|
|
前言:
L:Linux
A:Apache
M:MariaDB
P:PHP
当我们要基于模块PHP去部署LAMP时,需要在两台主机上进行操作,一台主机提供http以及php,另一台主机提供MariDB。
本博客就基于模块类型的PHP部署两台服务器的LAMP:
如图所示:我们要基于此种模型进行部署:
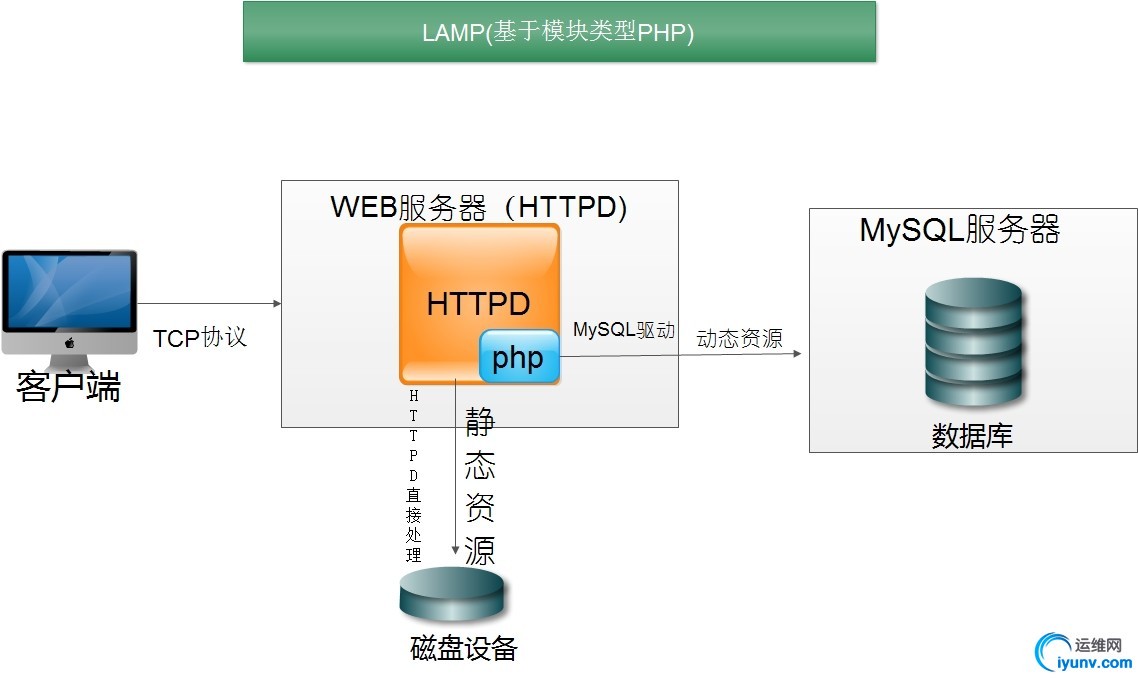
第一部分:
首先我们要准备两台Linux(CentOS7)主机;一台主机作为HTTP/PHP主机;
第一步:(部署httpd/php)
1
2
| eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.16.249.130 netmask 255.255.0.0 broadcast 172.16.255.255 #httpd服务器的ip地址
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| [iyunv@HTTP ~]# yum install -y httpd #在http主机上安装httpd
[iyunv@HTTP ~]# rpm -q httpd
httpd-2.4.6-40.el7.centos.x86_64 #CentOS 7 版本为httpd-2.4
[iyunv@HTTP ~]# yum install -y php #安装php 此种方法直接装为基于httpd模块化的php
[iyunv@httpd ~]# rpm -q php
php-5.4.16-36.el7_1.x86_64
[iyunv@HTTP httpd]# httpd -M | grep php #确定httpd已经加载php模块;
php5_module (shared)
[iyunv@HTTP ~]# yum install -y php-mysql #安装连接数据库的驱动
[iyunv@HTTP ~]# rpm -q php-mysql
php-mysql-5.4.16-36.el7_1.x86_64
[iyunv@HTTP ~]# vim /etc/httpd/conf.d/www.conf
<VirtualHost *:80> #创建虚拟主机
ServerName www.a.com
DocumentRoot "/www/
ErrorLog "/www/logs/a.error.log"
CustomLog "/www/logs/a.access.log" combined
<Directory "/www/www.a.com">
Options FollowSymLinks
Require all granted
AllowOverride None
</Directory>
</VirtualHost>
<VirtualHost *:80>
ServerName www.b.com
DocumentRoot "/www/www.b.com"
ErrorLog "/www/logs/b.error.log"
CustomLog "/www/logs/b.access.log" combined
<Directory "/www/www.b.com">
Options FollowSymLinks
Require all granted
AllowOverride None
</Directory>
</VirtualHost>
[iyunv@HTTP ~]# mkdir - pv /www/{logs, #为虚拟主机创建主页文档目录以及日志目录;
[iyunv@HTTP ~]# touch /www/logs/{a.error.log,a.access.log,b.error.log,b.access.log} #为两个虚拟主机提供日志文件;
[iyunv@HTTP httpd]# vim conf/httpd.conf
.....
#DocumentRoot "/var/www/html" #主配置文件中注释掉中心主机的主文档目录;
.....
|
第二步:(部署MariaDB服务器)
1
2
| eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.16.61.100 netmask 255.255.0.0 broadcast 172.16.255.255 #MariaDB服务器的地址;
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| [iyunv@MariaDB ~]# yum install -y mariadb #安装MariaDB
