一.apache的定义:企业中常用的web服务,用来提供http://(超文本传输协议)
二.apache的安装部署
#安装(配置好yum源)
yum install httpd -y

yum install httpd-manual

systemctl start httpd

systemctl enable httpd

systemctl stop firewalld.service

systemctl disable firewalld.service

测试: http://172.25.254.160/
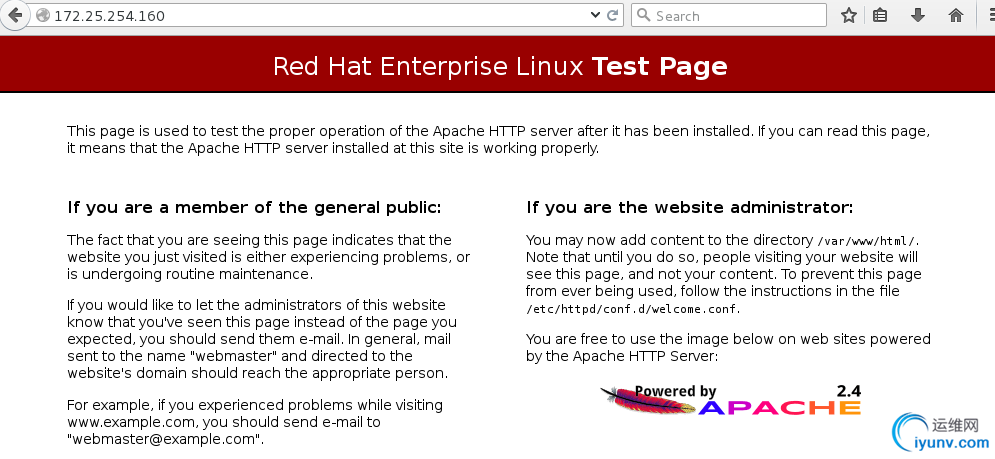
http://172.25.254.160/manual/

三.apache的基本信息
主配置目录: /etc/httpd/conf
主配置文件: /etc/httpd/conf/httpd.conf
子配置目录: /etc/httpd/conf.d/
子配置文件: /etc/httpd/conf.d/.conf
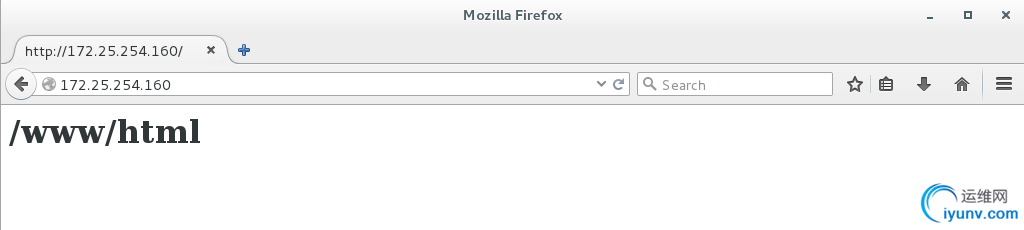
默认发布目录: /var/www/html
默认发布文件: index.html
默认端口: 80
默认安全上下文:httpd_sys_content_t
程序开启默认用户:apache
apache日志: /etc/httpd/logs/
查看安全上下文: ls -Z /var/www/

查看端口:ss -anutlpe | grep httpd
默认端口为80
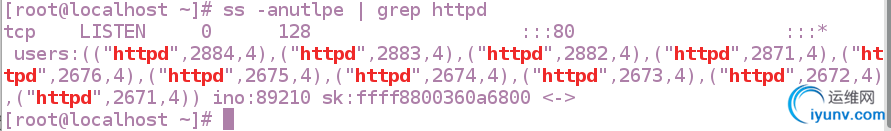
修改默认端口:
vim /etc/httpd/conf/httpd.conf
42 Listen 80 ##修改默认端口为8080


重启服务

修改后的端口为8080
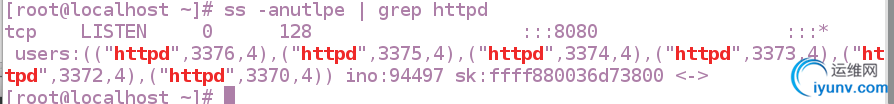
改回默认端口:80
修改配置文件vim /etc/httpd/conf/httpd.conf
42 Listen 80

