|
Keepalived 高可用ipvs和nginx服务 ============================================================================
概述:
本章讲主要介绍keepalived高可用ipvs服务和nginx服务,内容如下:
- keepalived 配置文件中Virtual_server(虚拟服务器)的配置格式及常用参数;
- keepalived高可用ipvs-dr模型实验过程详解;
- keepalived调用外部辅助脚本实现资源监控及调其优先级;
- keepalived高可用nginx服务;
- 总结keepalined高可用nginx及ipvs的配置示例以及通知脚本
============================================================================
回顾:

Virtual Server(虚拟服务器): 1.配置参数: ★虚拟服务器的配置格式: 1
2
3
4
5
6
7
8
9
| virtual_server IP port |
virtual_server fwmark int
{
...
real_server {
...
}
...
}
|
★常用参数
keepalived高可用的ipvs-dr集群前面讲到用LVS的DR模式来实现Web应用的负载均衡。为了防止LVS服务器自身的单点故障导致整个Web应用无法提供服务,因此还得利用Keepalived实现lvs的高可用性。
1.实验原理:

2.实验环境准备
- 准备四台虚拟主机,两台作为real_server,两台作为keepalived+lvs-dr模型的调度器;
- 在两个RS上修改内核参数,来限制arp响应和通告的级别;
- 配置两台keepalived+lvs-dr调度器的virtual_server
3.ip地址规划:
- keepalived+lvs-dr模型的调度器
node1:10.1.252.161
node2:10.1.249.203
- 要转移的ip地址:
10.1.252.73,把其80端口定义为集群服务
- Real_server
RS 1:10.1.252.37
RS 2:10.1.252.153
其80端口分别向外提供web服务
4.实验环境搭建:
1)首先为两台RS准备httpd服务,并提供测试页面如下:
RS 1

RS 2为一台CentOS 6主机
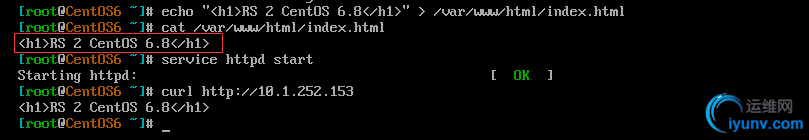
2)接下来我们要修改两台RS的内核参数arp_ignore和arp_announce,然后配置其本地lo网卡的网卡别名作为VIP(配置可参考先前的文档脚本),如下:
RS 1 vip如下:
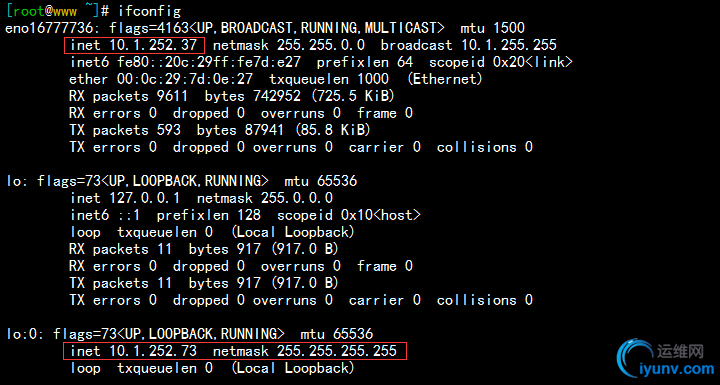
RS 2 vip如下:

5.配置调度器node1,和node2,的keepalived服务,手动测试看能否调度到后端RS,过程如下:
1)node1配置如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| [iyunv@node1 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id node1
vrrp_mcast_group4 224.0.100.19
}
vrrp_instance VI_1 {
state MASTER
interface eno16777736
virtual_router_id 17
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass f7111b2e
}
virtual_ipaddress {
10.1.252.73/16 dev eno16777736
}
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
|
2)node2,配置如下;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| [iyunv@node2 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id node1
vrrp_mcast_group4 224.0.100.19
}
vrrp_instance VI_1 {
state BACKUP
interface eno16777736
virtual_router_id 17
priority 98
advert_int 1
authentication {
auth_type PASS
auth_pass f7111b2e
}
virtual_ipaddress {
10.1.252.73/16 dev eno16777736
}
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
|
3)在node1上对转移ip:10.1.252.73的80端口定义集群服务,如下:
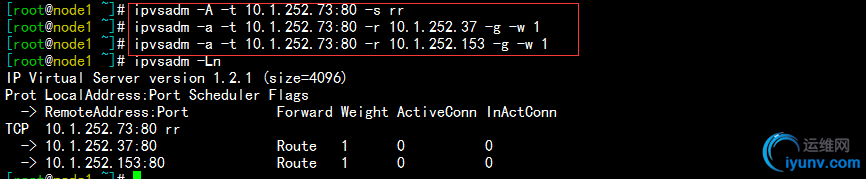
4)启动node1节点上的keepalived服务,然后在node2上做测试,如下:
启动node1,之后查看ip,因为此时node1为主节点,所以转移ip在node1上,如下:

