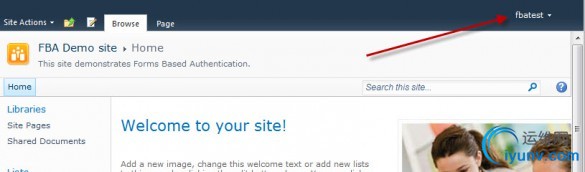
If all went well, you’ll see the name of the FBA user in the upper right corner! |
|