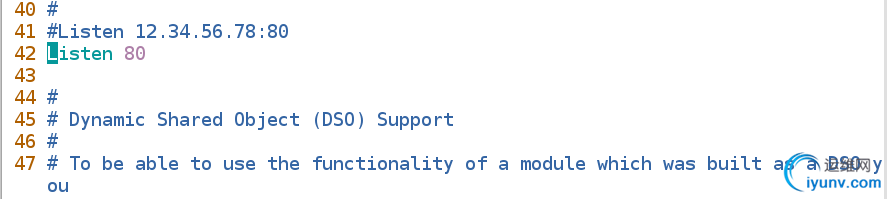
重启服务

查看端口信息80
修改默认发布文件:
120 DocumentRoot "/www/html"
121
122 Require all granted
123

cd /var/www/html
编辑默认发布目录vim index.html


测试:
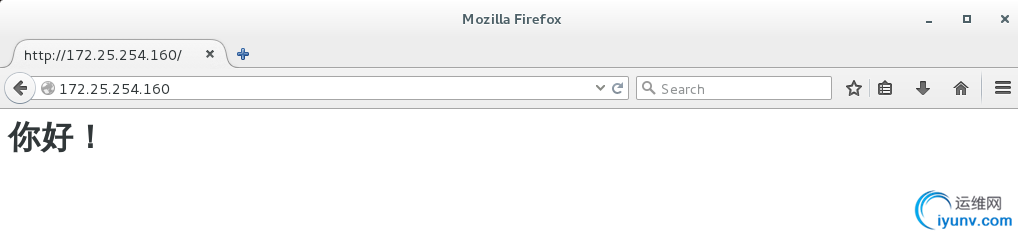
把默认发布目录名称修改不能访问

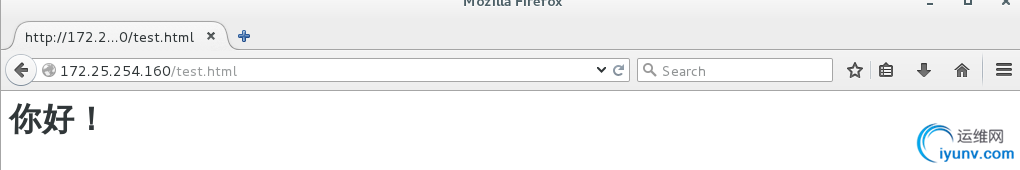
加上文件名才可访问
在配置文件中写入,当默认目录为空时即访问

配置文件中将默认目录在前,默认先访问前面的内容
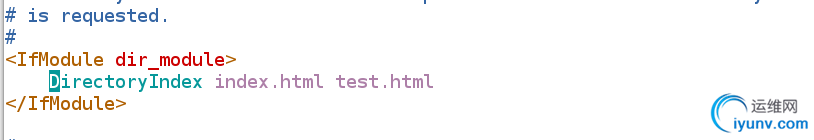



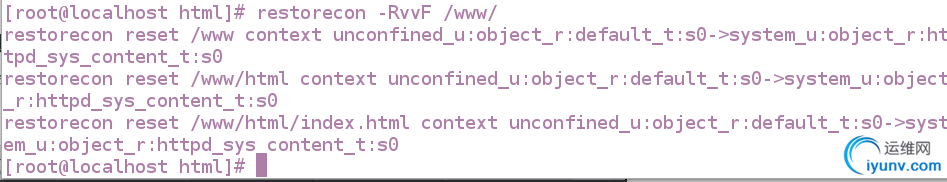
semanage fcontext -a -t httpd_sys_content_t '/www(/.*)?' ##更改安全下文
restorecon -RvvF /www/ ##刷新