在node2上做测试,可以看到是以轮询的方式响应,如下:
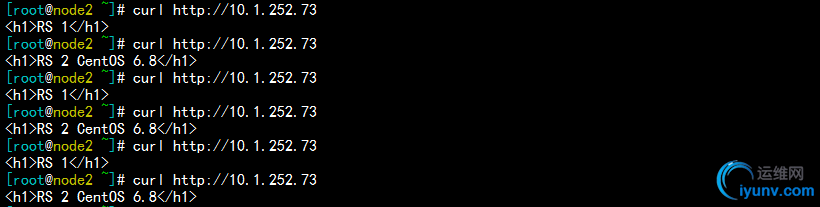
5)关闭node1上的keepalived服务,使10.1.252.73的地址转移到node2,以同样的方法在node2上定义转移ip的集群服务,在node1上测试发现,同样可以以轮询的方式正常调度到后端的RS服务器。

6.如上,两个节点手动测试都没有问题,清空两个调度器上的定义的集群服务;接下来我们要通过定义keepalived的配置文件来自动生成ipvsadm定义的规则。
1)首先编辑node1的配置文件,定义virtual server(虚拟主机服务),如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
| [iyunv@node1 keepalived]# cat keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id node1
vrrp_mcast_group4 224.0.100.19
}
vrrp_instance VI_1 {
state MASTER
interface eno16777736
virtual_router_id 17
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass f7111b2e
}
virtual_ipaddress {
10.1.252.73/16 dev eno16777736
}
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
virtual_server 10.1.252.73 80 { # 定义转移ip端口80的集群服务
delay_loop 3
lb_algo rr
lb_kind DR
protocol TCP
real_server 10.1.252.37 80 { # 定义集群服务包含的RS 1
weight 1 # 权重为1
HTTP_GET { # 定义RS1的健康状态检测
url {
path /
status_code 200
}
connect_timeout 1
nb_get_retry 3
delay_before_retry 1
}
}
real_server 10.1.252.153 80 { # 定义集群服务包含的RS 1
weight 1 # 权重为1
HTTP_GET { # 定义RS1的健康状态检测
url {
path /
status_code 200
}
connect_timeout 1
nb_get_retry 3
delay_before_retry 1
}
}
}
|
同理,在node2的节点上也添加定义virtual server,如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
| [iyunv@node2 keepalived]# cat keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id node1
vrrp_mcast_group4 224.0.100.19
}
vrrp_instance VI_1 {
state BACKUP
interface eno16777736
virtual_router_id 17
priority 98
advert_int 1
authentication {
auth_type PASS
auth_pass f7111b2e
}
virtual_ipaddress {
10.1.252.73/16 dev eno16777736
}
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
virtual_server 10.1.252.73 80 {
delay_loop 3
lb_algo rr
lb_kind DR
protocol TCP
real_server 10.1.252.37 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 1
nb_get_retry 3
delay_before_retry 1
}
}
real_server 10.1.252.153 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 1
nb_get_retry 3
delay_before_retry 1
}
}
}
|
7.如上,两个节点node1和node2都已经定义好虚拟主机的集群服务,现在我们开始测试。
1)启动node1和node2上的keepalived服务,因为node1为主节点,所以首先连接转移ip的集群服务,如下:
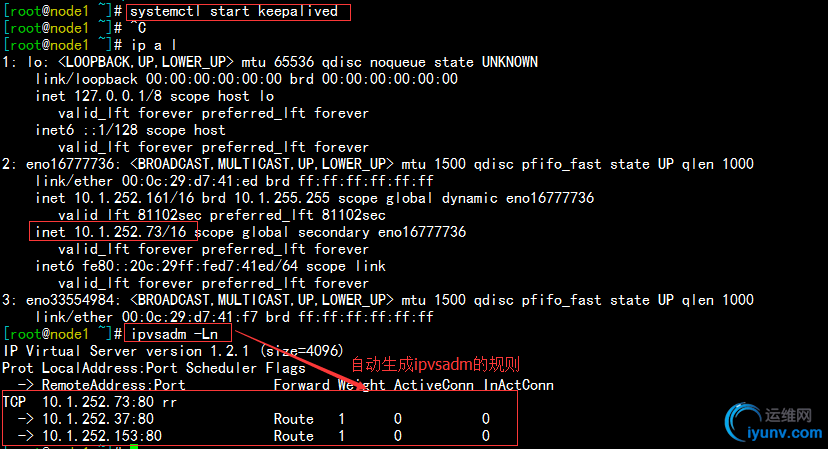
使用curl测试访问发现,以轮询的方式响应,如下:

