|
|
环境:CentOS 6.4(最小化安装)
SNAT测试:
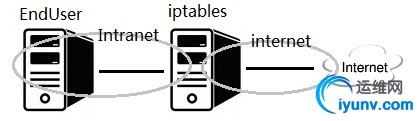
地址规划:
Node | IP address
| GW
| EndUser | 192.168.101.241/24
| 192.168.101.1
| iptables
| eth1:192.168.101.1/24
eth0:192.168.100.242/24
| 192.168.100.1
|
EndUser:
1
2
3
4
5
6
7
| [iyunv@EndUser ~]# tail -n 5 /etc/sysconfig/network-scripts/ifcfg-eth0
BOOTPROTO=static
IPADDR=192.168.101.241
NETMASK=255.255.255.0
GATEWAY=192.168.101.1
DNS1=114.114.114.114
[iyunv@EndUser ~]#
|
测试网关:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| [iyunv@EndUser ~]# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.101.0 * 255.255.255.0 U 0 0 0 eth0
link-local * 255.255.0.0 U 1002 0 0 eth0
default 192.168.101.1 0.0.0.0 UG 0 0 0 eth0
[iyunv@EndUser ~]# ping 192.168.101.1 -c 4
PING 192.168.101.1 (192.168.101.1) 56(84) bytes of data.
64 bytes from 192.168.101.1: icmp_seq=1 ttl=64 time=0.315 ms
64 bytes from 192.168.101.1: icmp_seq=2 ttl=64 time=0.340 ms
64 bytes from 192.168.101.1: icmp_seq=3 ttl=64 time=0.320 ms
64 bytes from 192.168.101.1: icmp_seq=4 ttl=64 time=0.317 ms
--- 192.168.101.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3001ms
rtt min/avg/max/mdev = 0.315/0.323/0.340/0.010 ms
[iyunv@EndUser ~]# ping 192.168.100.242 -c 4
PING 192.168.100.242 (192.168.100.242) 56(84) bytes of data.
64 bytes from 192.168.100.242: icmp_seq=1 ttl=64 time=0.557 ms
64 bytes from 192.168.100.242: icmp_seq=2 ttl=64 time=0.339 ms
64 bytes from 192.168.100.242: icmp_seq=3 ttl=64 time=0.319 ms
64 bytes from 192.168.100.242: icmp_seq=4 ttl=64 time=0.400 ms
--- 192.168.100.242 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3003ms