测试:
四.apache的虚拟主机
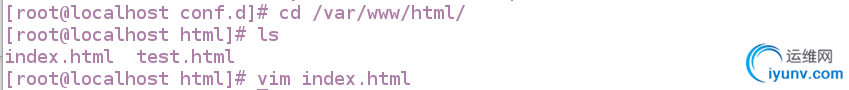
[root@localhost conf.d]# cd /var/www/html/
[root@localhost html]# ls
index.html test.html
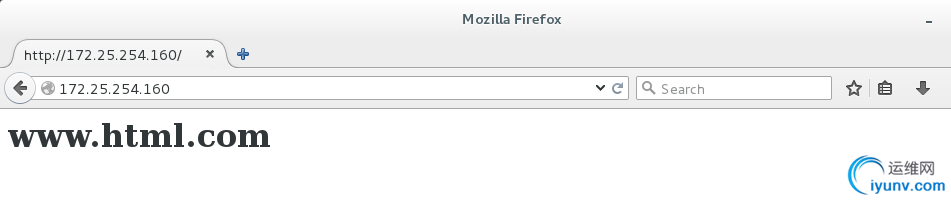
[root@localhost html]# vim index.html
www.html.com
[root@localhost html]# mkdir /var/www/virtual/linux1.html.com/html -p
[root@localhost html]# mkdir /var/www/virtual/linux2.html.com/html -p
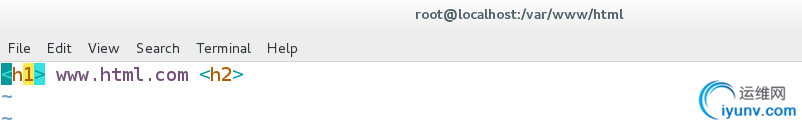
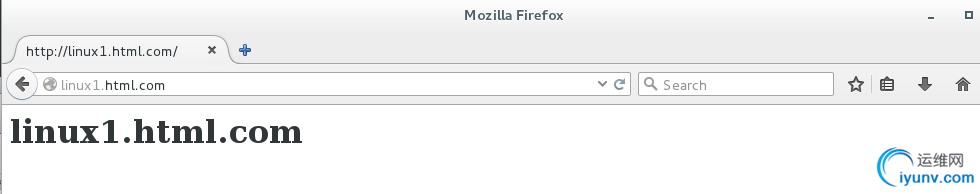
vim /var/www/virtual/linux1.html.com/html/index.html
linux1.html.com
vim /var/www/virtual/linux1.html.com/html/index.html
linux1.html.com
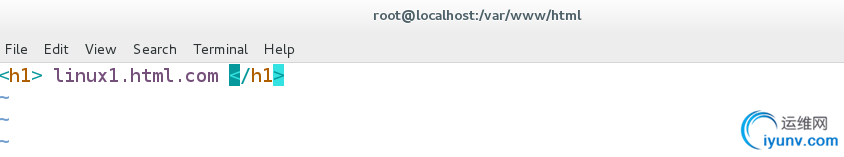
[root@localhost html]# mkdir /var/www/virtual/linux1.html.com/html -p
[root@localhost html]# mkdir /var/www/virtual/linux2.html.com/html -p

vim /var/www/virtual/linux1.html.com/html/index.html
linux1.html.com

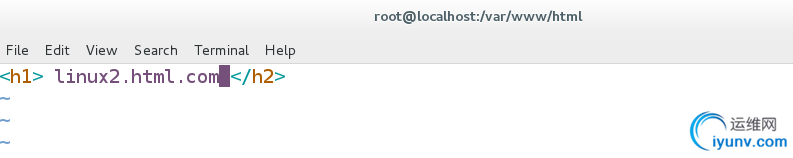
vim /var/www/virtual/linux2.html.com/html/index.html
linux2.html.com

[root@localhost conf.d]# vim /etc/httpd/conf.d/adefault.conf
DocumentRoot "/var/www/html"
CustomLog "logs/www.html.com.log" combined

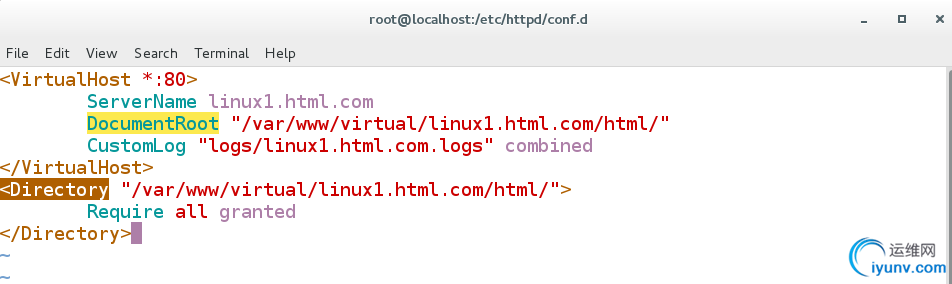
[root@localhost conf.d]#vim /etc/httpd/conf.d/linux1.conf
ServerName linux1.html.com #指定站点名称
DocumentRoot "/var/www/virtual/linux1.html.com/html/" #站点默认发布目录
CustomLog "logs/linux1.html.com.logs" combined
Require all granted

[root@localhost conf.d]# vim /etc/httpd/conf.d/linux2.conf
ServerName linux2.html.com
DocumentRoot "/var/www/virtual/linux2.html.com/html/"
CustomLog "logs/linux2.html.com.logs" combined
Require all granted