现在我停止后端主机RS1,再次在node1上使用ipvsadm查看,RS1已经不存在了,使用curl请求,这是只有RS2响应,如下:
1
2
3
4
5
6
7
| [iyunv@node1 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 10.1.252.73:80 rr
-> 10.1.252.153:80 Route 1 0 0
You have new mail in /var/spool/mail/root
|
1
2
3
4
5
6
7
8
9
10
11
| [iyunv@node2 ~]# for i in {0..9};do curl http://10.1.252.73 ;done
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 2 CentOS 6.8</h1>
|
把RS1启动,3s之后ipvsadm规则就又检测到了,使用curl请求,后端主机又是以轮询的方式响应:
1
2
3
4
5
6
7
| [iyunv@node1 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 10.1.252.73:80 rr
-> 10.1.252.37:80 Route 1 0 0
-> 10.1.252.153:80 Route 1 0 0
|
1
2
3
4
5
6
7
8
9
10
11
| [iyunv@node2 ~]# for i in {0..9};do curl http://10.1.252.73 ;done
<h1>RS 1</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS 2 CentOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS 2 CentOS 6.8</h1>
|
如果我们把后端的两台RS都停止服务,发现再使用ipvsadm就检测不到了,使用curl访问,提示拒绝访问,如下:
1
2
3
4
5
6
7
8
9
10
11
| [iyunv@node2 ~]# for i in {0..9};do curl http://10.1.252.73 ;done
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
curl: (7) Failed connect to 10.1.252.73:80; Connection refused
|
8.现在我们就需要定义一个sorry_server,可以用来提醒用户,集群服务出现故障。这里要使用调度器本身的httpd服务来做更合适;并且,要保证两台调度器的web服务都启动起来。
注意:调度器的web服务在这是没有用的,因为80端口直接在INPUT链上已经被劫走,当做集群服务了,所以调度器上的web服务只能当做sorry_server。
1)在node1和node2上定义sorry_server如下:(以node1为例)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
| [iyunv@node1 keepalived]# cat keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id node1
vrrp_mcast_group4 224.0.100.19
}
vrrp_instance VI_1 {
state MASTER
interface eno16777736
virtual_router_id 17
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass f7111b2e
}
virtual_ipaddress {
10.1.252.73/16 dev eno16777736
}
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
virtual_server 10.1.252.73 80 {
delay_loop 3
lb_algo rr
lb_kind DR
protocol TCP
sorry_server 127.0.0.1 80 # 定义的 sorry_server为本机的80端口
real_server 10.1.252.37 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 1
nb_get_retry 3
delay_before_retry 1
}
}
real_server 10.1.252.153 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 1
nb_get_retry 3
delay_before_retry 1
}
}
}
|
2)然后我们编辑本机httpd服务的映射根目录,添加提醒用户的测试页面,如下:
1
2
3
| [iyunv@node1 html]# echo "<h1>LB Cluster Fault,this is Sorry Server 1</h1>" > /var/www/html/index.html
[iyunv@node1 html]# cat /var/www/html/index.html
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
|
3)在后端两台RS停止服务的情况下,使用ipvsadm查看,可以看到有本机的定义的sorry_server,使用curl访问如下:
1
2
3
4
5
6
| [iyunv@node1 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 10.1.252.73:80 rr
-> 127.0.0.1:80 Route 1 0 0
|
1
2
3
4
5
6
7
8
9
10
11
| [iyunv@node2 ~]# for i in {0..9};do curl http://10.1.252.73 ;done
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
<h1>LB Cluster Fault,this is Sorry Server 1</h1>
|
4)后端主机只要有一个RS启动,3s之后sorry_server就会下线了,由后端主机提供服务。
如上,整个过程就是利用keepalived高可用lvs-dr负载均衡的web集群。。。
=============================================================================
keepalived实现优先级动态调整;keepalived调用外部的辅助脚本进行资源监控,并根据监控的结果状态能实现优先动态调整;

