|
httpd 自建CA 认证 实现 https 服务
需要的软件: httpd mod_ssl openssl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
| [iyunv@jinyongri CA]# httpd -v #httpd版本
Server version: Apache/2.2.15 (Unix)
Server built: Jul 23 2014 14:15:00
[iyunv@jinyongri CA]# uname -r #内核版本
2.6.32-431.el6.i686
[iyunv@jinyongri CA]# uname -a #发型版本
Linux jinyongri.com 2.6.32-431.el6.i686 #1 SMP Fri Nov 22 00:26:36 UTC 2013 i686 i686 i386 GNU/Linux
###################################开始干活##############################################
[iyunv@jinyongri ~]# cd /etc/pki/CA/ #切换到证书目录之下
[iyunv@jinyongri CA]# (umask 077; openssl genrsa -out private/cakey.pem 2048)
#生成自建CA用私钥
Generating RSA private key, 2048 bit long modulus
......+++
.....+++
e is 65537 (0x10001)
[iyunv@jinyongri CA]# openssl req -new -x509 -key private/cakey.pem -days 3655 -out cacert.pem
#提交自签证书申请
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN #国家
State or Province Name (full name) []:ShangHai #省份
Locality Name (eg, city) [Default City]:ShangHai #城市
Organization Name (eg, company) [Default Company Ltd]:jinyongri Ltd #公司名
Organizational Unit Name (eg, section) []:SA #部门名称
Common Name (eg, your name or your server's hostname) []:ca.jinyongri.com #主机名
Email Address []:admin@jinyongri.com #管理员邮箱
[iyunv@jinyongri CA]# mkdir /etc/httpd/conf/ssl -p #建立存放httpd服务器私钥和证书的目录
[iyunv@jinyongri CA]# (umask 077; openssl genrsa 1024 > /etc/httpd/conf/ssl/httpd.key)
#创建httpd私钥
Generating RSA private key, 1024 bit long modulus
........++++++
............++++++
e is 65537 (0x10001)
[iyunv@jinyongri CA]# cd /etc/httpd/conf/ssl/ #切换到存放httpd私钥目录下
[iyunv@jinyongri ssl]# openssl req -new -key ./httpd.key -out ./httpd.csr
#提交httpd证书申请
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:ShangHai
Locality Name (eg, city) [Default City]:ShangHai
Organization Name (eg, company) [Default Company Ltd]:jinyongri Ltd
Organizational Unit Name (eg, section) []:SA
Common Name (eg, your name or your server's hostname) []:www.jinyongri.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:jinyongri Ltd
[iyunv@jinyongri ssl]# touch /etc/pki/CA/{index.txt,crlnumber}
[iyunv@jinyongri ssl]# echo 01 > /etc/pki/CA/serial
[iyunv@jinyongri ssl]# openssl ca -in httpd.csr -out httpd.crt -days 3655 #生成httpd证书
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Sep 29 12:16:18 2014 GMT
Not After : Oct 1 12:16:18 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = ShangHai
organizationName = jinyongri Ltd
organizationalUnitName = SA
commonName = www.jinyongri.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
BB:A2:68:13:FB:EA:BB:A8:52:D9:6A:AB:02:43:94:40:28:74:72:2A
X509v3 Authority Key Identifier:
keyid:5A:68:9C:F6:D1:5D:51:36:A5:95:3C:28:B1:7F:76:F9:9E:69:48:56
Certificate is to be certified until Oct 1 12:16:18 2024 GMT (3655 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[iyunv@jinyongri ssl]# yum install -y mod_ssl #安装httpd的mod_ssl模块
[iyunv@jinyongri ssl]# rpm -ql mod_ssl #看一下都生成了哪些文件
/etc/httpd/conf.d/ssl.conf
/usr/lib/httpd/modules/mod_ssl.so
/var/cache/mod_ssl
/var/cache/mod_ssl/scache.dir
/var/cache/mod_ssl/scache.pag
/var/cache/mod_ssl/scache.sem
[iyunv@jinyongri ssl]# vim /etc/httpd/conf.d/ssl.conf#
#配置实用ssl的虚拟主机
# ServerName
# DocumentRoot
#配置证书和私钥
# SSLCertificatFile 证书文件
# SSLCertificatKeyFile 密钥文件
DocumentRoot "/var/www/html" #网页根目录
ServerName
[iyunv@jinyongri ssl]# httpd -t #检测配置文件语法错误
Syntax OK
[iyunv@jinyongri ssl]# service httpd restart #重启httpd服务
Stopping httpd: [ OK ]
Starting httpd: [ OK ]
[iyunv@jinyongri CA]# cp /etc/pki/CA/cacert.pem /etc/pki/CA/cacert.crt
#复制一个CA服务器认证证书, 以便于windows来安装
|
使用window7客户端来检测
修改C:WindowsSystem32driversetchosts 添加如下内容, 自己的web服务器ip和测试用域名
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
#127.0.0.1 localhost
#::1 localhost
192.168.1.100www.jinyongri.com #添加这一行,要根据自己的ip和域名来配置
注意: 这个域名要和注册CA证书的域名一致, 否则会出错,
如果无法修改请配置当前用户对该文件的写入权限.
把刚才复制好的/etc/pki/CA/cacert.crt CA服务器证书下载windows客户端上