[iyunv@MariaDB ~]# systemctl start mariadb #启动数据库
[iyunv@MariaDB ~]# ss -tanl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 50 *:3306 *:* #确定3306端口处于监听状态
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
[iyunv@MariaDB ~]# mysql
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 194
Server version: 5.5.46-MariaDB-log MariaDB Server
Copyright (c) 2000, 2015, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> GRANT ALL ON *.* TO 'root'@'172.16.%.%' IDENTIFIED BY 'tianzhuang'; #授权远程连接的帐号;
|
第三步(测试http服务器能否连接数据库)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| [iyunv@HTTP httpd]# vim /www/www.a.com/index.php #在虚拟主机中创建测试页面
<?php
$conn = mysql_connect('172.16.61.100','root','tianzhuang'); #远程连接数据库的ip地址以及已经授权的帐号和密码
if ($conn)
echo "ok";
else
echo "failed";
?>
[iyunv@HTTP httpd]# systemctl start httpd #启动httpd
[iyunv@HTTP httpd]# systemctl start php-mysql #启动数据库驱动
[iyunv@HTTP httpd]# ss -tanl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 50 *:3306 *:* #确定3306端口处于监听状态
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::80 :::* #确定80端口处于监听状态
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
|
在浏览器中测试是否能连接数据库,在windows上测试需要将windows hosts文件中增加虚拟主机的FQDN解析;

测试结果:
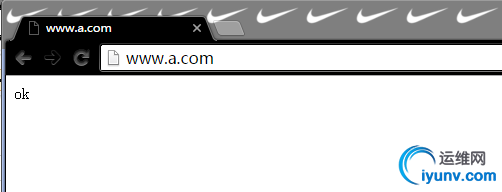
显示ok表示测试代码生效,能够远程连接到数据库服务器中。
第二部分:
分别为两台虚拟主机装入phpMyAdmin以及wordpress程序;
第一步:为www.a.com提供phpMyAdmin:
1
2
3
4
5
6
7
8
9
10
11
| [iyunv@HTTP www.a.com]# ls
index.php phpMyAdmin-4.4.14.1-all-languages.zip #下载phpMyAdmin安装包
[iyunv@HTTP www.a.com]# unzip phpMyAdmin-4.4.14.1-all-languages.zip #解压缩
[iyunv@HTTP www.a.com]# ln -sv phpMyAdmin-4.4.14.1-all-languages phpadmin #为了方便使用创建符号链接
‘phpadmin’ -> ‘phpMyAdmin-4.4.14.1-all-languages’
[iyunv@HTTP www.a.com]# ll
total 9836
-rw-r--r-- 1 root root 132 Jan 19 11:23 index.php
lrwxrwxrwx 1 root root 33 Jan 19 11:53 phpadmin -> phpMyAdmin-4.4.14.1-all-languages
drwxr-xr-x 10 root root 4096 Sep 8 12:07 phpMyAdmin-4.4.14.1-all-languages