示例:
我们在前面的试验中,每次如果由主动节点跳转到被动节点,都是手动把keepalived服务停掉才能实现。但是在实际生产环境中,如果我们不想让他停止服务,只是暂时的进行维护,那该怎么办呢?
keeoalived有一个功能,可以调用外部脚本来完成资源监控,然后根据资源监控的结果,来完成优先级的动态调整。
这里我定义一个外部脚本,如果在/etc/keepalived/下存在down文件,则节点优先级减5,编辑配置文件,如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| [iyunv@centos7 keepalived]# cat keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id node1
vrrp_mcast_group4 224.0.100.19
}
# 定义外部脚本,如果/etc/keepalived/down存在,则返回值为1,否则为0
vrrp_script chk_down {
script "[[ -f /etc/keepalived/down ]] && exit 1 || exit 0"
interval 1 # 每个1s钟检测一次
weight -5 # 优先级减去5
}
vrrp_instance VI_1 {
state MASTER
interface eno16777736
virtual_router_id 17
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass f7111b2e
}
virtual_ipaddress {
10.1.252.73/16 dev eno16777736
}
track_script { # 调用定义的外部脚本
chk_down
}
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
|
同样的定义在节点node2也编辑过去,然后保存,现在我们来测试,启动node1和node2的keepalived服务,此时node1因为优先级高,所以资源ip在主节点node1,如下:

然后我们在主节点node1的/etc/keepalived下创建一个down文件,可以发现node1的资源ip已经转移到备用节点node2上了,如下:

备用节点查看如下:
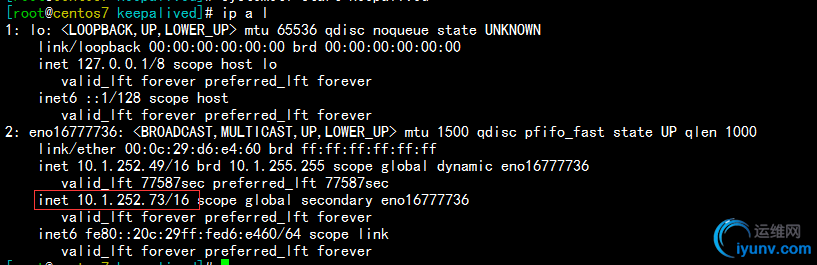
现在,我们把主节点node1上的down文件删除,发现1秒钟之后,资源ip又被node1抢了会来,如下:

keepalived高可用nginx服务1.实验拓扑图 2.实验环境准备 - 准备四台虚拟主机,两台作为real_server,两台配置nginx服务作为调度器;
- 在两台nginx调度器上配置upstream模块,然后proxy反代到两台后端主机
- 配置两台nginx调度器的virtual_serve
3.ip地址规划和高可用lpvs-dr相同
4.实验环境搭建如下:
1)首先,在作为两台nginx调度器上配置配置upstream模块,然后proxy反代到两台后端主机,如下:
在/etc/nginx/nginx.conf中的http配置段定义后端web服务器组;
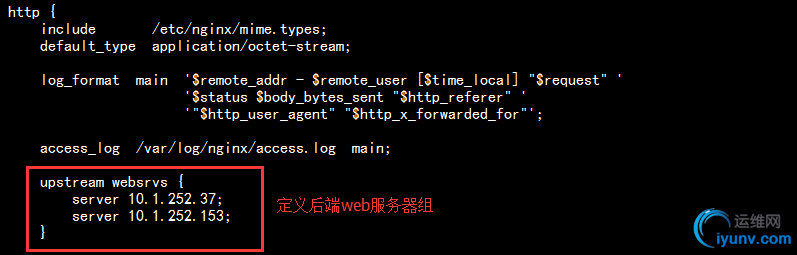
在/etc/nginx/conf.d/default.conf的server中定义proxy反向代理