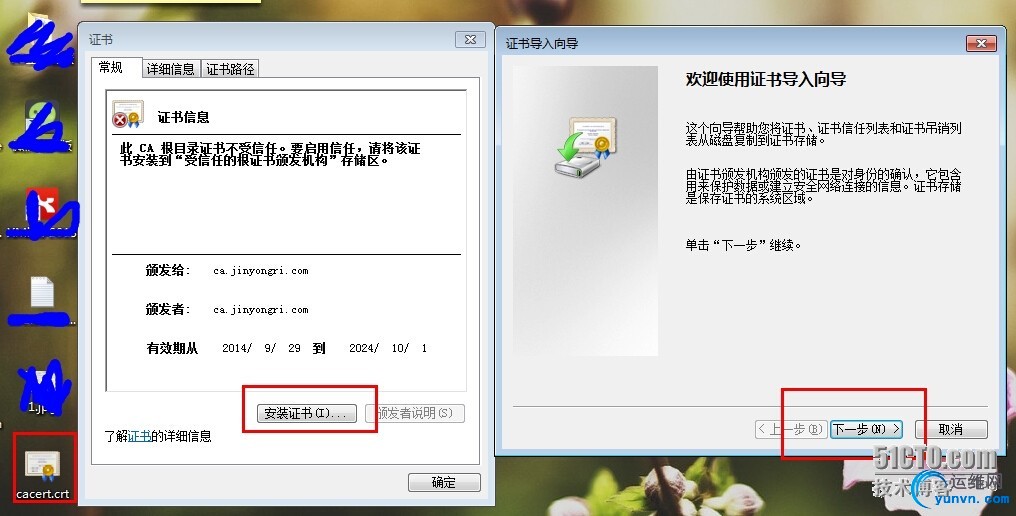

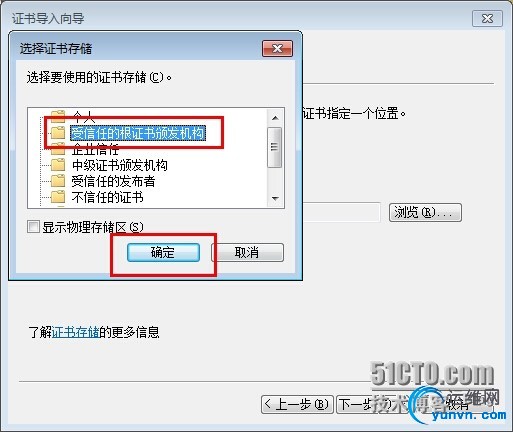

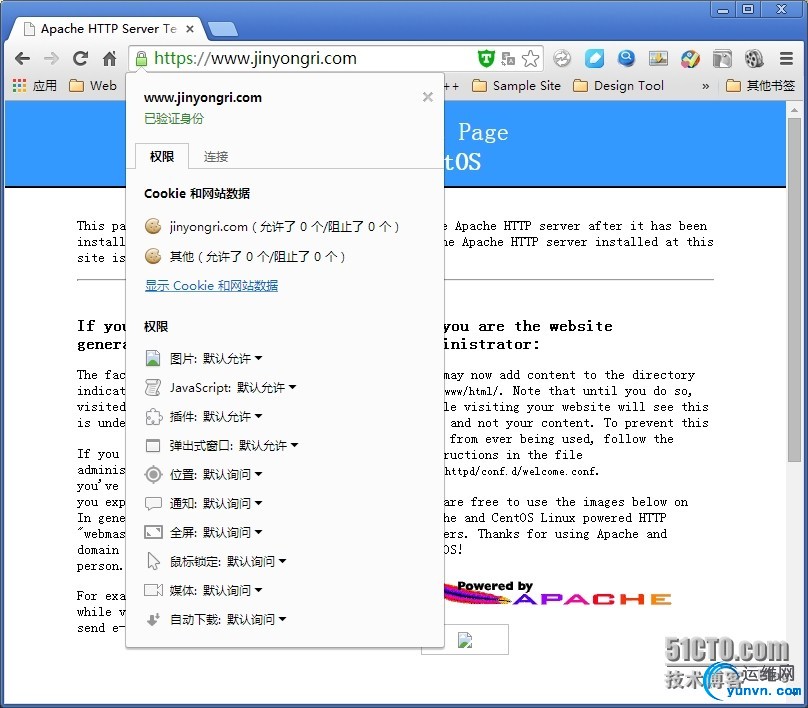
|