-rw-r--r-- 1 root root 10057503 Sep 18 11:38 phpMyAdmin-4.4.14.1-all-languages.zip
|
使用浏览器登录:
输入远程连接的账户和密码之后登录到phpMyAdmin
第二步:为www.b.com主机提供wordpress:
1
2
3
4
5
6
7
| [iyunv@HTTP www.b.com]# ls
wordpress wordpress-4.3.1-zh_CN.zip #下载wordpress安装包并解压缩
[iyunv@HTTP www.b.com]# unzip wordpress-4.3.1-zh_CN.zip
[iyunv@HTTP www.b.com]# ls
wordpress wordpress-4.3.1-zh_CN.zip
[iyunv@HTTP wordpress]# cp wp-config-sample.php wp-config.php #复制示例为配置文件
|
1
| MariaDB [(none)]> create database wp; #在数据库主机中为wordpress创建数据库wp
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| [iyunv@HTTP wordpress]# vim wp-config.php
/** WordPress数据库的名称 */
define('DB_NAME','wp');
/** MySQL数据库用户名 */
define('DB_USER', 'root');wp
/** MySQL数据库密码 */
define('DB_PASSWORD', 'tianzhuang');
/** MySQL主机 */
define('DB_HOST', '172.16.61.100');
/** 创建数据表时默认的文字编码 */
define('DB_CHARSET', 'utf8');
/** 数据库整理类型。如不确定请勿更改 */
define('DB_COLLATE', '');
|
按照提示进行安装即可!
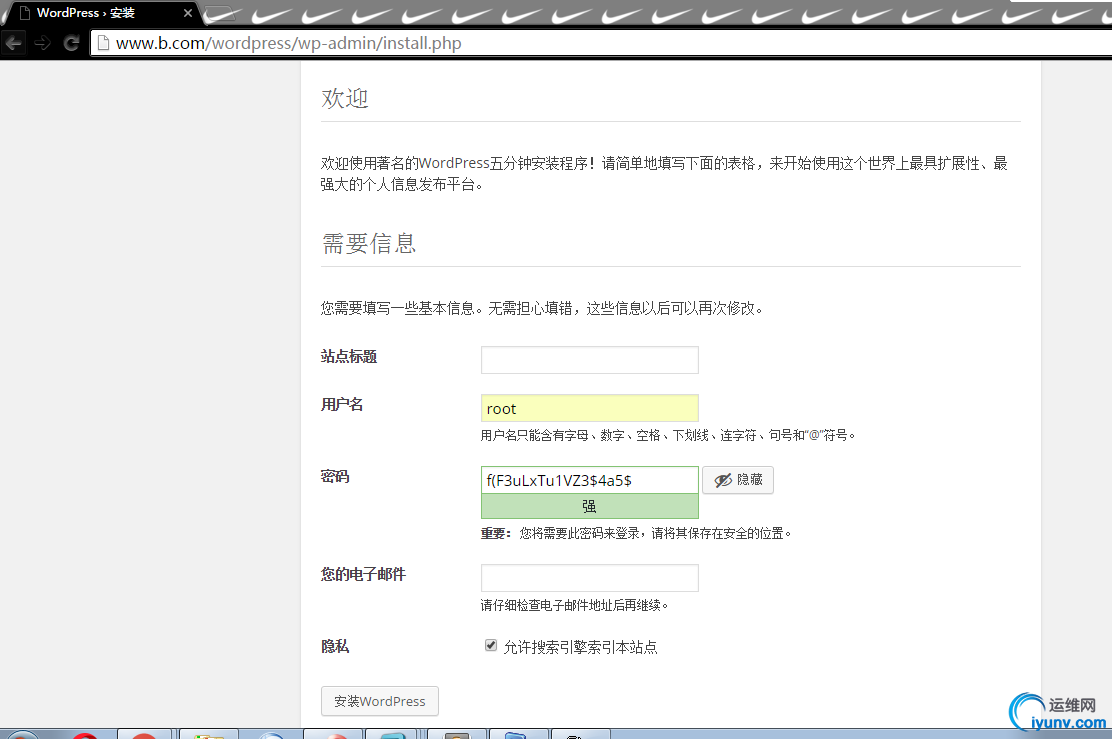
===========================================================================================
第三部分:为phpMyadmin提供https虚拟主机:
第一步:为虚拟主机申请数字证书:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
| [iyunv@CA ~]# (umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048) #生成CA的私钥
Generating RSA private key, 2048 bit long modulus
..........................................................................+++
...............................................+++
e is 65537 (0x10001)
[iyunv@CA ~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem #生成CA的自签证书
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:beijing
Organization Name (eg, company) [Default Company Ltd]:mageedu
Organizational Unit Name (eg, section) []:ops
Common Name (eg, your name or your server's hostname) []:ca.mageedu.com
Email Address []:ca@admin.com
[iyunv@CA ~]# ls /etc/pki/CA
cacert.pem certs crl newcerts private
[iyunv@CA ~]# touch /etc/pki/CA/{serial,index.txt} #创建CA需要的文件
[iyunv@CA ~]# echo 01 > /etc/pki/CA/serial
[iyunv@HTTP httpd]# mkdir ssl #在服务器端创建ssl目录