node2上的nginx配置和node1是相同的,这里不在列出。
2)配置node1和node2上的keepalived服务,使用nginx不需要定义virtual_server,如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| [iyunv@node1 keepalived]# cat keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id node1
vrrp_mcast_group4 224.0.100.19
}
vrrp_script chk_down {
script "[[ -f /etc/keepalived/down ]] && exit 1 || exit 0"
interval 1
weight -5
}
vrrp_instance VI_1 {
state MASTER
interface eno16777736
virtual_router_id 17
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass f7111b2e
}
virtual_ipaddress {
10.1.252.73/16 dev eno16777736
}
track_script {
chk_down
}
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
|
5.如上,整个环境及配置就已经完成了,现在,启动主备节点node1上的nginx服务,和keepalived服务,查看主节点node1的ip,发现资源ip在node1上,如下:

1)测试,在客户端请求nginx调度器上的资源ip,可以发现后端web服务器以轮询的方式响应客户端请求,如下:
1
2
3
4
5
6
7
8
9
10
11
| [iyunv@localhost ~]# for i in {0..9};do curl http://10.1.252.73;done
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
|
2)在主节点node1的/etc/keepalived/下创建一个down文件,因为前面定义了一个调用外部脚本,改变其优先级,所以,这时node1节点的优先级降低,资源ip转移到备用节点node2上,再在客户端请求,发现后端web服务不收影响
1
2
3
4
5
6
7
8
9
10
11
| [iyunv@localhost ~]# for i in {0..9};do curl http://10.1.252.73;done
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
|
6.假如资源ip所在nginx调度器服务宕机或者出现故障了,这时,因为不是keepalived服务故障,所以资源ip时不会转移的。这时,我们就要保证在出现故障前把资源ip转移到备用nginx调度器上,所以,这里我们也可以再定义一个外部脚本来监控nginx服务,一旦出现故障就会调用脚本,降低其优先级然后转移资源ip到备用nginx调度器,如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
| [iyunv@node1 keepalived]# cat keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id node1
vrrp_mcast_group4 224.0.100.19
}
vrrp_script chk_down {
script "[[ -f /etc/keepalived/down ]] && exit 1 || exit 0"
interval 1
weight -5
}
vrrp_script chk_nginx { # 定义检测nginx的外部脚本
script "killall -0 nginx && exit 0 || exit 1" # 如果检测到nginx服务在就返回0(为真),如果不在就返回值1(假)
interval 1 # 每隔1s检测一次
weight -5 # 优先级减5
}
vrrp_instance VI_1 {
state MASTER
interface eno16777736
virtual_router_id 17
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass f7111b2e
}
virtual_ipaddress {
10.1.252.73/16 dev eno16777736
}
track_script {
chk_down
chk_nginx # 调用此脚本
}
notify_master "/etc/keepalived/notify.sh master"
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
|
实验如下:
1)现在资源ip在主节点node1上,此时访问资源ip可以正常响应;现在我们把node1上的nginx服务进程杀掉,再去访问,发现请求不到资源,资源ip也没有转移到备用节点node2,如下:

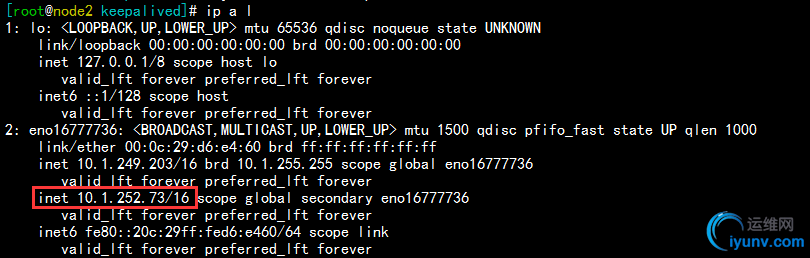
2)在配置文件中,定义调用检查nginx服务的脚本后,我们再去做上面的实验,发现资源ip在停止服务前减低优先级,把资源ip转移到备用nginx调度器上,如下:
杀掉node1的nginx服务,发现资源ip已经不在了