rtt min/avg/max/mdev = 0.319/0.403/0.557/0.096 ms
[iyunv@EndUser ~]#
|
iptables:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| [iyunv@iptables ~]# tail -n 5 /etc/sysconfig/network-scripts/ifcfg-eth0
BOOTPROTO=static
IPADDR=192.168.100.242
NETMASK=255.255.255.0
GATEWAY=192.168.100.1
DNS1=114.114.114.114
[iyunv@iptables ~]# tail -n 4 /etc/sysconfig/network-scripts/ifcfg-eth1
NM_CONTROLLED=yes
BOOTPROTO=static
IPADDR=192.168.101.1
NETMASK=255.255.255.0
[iyunv@iptables ~]# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.100.0 * 255.255.255.0 U 0 0 0 eth0
192.168.101.0 * 255.255.255.0 U 0 0 0 eth1
link-local * 255.255.0.0 U 1002 0 0 eth0
link-local * 255.255.0.0 U 1003 0 0 eth1
default 192.168.100.1 0.0.0.0 UG 0 0 0 eth0
[iyunv@iptables ~]#
[iyunv@iptables ~]# grep forward /etc/sysctl.conf |grep -v ^#
net.ipv4.ip_forward = 1
[iyunv@iptables ~]# sysctl -p
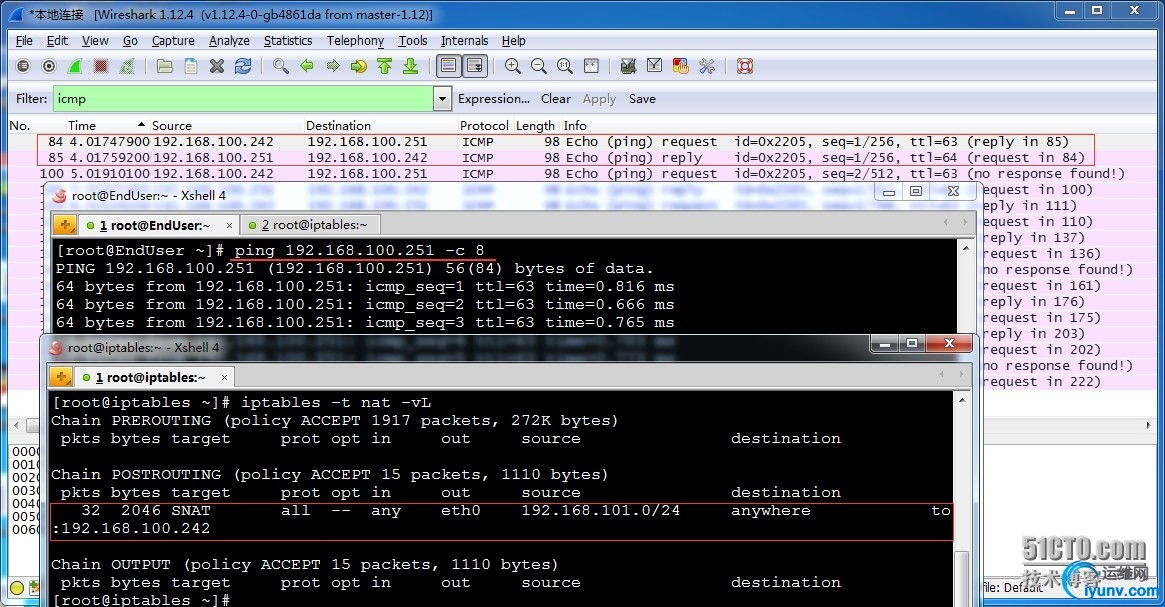
[iyunv@iptables ~]# iptables -t nat -vL //查看linux下NAT映射表
|

1
2
3
4
5
6
7
8
9
| [iyunv@iptables ~]# grep "POSTROUTING" /etc/sysconfig/iptables|grep -v ^:
-A POSTROUTING -s 192.168.101.0/24 -o eth0 -j SNAT --to-source 192.168.100.242
[iyunv@iptables ~]#
[iyunv@iptables ~]# /etc/init.d/iptables restart
iptables: Flushing firewall rules: [ OK ]
iptables: Setting chains to policy ACCEPT: filter nat [ OK ]
iptables: Unloading modules: [ OK ]
iptables: Applying firewall rules: [ OK ]
[iyunv@iptables ~]#
|
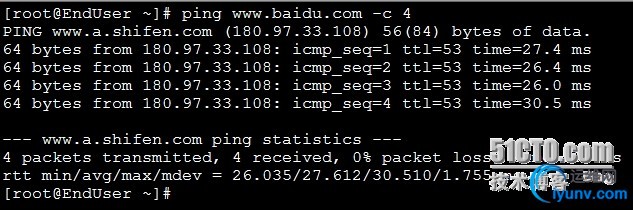
先测试防火墙能否上网:
1
2
3
4
5
6
7
8
9
10
| [iyunv@iptables ~]# ping www.baidu.com -c 4
PING www.a.shifen.com (180.97.33.107) 56(84) bytes of data.