[iyunv@HTTP httpd]# cd ssl
[iyunv@HTTP ssl]# (umask 077;openssl genrsa -out httpd.key 1024) #生成服务器的私钥
Generating RSA private key, 1024 bit long modulus
.............................++++++
............................++++++
e is 65537 (0x10001)
[iyunv@HTTP ssl]# openssl req -new -key httpd.key -out httpd.csr #生成证书请求
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:beijing
Organization Name (eg, company) [Default Company Ltd]:mageedu
Organizational Unit Name (eg, section) []:ops
Common Name (eg, your name or your server's hostname) []:www.a.com
Email Address []:a@admin.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[iyunv@HTTP ssl]# scp httpd.csr root@172.16.61.100:/tmp #远程复制到ca主机上
The authenticity of host '172.16.61.100 (172.16.61.100)' can't be established.
ECDSA key fingerprint is 61:77:91:fd:34:1b:0d:2e:f8:ff:cf:f9:f6:7c:2d:09.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.16.61.100' (ECDSA) to the list of known hosts.
root@172.16.61.100's password:
Permission denied, please try again.
root@172.16.61.100's password:
httpd.csr 100% 688 0.7KB/s 00:00
[iyunv@HTTP ~]# openssl ca -in /tmp/httpd.csr -out /etc/pki/CA/certs/httpd.crt #在CA主机上签署httpd的证书请求
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jan 19 15:52:08 2016 GMT
Not After : Jan 18 15:52:08 2017 GMT
Subject:
countryName = CN
stateOrProvinceName = beijing
organizationName = mageedu
organizationalUnitName = ops
commonName = www.a.com
emailAddress = a@admin.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
0D:48:41:4D:E4:8A:C2:8F:89:B4:2A:CE:B5:D6:61:B4:94:0D:D3:B4
X509v3 Authority Key Identifier:
keyid:94:DF:49:28:82:9E:57:B0:A6:C8:8D:5F:D9:63:2C:8F:F3:7B:46:F3
Certificate is to be certified until Jan 18 15:52:08 2017 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[iyunv@HTTP ~]# scp /etc/pki/CA/certs/httpd.crt root@172.16.249.130:/etc/httpd/ssl #将签署过的证书远程复制给服务器
The authenticity of host '172.16.249.130 (172.16.249.130)' can't be established.