测试:
在测试机中做好本地解析
vim /etc/hosts
172.25.254.160 linux1.html.com linux2.html.com www.html.com html.com


测试:

五.apache的内部访问控制
1.针对与主机的访问
2.[root@localhost conf.d]# mkdir /var/www/html/test
[root@localhost conf.d]# vim /var/www/html/test/index.html
hello world

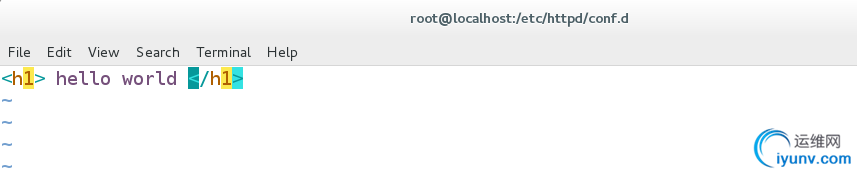
测试:
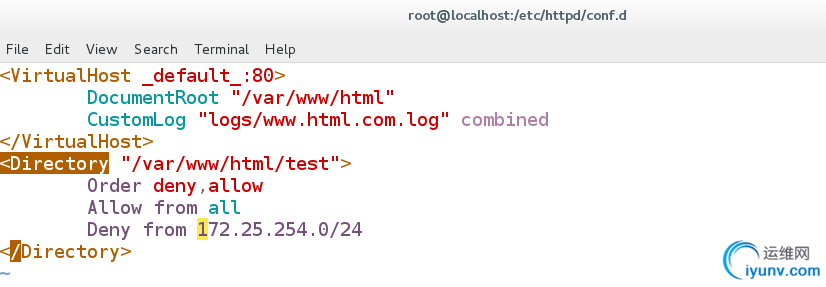
[root@localhost conf.d]# vim default.conf
DocumentRoot "/var/www/html"
CustomLog "logs/www.html.com.log" combined
Order deny,allow
Allow from all ##列表读取顺序,后读取的内容会覆盖先读取内容的重复部分
Deny from 172.25.254.0/24

[root@localhost conf.d]# systemctl restart httpd.service

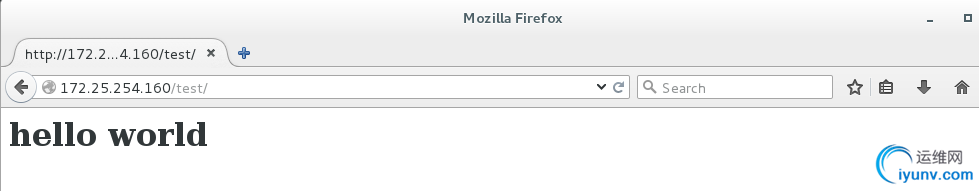
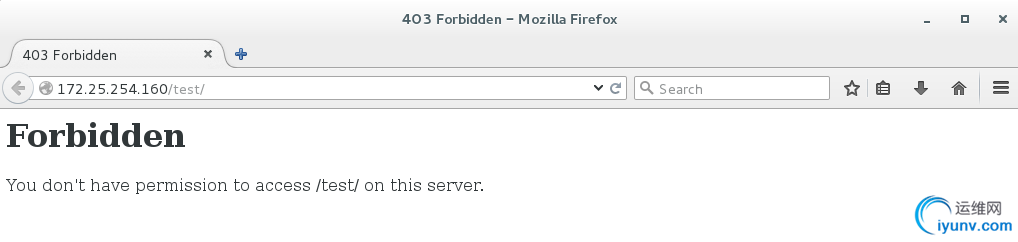
测试:
拒绝172.25.254.0/24
2.用户方式的访问控制
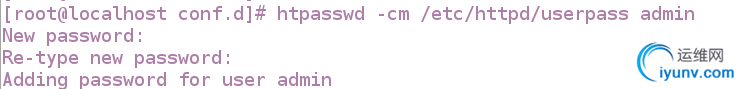
[root@localhost conf.d]# htpasswd -cm /etc/httpd/userpass admin
New password:
Re-type new password:
Adding password for user admin
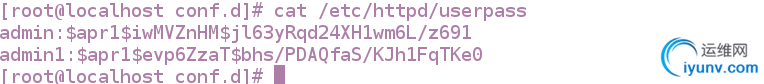
[root@localhost conf.d]# cat /etc/httpd/userpass

[root@localhost conf.d]# htpasswd -m /etc/httpd/userpass admin1#再次添加用户时,去掉c
New password:
Re-type new password:
Adding password for user admin1

