|
|
一.安装ldap
1
2
| [iyunv@dev ~]# yum install openldap openldap-* -y
[iyunv@dev ~]# yum install nscd nss-pam-ldapd nss-* pcre pcre-* -y
|
二.配置ldap
1
2
3
4
5
6
7
| [iyunv@dev ~]# cd /etc/openldap/
[iyunv@dev openldap]# ll
total 16
drwxr-xr-x. 2 root root 4096 Jul 13 20:10 certs
-rw-r--r--. 1 root root 282 Jun 21 17:19 ldap.conf
drwxr-xr-x 2 root root 4096 Jul 13 20:10 schema
drwx------ 3 ldap ldap 4096 Jul 13 20:10 slapd.d
|
复制配置文件
1
2
| [iyunv@dev openldap]# cp /usr/share/openldap-servers/slapd.conf.obsolete slapd.conf
[iyunv@dev openldap]# cp slapd.conf slapd.conf_`date +%Y%m%d`.bak
|
设置ldap管理员密码
1
2
3
4
5
| [iyunv@dev openldap]# slappasswd -s weyee
{SSHA}4zVLzQItaa9wp00xF7oSynhPPNKfGyJ1
[iyunv@dev openldap]# slappasswd -s weyee |sed -e "s#{SSHA}#rootpw\t{SSHA}#g" >>/etc/openldap/slapd.conf #设置密码是weyee
[iyunv@dev openldap]# tail -1 /etc/openldap/slapd.conf
rootpw {SSHA}6jZP4UfMlMfN0XKPch70R5+TiRCV+yT7
|
修改dc配置
1
2
3
4
5
| [iyunv@dev openldap]# vim /etc/openldap/slapd.conf
#以下参数大概在114行
database bdb #使用bdb数据库
suffix "dc=dev,dc=com" #定义dc,指定搜索的域
rootdn "cn=admin,dc=dev,dc=com" #定义管理员的dn,使用这个dn能登陆openldap
|
优化ldap配置参数
1
2
3
4
| [iyunv@dev openldap]# vim /etc/openldap/slapd.conf
loglevel 296 #定义日志级别
cachesize 1000 #换成条目数
checkpoint 2048 10 #表示内存中达到2048k或者10分钟,执行一次checkpoint,即写入数据文件的操作
|
配置相关权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| [iyunv@dev openldap]# vim /etc/openldap/slapd.conf
#删除默认权限,将下面的内容都删除
database config
access to *
by dn.exact="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage
by * none
# enable server status monitoring (cn=monitor)
database monitor
access to *
by dn.exact="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read
by dn.exact="cn=Manager,dc=my-domain,dc=com" read
by * none
#添加新的权限(这是2.3的权限设置方式)
access to *
by self write
by anonymous auth
by * read
|
配置syslog记录ldap的服务日志
1
2
3
4
5
6
7
8
9
10
| [iyunv@dev openldap]# cp /etc/rsyslog.conf /etc/rsyslog.conf_`date +%Y%m%d`.bak
#往配置文件中增加如下内容
[iyunv@dev openldap]# tail -1 /etc/rsyslog.conf
local4.* /var/log/ldap.log
#重启rsyslog服务
[iyunv@dev openldap]# /etc/init.d/rsyslog restart
Shutting down system logger: [ OK ]
Starting system logger: [ OK ]
|
配置ldap数据库路径
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| #创建数据文件
[iyunv@dev openldap]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[iyunv@dev openldap]# chown ldap.ldap /var/lib/ldap/DB_CONFIG
[iyunv@dev openldap]# chmod 700 /var/lib/ldap/
[iyunv@dev openldap]# ll /var/lib/ldap/
total 4
-rw-r--r-- 1 ldap ldap 845 Jul 13 21:05 DB_CONFIG
[iyunv@dev openldap]# egrep -v "\#|^$" /var/lib/ldap/DB_CONFIG
set_cachesize 0 268435456 1
set_lg_regionmax 262144
set_lg_bsize 2097152
[iyunv@dev openldap]# slaptest -u #检查配置文件是否正常
config file testing succeeded
|
ldap最后的完整配置如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
| [iyunv@dev openldap]# egrep -v "\#|^$" /var/lib/ldap/DB_CONFIG
set_cachesize 0 268435456 1
set_lg_regionmax 262144
set_lg_bsize 2097152
[iyunv@dev openldap]# slaptest -u
config file testing succeeded
[iyunv@dev openldap]# egrep -v "^#|^$" /etc/openldap/slapd.conf
include /etc/openldap/schema/corba.schema
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/duaconf.schema
include /etc/openldap/schema/dyngroup.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/java.schema
include /etc/openldap/schema/misc.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/openldap.schema