ECDSA key fingerprint is 88:93:ff:8b:6e:ac:a0:c1:10:1f:4b:7d:ac:44:85:f0.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.16.249.130' (ECDSA) to the list of known hosts.
root@172.16.249.130's password:
httpd.crt 100% 3833 3.7KB/s 00:00
|
第二步:配置httpd支持使用ssl,及使用的证书;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| [iyunv@HTTP ~]# yum install -y mod_ssl
[iyunv@HTTP ~]# vim /etc/httpd/conf.d/ssl.conf #编辑ssl的配置文件
.....
DocumentRoot "/www/ #主文档目录
ServerName #httpds的FQDN
.....
# Server Certificate:
# Point SSLCertificateFile at a PEM encoded certificate. If
# the certificate is encrypted, then you will be prompted for a
# pass phrase. Note that a kill -HUP will prompt again. A new
# certificate can be generated using the genkey(1) command.
SSLCertificateFile /etc/httpd/ssl/httpd.crt #证书位置
# Server Private Key:
# If the key is not combined with the certificate, use this
# directive to point at the key file. Keep in mind that if
# you've both a RSA and a DSA private key you can configure
# both in parallel (to also allow the use of DSA ciphers, etc.)
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key #私钥位置
[iyunv@HTTP ~]# systemctl reload httpd #重载服务
[iyunv@HTTP ~]# ss -tan
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 50 *:3306 *:*
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
ESTAB 0 52 172.16.249.130:22 172.16.61.1:49912
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
LISTEN 0 128 :::443 :::* #443端口已经监听
|
第三步:测试
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
| [iyunv@localhost ~]# openssl s_client -connect 172.16.249.130:443
CONNECTED(00000003)
depth=0 C = CN, ST = beijing, O = mageedu, OU = ops, CN = www.a.com, emailAddress = a@admin.com
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 C = CN, ST = beijing, O = mageedu, OU = ops, CN = www.a.com, emailAddress = a@admin.com
verify error:num=27:certificate not trusted
verify return:1
depth=0 C = CN, ST = beijing, O = mageedu, OU = ops, CN = www.a.com, emailAddress = a@admin.com
verify error:num=21:unable to verify the first certificate
verify return:1
---
Certificate chain
0 s:/C=CN/ST=beijing/O=mageedu/OU=ops/CN=www.a.com/emailAddress=a@admin.com
i:/C=CN/ST=beijing/L=beijing/O=mageedu/OU=ops/CN=ca.mageedu.com/emailAddress=ca@admin.com
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIDaTCCAlGgAwIBAgIBATANBgkqhkiG9w0BAQsFADCBhzELMAkGA1UEBhMCQ04x
EDAOBgNVBAgMB2JlaWppbmcxEDAOBgNVBAcMB2JlaWppbmcxEDAOBgNVBAoMB21h
Z2VlZHUxDDAKBgNVBAsMA29wczEXMBUGA1UEAwwOY2EubWFnZWVkdS5jb20xGzAZ
BgkqhkiG9w0BCQEWDGNhQGFkbWluLmNvbTAeFw0xNjAxMTkxNTUyMDhaFw0xNzAx