[root@localhost conf.d]# cat /etc/httpd/userpass
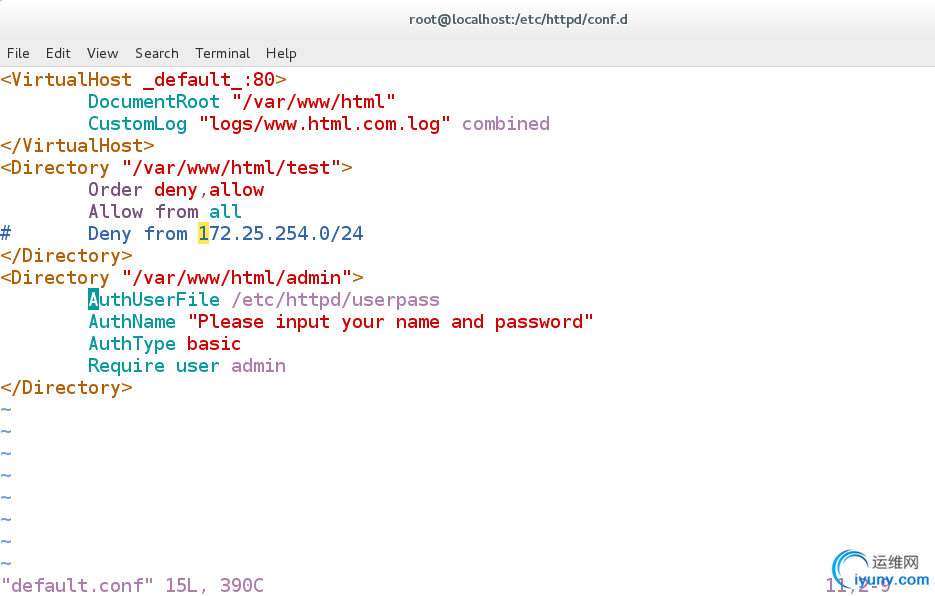
[root@localhost conf.d]# vim default.conf
rectory "/var/www/html/admin">
AuthUserFile /etc/httpd/userpass
AuthName "Please input your name and password"
AuthType basic
Require user admin
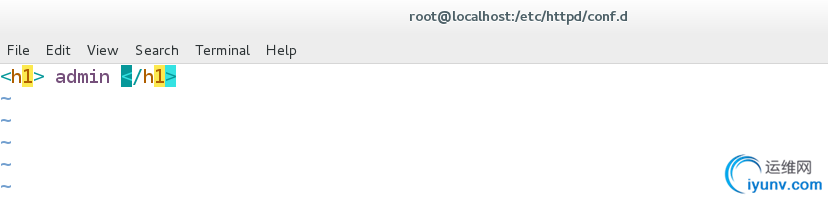
[root@localhost conf.d]# mkdir /var/www/html/admin
[root@localhost conf.d]# vim /var/www/html/admin/index.html
admin

[root@localhost conf.d]# systemctl restart httpd.service
测试:
需要输入密码
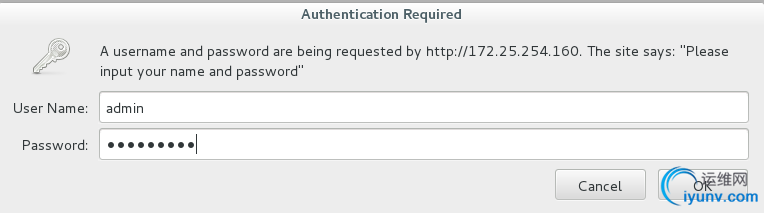
输入密码正确后

[root@localhost conf.d]# vim default.conf
AuthUserFile /etc/httpd/userpass
AuthName "Please input your name and password"
AuthType basic
#Require user admin
Require valid-user
#

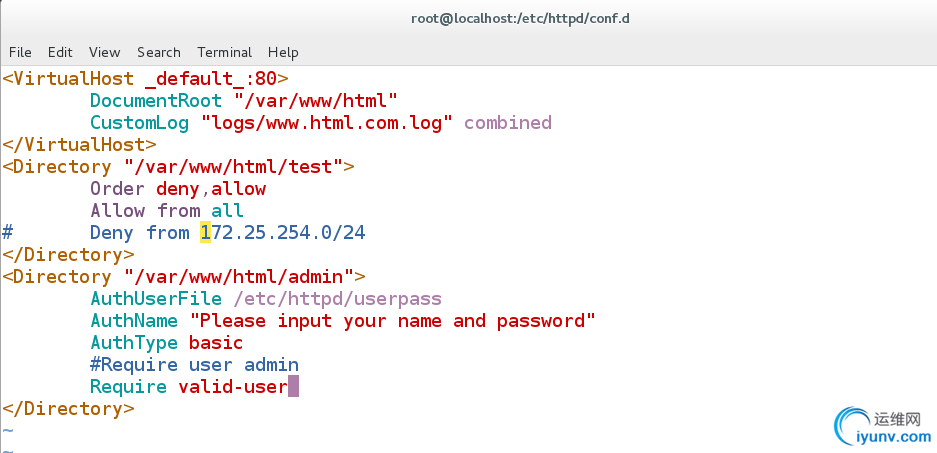
[root@localhost conf.d]# systemctl restart httpd.service