64 bytes from 180.97.33.107: icmp_seq=1 ttl=53 time=27.3 ms
64 bytes from 180.97.33.107: icmp_seq=2 ttl=53 time=26.5 ms
64 bytes from 180.97.33.107: icmp_seq=3 ttl=53 time=25.2 ms
64 bytes from 180.97.33.107: icmp_seq=4 ttl=53 time=24.9 ms
--- www.a.shifen.com ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3031ms
rtt min/avg/max/mdev = 24.994/26.047/27.371/0.977 ms
[iyunv@iptables ~]#
|
测试EndUser:
ping一个windows主机用wireshark抓包:
DNAT测试:

地址规划:
Node
| IP Address
| GW
| WEB
| 192.168.101.241/24
| 192.168.101.1
| iptables
| eth0:192.168.100.242/24
eth1:192.168.101.1/24 | 192.168.100.243
192.168.101.241
| EndUser
| 192.168.100.251/24
| -
|
WEB:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| [iyunv@WEB ~]# tail -n 4 /etc/sysconfig/network-scripts/ifcfg-eth0
BOOTPROTO=static
IPADDR=192.168.101.241
NETMASK=255.255.255.0
GATEWAY=192.168.101.1
[iyunv@WEB ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.101.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
169.254.0.0 0.0.0.0 255.255.0.0 U 1002 0 0 eth0
0.0.0.0 192.168.101.1 0.0.0.0 UG 0 0 0 eth0
[iyunv@WEB ~]#
[iyunv@WEB ~]# ping 192.168.100.242 -c 4
PING 192.168.100.242 (192.168.100.242) 56(84) bytes of data.
64 bytes from 192.168.100.242: icmp_seq=1 ttl=64 time=0.287 ms
64 bytes from 192.168.100.242: icmp_seq=2 ttl=64 time=0.346 ms
64 bytes from 192.168.100.242: icmp_seq=3 ttl=64 time=0.403 ms
64 bytes from 192.168.100.242: icmp_seq=4 ttl=64 time=0.409 ms
--- 192.168.100.242 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3002ms
rtt min/avg/max/mdev = 0.287/0.361/0.409/0.051 ms
[iyunv@WEB ~]#
|
iptables:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| [iyunv@iptables ~]# grep forward /etc/sysctl.conf |grep -v ^#
net.ipv4.ip_forward = 1
[iyunv@iptables ~]#
[iyunv@iptables ~]# tail -n 4 /etc/sysconfig/network-scripts/ifcfg-eth0
BOOTPROTO=static
IPADDR=192.168.100.242
NETMASK=255.255.255.0
GATEWAY=192.168.100.243
[iyunv@iptables ~]# tail -n 4 /etc/sysconfig/network-scripts/ifcfg-eth1
BOOTPROTO=static
IPADDR=192.168.101.1
NETMASK=255.255.255.0
GATEWAY=192.168.101.241
[iyunv@iptables ~]#
[iyunv@iptables ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.100.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
192.168.101.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
169.254.0.0 0.0.0.0 255.255.0.0 U 1002 0 0 eth0
169.254.0.0 0.0.0.0 255.255.0.0 U 1003 0 0 eth1
0.0.0.0 192.168.101.241 0.0.0.0 UG 0 0 0 eth1
[iyunv@iptables ~]#
[iyunv@iptables ~]# iptables -t nat -A PREROUTING -d 192.168.100.242 -p tcp -m tcp --dport 80 -i eth0 -j DNAT --to-destination 192.168.101.241
|
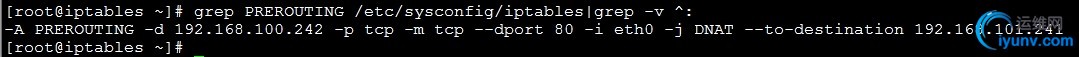
1
2
3
4
5
6
| [iyunv@iptables ~]# /etc/init.d/iptables restart
iptables: Flushing firewall rules: [ OK ]
iptables: Setting chains to policy ACCEPT: filter nat [ OK ]
iptables: Unloading modules: [ OK ]
iptables: Applying firewall rules: [ OK ]
[iyunv@iptables ~]#
|
访问:http://192.168.100.242/


|
|
|