MTgxNTUyMDhaMG8xCzAJBgNVBAYTAkNOMRAwDgYDVQQIDAdiZWlqaW5nMRAwDgYD
VQQKDAdtYWdlZWR1MQwwCgYDVQQLDANvcHMxEjAQBgNVBAMMCXd3dy5hLmNvbTEa
MBgGCSqGSIb3DQEJARYLYUBhZG1pbi5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0A
MIGJAoGBAOBkKXz/lJOZNH5sC+VOqDed357ic4TsceerrJuw3SHn7wKeGI0cBL1+
e+XhCCcU6t4abv8sZqpMQR/pAfUoouF73Vp1MCu1W/MQhKl/RUixudsYMkiNB5aQ
E97egkVOTrcvcTcB10BiPyvuOi2lsZ8nQ86tiGgawPEUVyv35VXJAgMBAAGjezB5
MAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENl
cnRpZmljYXRlMB0GA1UdDgQWBBQNSEFN5IrCj4m0Ks611mG0lA3TtDAfBgNVHSME
GDAWgBSU30kogp5XsKbIjV/ZYyyP83tG8zANBgkqhkiG9w0BAQsFAAOCAQEAVqOH
LKhD4MKgx8E+8Lwe268BNbGOhc5z0q0pq1imjrJ0Y/QAqgni3PBn/2AGwqGZISbj
KBRZxcMHJdDuVRDHWsgWeeo8+ui7KVaNiAOE77pyYSK4HNdq9DZwwgk607a9GLvu
fTq8umBP2mZAKHWkZkBcnpP1vFDgrE/s5XsLGBXmfjd4UnPehFpSqpsVcSWr8+nz
NRUVxmBpSE7Os4GtpHRmGmJSXlRCOtnppWOpFjmgTEX8BBogfi02zJ9PncJV3LO9
8v93iwI56LBHhx97U7afFPSNlgjfL5HbFFVqF0nHkQuqtjgJ/FSvmCq2Ei7FkPQz
zT0pFBM8N3+Ktj5OQw==
-----END CERTIFICATE-----
subject=/C=CN/ST=beijing/O=mageedu/OU=ops/CN=www.a.com/emailAddress=a@admin.com
issuer=/C=CN/ST=beijing/L=beijing/O=mageedu/OU=ops/CN=ca.mageedu.com/emailAddress=ca@admin.com
---
No client certificate CA names sent
Server Temp Key: ECDH, secp521r1, 521 bits
---
SSL handshake has read 1508 bytes and written 443 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 1024 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 46EAFD7AA09035829482E579C92EA5F502D46B9809E909C7359B3F770BFA7052
Session-ID-ctx:
Master-Key: 63EAD37CEFF0CDF4D3F60D3B964AB551562A2BDB32EC3620B2AB0B62D82D455ED27A4653CFB1A8CE9483B09541DC3DFB
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - f8 cb 27 97 83 d1 6b d4-ee ca 50 0e d1 ac 8a 55 ..'...k...P....U
0010 - 32 71 98 37 6a 4d 16 34-68 69 44 30 57 34 03 6d 2q.7jM.4hiD0W4.m
0020 - 0f 85 a9 57 d6 08 5b d2-05 63 a5 09 71 5c 2b f0 ...W..[..c..q\+.
0030 - 16 60 0a 7d 66 1c fe 9b-7b 5d 16 98 14 44 c9 c2 .`.}f...{]...D..
0040 - 02 da 0b b2 b3 06 44 c9-28 43 45 4b 72 5c ad 8c ......D.(CEKr\..
0050 - fd 39 1f 71 bd 60 d7 16-95 70 28 ad 92 7b aa 40 .9.q.`...p(..{.@
0060 - db 0f b9 f6 87 03 6c 3c-41 21 b8 bc 25 39 b1 63 ......l<A!..%9.c
0070 - 64 a2 91 e1 0d c5 86 9f-f9 58 ce ba 83 c7 dc 0a d........X......
0080 - 20 78 d3 da c6 28 04 fd-91 6c a9 cf a2 96 28 59 x...(...l....(Y
0090 - dd 6e 3f a2 88 da 4e bb-8f 00 96 c4 2f f1 cb c0 .n?...N...../...
00a0 - fd ae 4b 0d 71 ab a3 a3-67 d9 3c 19 68 e7 3a df ..K.q...g.<.h.:.
00b0 - 35 2a bd 9e e6 18 30 6d-01 28 00 a2 a9 4c 2e cf 5*....0m.(...L..
Start Time: 1453219861
Timeout : 300 (sec)
Verify return code: 21 (unable to verify the first certificate)
---
|
|
|