六。apache支持的语言
1.html
2.php
[root@localhost html]# vim index.php

[root@localhost conf.d]# systemctl restart httpd.service

[root@localhost html]# vim /etc/httpd/conf/httpd.conf
163 DirectoryIndex index.php index.html test.html
测试:
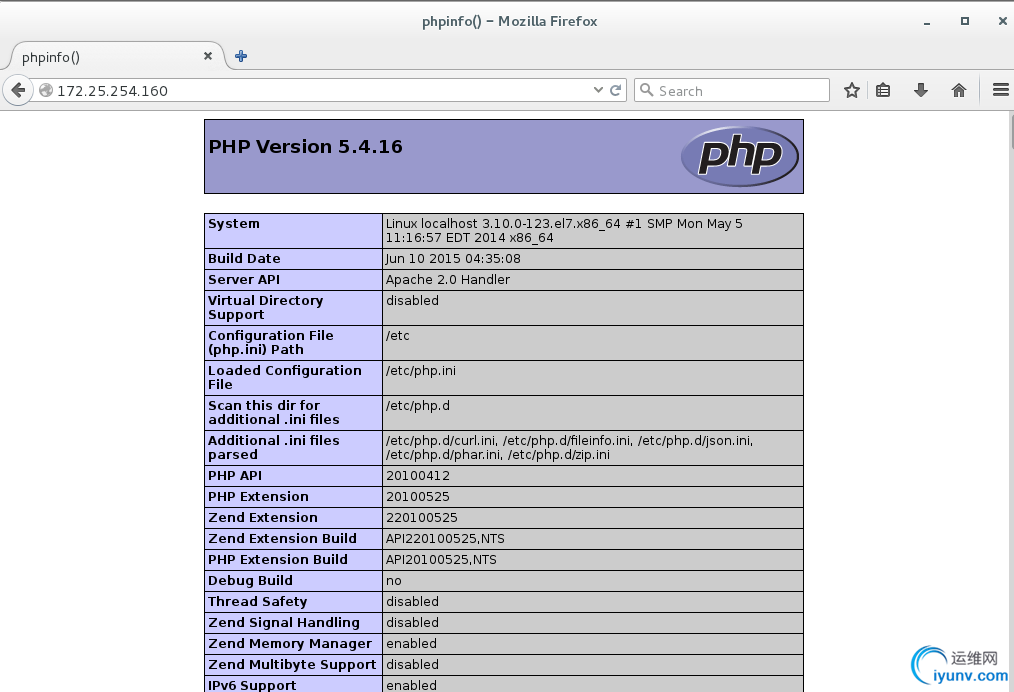
3.cgi
安装的manual里面有cgi语言的模板
[root@localhost cgi]# vim index.cgi
#!/usr/bin/perl
#print "Content-type: text/html\n\n";
#print "date";

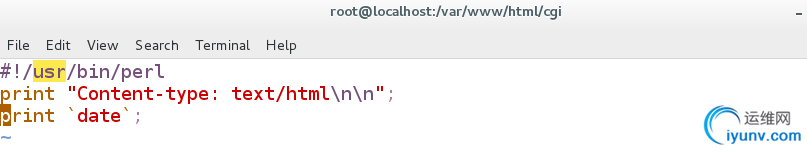
给该目录加上可执行权限

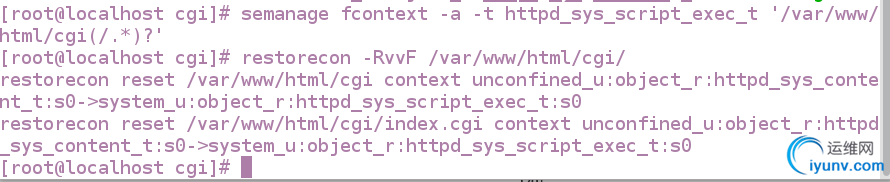
[root@localhost cgi]# semanage fcontext -a -t httpd_sys_script_exec_t '/var/www/html/cgi(/.*)?' #更改安全上下文
[root@localhost cgi]# restorecon -RvvF /var/www/html/cgi/
[root@localhost conf.d]# vim default.conf
Options +ExecCGI
AddHandler cgi-script .cgi