include /etc/openldap/schema/ppolicy.schema
include /etc/openldap/schema/collective.schema
allow bind_v2
pidfile /var/run/openldap/slapd.pid
argsfile /var/run/openldap/slapd.args
TLSCACertificatePath /etc/openldap/certs
TLSCertificateFile "\"OpenLDAP Server\""
TLSCertificateKeyFile /etc/openldap/certs/password
access to *
by self write
by anonymous auth
by * read
database bdb
suffix "dc=dev,dc=com"
checkpoint 1024 15
rootdn "cn=admin,dc=dev,dc=com"
directory /var/lib/ldap
index objectClass eq,pres
index ou,cn,mail,surname,givenname eq,pres,sub
index uidNumber,gidNumber,loginShell eq,pres
index uid,memberUid eq,pres,sub
index nisMapName,nisMapEntry eq,pres,sub
rootpw {SSHA}6jZP4UfMlMfN0XKPch70R5+TiRCV+yT7
loglevel 296
cachesize 1000
checkpoint 2048 10
|
三.启动ldap服务
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| [iyunv@dev ~]# /etc/init.d/slapd start
Starting slapd: [ OK ]
[iyunv@dev ~]# ps aux |grep ldap
ldap 2012 0.3 1.9 490532 19656 ? Ssl 21:13 0:00 /usr/sbin/slapd -h ldap:/// ldapi:/// -u ldap
root 2018 0.0 0.0 103248 872 pts/0 S+ 21:14 0:00 grep ldap
[iyunv@dev ~]# netstat -tunlp |grep slapd
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 2012/slapd
tcp 0 0 :::389 :::* LISTEN 2012/slapd #普通端口389,加密后的是689
#添加到开机自启动
[iyunv@dev ~]# chkconfig slapd on
#查看日志文件
[iyunv@dev ~]# tail /var/log/ldap.log
Jul 13 21:14:00 dev slapd[2011]: @(#) $OpenLDAP: slapd 2.4.39 (Oct 15 2014 09:51:43) $#012#011mockbuild@c6b8.bsys.dev.centos.org:/builddir/build/BUILD/openldap-2.4.39/openldap-2.4.39/build-servers/servers/slapd
|
查询一下ldap的内容
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| [iyunv@dev ~]# ldapsearch -LLL -W -x -H ldap://dev.com -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=*)"
Enter LDAP Password:
ldap_bind: Invalid credentials (49) #这里报错
#解决如下,删除默认2.4的配置文件,重新生成2.3的配置文件
[iyunv@dev ~]# rm -rf /etc/openldap/slapd.d/*
[iyunv@dev ~]# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/
55a3bf76 bdb_monitor_db_open: monitoring disabled; configure monitor database to enable
config file testing succeeded [ OK ]
[iyunv@dev ~]# ll /etc/openldap/slapd.d/
total 8
drwxr-x--- 3 root root 4096 Jul 13 21:39 cn=config
-rw------- 1 root root 1302 Jul 13 21:39 cn=config.ldif
#重启服务
[iyunv@dev ~]# /etc/init.d/slapd restart
Stopping slapd: [ OK ]
Checking configuration files for slapd: [FAILED]
55a3bfd6 ldif_read_file: Permission denied for "/etc/openldap/slapd.d/cn=config.ldif"
slaptest: bad configuration file!
[iyunv@dev ~]# chown -R ldap.ldap /etc/openldap/slapd.d
[iyunv@dev ~]# /etc/init.d/slapd restart
Stopping slapd: [FAILED]
Starting slapd: [ OK ]
[iyunv@dev ~]# netstat -tunlp |grep slapd
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 5906/slapd
tcp 0 0 :::389 :::* LISTEN 5906/slapd
#再重新查询ldap内容
[iyunv@dev ~]# ldapsearch -LLL -W -x -H ldap://dev.com -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=*)"
Enter LDAP Password: #密码是上文中的weyee
No such object (32) #ldap中还没有任何数据
|
附上2个脚本
添加本地存在用户到目录服务
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
| #脚本内容
[iyunv@dev ~]# cat ldapuser.sh
###### ldapuser script start ######
# extract local users who have 500-999 digit UID
# replace "SUFFIX=***" to your own suffix
# this is an example
#!/bin/bash
SUFFIX='dc=dev,dc=com'
LDIF='ldapuser.ldif'
echo -n > $LDIF
for line in `grep "x:[5-9][0-9][0-9]:" /etc/passwd | sed -e "s/ /%/g"`
do