请求服务,发现仍然可以访问
1
2
3
4
5
6
7
8
9
10
11
| [iyunv@localhost ~]# for i in {0..9};do curl http://10.1.252.73;done
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
<h1>RS 1</h1>
<h1>RS2 CentCOS 6.8</h1>
|
查看备用nginx调度器node2,发现资源ip成功转移过来,如下:
3)当一个节点nginx服务出现故障,我们就要立即去修复,或者重启服务,如果不想手动去修改,可以编辑通知脚本,在主节点变为MASTER和BACKUP都重启nginx服务,如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| [iyunv@node1 keepalived]# cat notify.sh
#!/bin/bash
#
contact='root@localhost'
notify() {
mailsubject="$(hostname) to be $1,vip floating"
mailbody="$(date +'%F %T'): vrrp transition, $(hostname) changed to be $1"
echo "$mailbody" |mail -s "$mailsubject" $contact
}
case $1 in
master)
notify master
systemctl restart nginx.service
;;
backup)
notify backup
systemctl restart nginx.service
;;
fault)
notify fault
;;
*)
echo "Usage: $(basename $0) {master|backup|fault}"
exit 1
;;
esac
|
现在我再把主节点的nginx服务kill掉,发现主节点资源ip转移到备用nginx节点node2,但是马上nginx服务就又启动起来了,资源ip又转移到主节点node1,如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| [iyunv@node1 keepalived]# killall nginx # 杀掉node1的nginx服务
[iyunv@node1 keepalived]# ip a l
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eno16777736: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:21:c9:43 brd ff:ff:ff:ff:ff:ff
inet 10.1.252.161/16 brd 10.1.255.255 scope global eno16777736
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe21:c943/64 scope link # 资源ip转移
valid_lft forever preferred_lft forever
# =====================================================================================
[iyunv@node1 keepalived]# ip a l
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eno16777736: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:21:c9:43 brd ff:ff:ff:ff:ff:ff
inet 10.1.252.161/16 brd 10.1.255.255 scope global eno16777736
valid_lft forever preferred_lft forever
inet 10.1.252.73/16 scope global secondary eno16777736 # 资源ip又被抢占回来了
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe21:c943/64 scope link
valid_lft forever preferred_lft forever
|
查看node2的日志,也可以发现资源在短时间内转移了2次

如上就是整个keepalived高可用nginx服务的整个过程。。。
=====================================================================
总结:
1.keepalived高可用nginx主节点配置示例:

2.高可用nginx通知脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| #!/bin/bash
#
contact='root@localhost'
notify() {
mailsubject="$(hostname) to be $1,vip floating"
mailbody="$(date +'%F %T'): vrrp transition, $(hostname) changed to be $1"
echo "$mailbody" |mail -s "$mailsubject" $contact
}
case $1 in
master)
notify master
systemctl restart nginx.service
;;
backup)
notify backup
systemctl restart nginx.service
;;
fault)
notify fault
;;
*)
echo "Usage: $(basename $0) {master|backup|fault}"
exit 1
;;
esac
|
3.高可用ipvs+dr主机点配置示例
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
| [iyunv@node1 keepalived]# cat keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from keepalived@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id node1
vrrp_mcast_group4 224.0.100.19
}
vrrp_instance VI_1 {
state MASTER
interface eno16777736
virtual_router_id 17
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass f7111b2e
}
virtual_ipaddress {
10.1.252.73/16 dev eno16777736 # 要转移的资源ip
}
notify_master "/etc/keepalived/notify.sh master" # 调用通知脚本
notify_backup "/etc/keepalived/notify.sh backup"
notify_fault "/etc/keepalived/notify.sh fault"
}
virtual_server 10.1.252.73 80 { # 定义转移资源ip上的集群服务
delay_loop 3
lb_algo rr
lb_kind DR
protocol TCP
sorry_server 127.0.0.1 80 # 定义的 sorry_server为本机的80端口
real_server 10.1.252.37 80 { # 定义后端Real_server所提供的80服务
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 1
nb_get_retry 3
delay_before_retry 1
}
}
real_server 10.1.252.153 80 {
weight 1
HTTP_GET {
url {
path /
status_code 200
}
connect_timeout 1
nb_get_retry 3
delay_before_retry 1
}
}
}
|
|