[root@localhost conf.d]# systemctl restart httpd.service
测试:
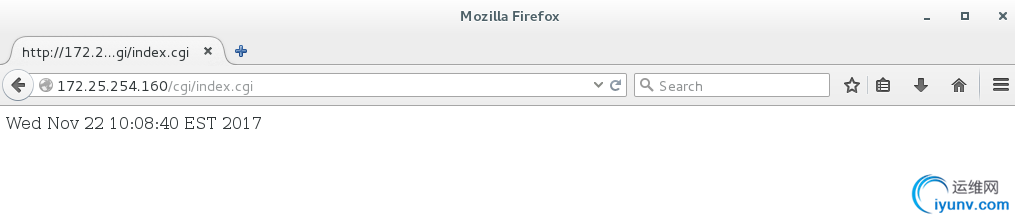
七.https
[root@localhost conf.d]# yum install mod_ssl.x86_64
[root@localhost conf.d]# yum install crypto-utils.x86_64



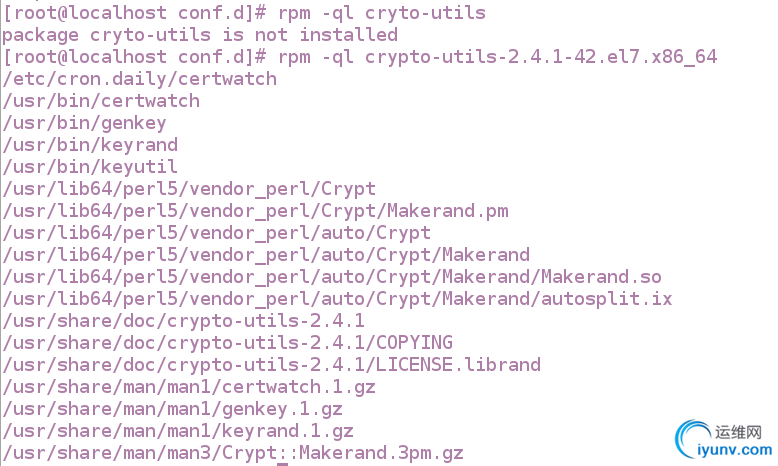
查看安装过程中生成了什么文件
rpm -ql crypto-utils.x86_64
生成认证genkey www.westos.com

next
选择1024字节,加密方式
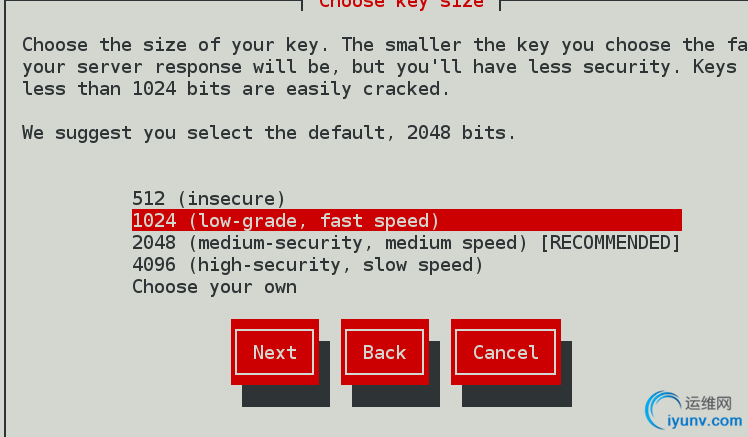
填写先关信息获得认证
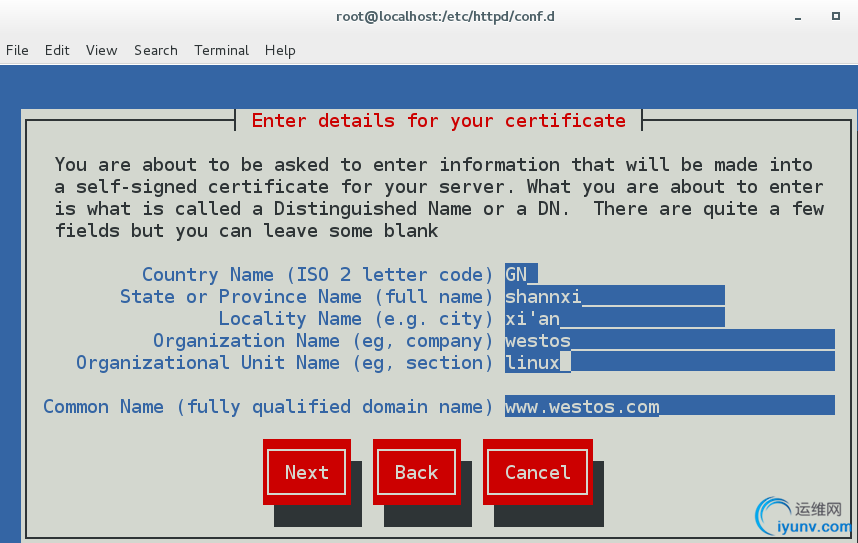
生成密钥
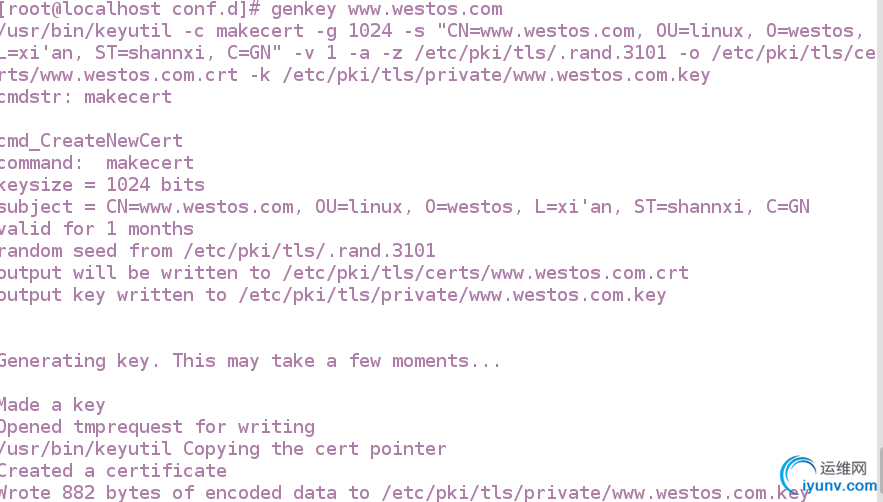
加密字符
http://i2.51cto.com/images/blog/201711/23/e04162df3295549818e6d8de57885101.png
http://i2.51cto.com/images/blog/201711/23/7b56e2e8564d97a6033254b99dab5a31.png
vim /etc/httpd/conf.d/ssl.conf
101 SSLCertificateFile /etc/pki/tls/certs/www.westos.com.crt
108 SSLCertificatekey:wq
File /etc/pki/tls/private/www.westos.com.key
http://i2.51cto.com/images/blog/201711/23/319469816355af41d3f06f55cc2e26cd.png
把刚才获得的认证写入配置文件
http://i2.51cto.com/images/blog/201711/23/367c6e45471f00614b2290b986691bfb.png
[root@localhost conf.d]# mkdir -p /var/www/html/virtual/login.html.com/html
[root@localhost conf.d]# vim /var/www/html/virtual/login.html.com/html/index.html
[root@localhost conf.d]# vim /etc/httpd/conf.d/login.conf
ServerName login.html.com
DocumentRoot /var/www/html/virtual/login.html.com/html
CustomLog "logs/login.logs" combined
SSLEngine on
SSLCertificateFile /etc/pki/tls/certs/www.westos.com.crt
SSLCertificatekeyFile /etc/pki/tls/private/www.westos.com.key
Require all granted
ServerName login.html.com
RewriteEngine on
RewriteRule ^(/.*)$ https://%{HTTP_HOST}$1 [redirect=301]
^(/.)$ ##客户在浏览器地址栏中输入的所有字符
https:// ##强制客户加密访问
%{HTTP_HOST} ##客户请求主机
$1 ##“$1”表示 ^(/.)$的值
[redirect=301] ##临时重写,302永久转换
http://i2.51cto.com/images/blog/201711/23/f6511a4deb91e51bb1d9d600d7c7b38a.png
http://i2.51cto.com/images/blog/201711/23/44c009abce5d9cfad359ac5f0bb523ca.png
测试:
输入内容都能跳到https
http://i2.51cto.com/images/blog/201711/23/51d5affeb4ce093eadc7f5413f7425c6.png
|