UID1=`echo $line | cut -d: -f1`
NAME=`echo $line | cut -d: -f5 | cut -d, -f1`
if [ ! "$NAME" ]
then
NAME=$UID1
else
NAME=`echo $NAME | sed -e "s/%/ /g"`
fi
SN=`echo $NAME | awk '{print $2}'`
if [ ! "$SN" ]
then
SN=$NAME
fi
GIVEN=`echo $NAME | awk '{print $1}'`
UID2=`echo $line | cut -d: -f3`
GID=`echo $line | cut -d: -f4`
PASS=`grep $UID1: /etc/shadow | cut -d: -f2`
SHELL=`echo $line | cut -d: -f7`
HOME=`echo $line | cut -d: -f6`
EXPIRE=`passwd -S $UID1 | awk '{print $7}'`
FLAG=`grep $UID1: /etc/shadow | cut -d: -f9`
if [ ! "$FLAG" ]
then
FLAG="0"
fi
WARN=`passwd -S $UID1 | awk '{print $6}'`
MIN=`passwd -S $UID1 | awk '{print $4}'`
MAX=`passwd -S $UID1 | awk '{print $5}'`
LAST=`grep $UID1: /etc/shadow | cut -d: -f3`
echo "dn: uid=$UID1,ou=people,$SUFFIX" >> $LDIF
echo "objectClass: inetOrgPerson" >> $LDIF
echo "objectClass: posixAccount" >> $LDIF
echo "objectClass: shadowAccount" >> $LDIF
echo "uid: $UID1" >> $LDIF
echo "sn: $SN" >> $LDIF
echo "givenName: $GIVEN" >> $LDIF
echo "cn: $NAME" >> $LDIF
echo "displayName: $NAME" >> $LDIF
echo "uidNumber: $UID2" >> $LDIF
echo "gidNumber: $GID" >> $LDIF
echo "userPassword: {crypt}$PASS" >> $LDIF
echo "gecos: $NAME" >> $LDIF
echo "loginShell: $SHELL" >> $LDIF
echo "homeDirectory: $HOME" >> $LDIF
echo "shadowExpire: $EXPIRE" >> $LDIF
echo "shadowFlag: $FLAG" >> $LDIF
echo "shadowWarning: $WARN" >> $LDIF
echo "shadowMin: $MIN" >> $LDIF
echo "shadowMax: $MAX" >> $LDIF
echo "shadowLastChange: $LAST" >> $LDIF
echo >> $LDIF
done
###### ldapuser script end ######
#使用方法
[iyunv@dev ~]# sh ldapuser.sh
[iyunv@dev ~]# ldapadd -x -D cn=admin,dc=dev,dc=com -W -f ldapuser.ldif
|
添加本地存在组到目录服务
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| #脚本内容
[iyunv@dev ~]# cat ldapgroup.sh
# extract local groups who have 500-999 digit UID
# replace "SUFFIX=***" to your own suffix
# this is an example
#!/bin/bash
SUFFIX='dc=dev,dc=com'
LDIF='ldapgroup.ldif'
echo -n > $LDIF
for line in `grep "x:[5-9][0-9][0-9]:" /etc/group`
do
CN=`echo $line | cut -d: -f1`
GID=`echo $line | cut -d: -f3`
echo "dn: cn=$CN,ou=groups,$SUFFIX" >> $LDIF
echo "objectClass: posixGroup" >> $LDIF
echo "cn: $CN" >> $LDIF
echo "gidNumber: $GID" >> $LDIF
users=`echo $line | cut -d: -f4 | sed "s/,/ /g"`
for user in ${users} ; do
echo "memberUid: ${user}" >> $LDIF
done
echo >> $LDIF
done
#使用方法和前面的脚本一样
|
添加一个系统用户,使用脚本添加进ldap中
1
2
3
4
5
6
7
8
9
| #创建系统用户user1,设置密码user1
[iyunv@dev ~]# useradd user1
[iyunv@dev ~]# passwd user1
Changing password for user user1.
New password:
BAD PASSWORD: it is too short
BAD PASSWORD: is too simple
Retype new password:
passwd: all authentication tokens updated successfully.
|
四.安装migrationtools
1
| [iyunv@dev ~]# yum install migrationtools -y
|
编辑migrationtool的配置文件/usr/share/migrationtools/migrate_common.ph
1
2
3
4
5
6
| [iyunv@dev ~]# vim /usr/share/migrationtools/migrate_common.ph
# Default DNS domain
$DEFAULT_MAIL_DOMAIN = "dev.com";
# Default base
$DEFAULT_BASE = "dc=dev,dc=com";
|
下面利用pl脚本将/etc/passwd 和/etc/shadow生成LDAP能读懂的文件格式,保存在/tmp/下
1
2
3
| [iyunv@dev ~]# /usr/share/migrationtools/migrate_base.pl >/tmp/base.ldif
[iyunv@dev ~]# /usr/share/migrationtools/migrate_passwd.pl /etc/passwd >/tmp/passwd.ldif
[iyunv@dev ~]# /usr/share/migrationtools/migrate_passwd.pl /etc/group >/tmp/group.ldif
|
下面就要把这三个文件导入到LDAP,这样LDAP的数据库里就有了我们想要的用户
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
| #导入base
[iyunv@dev ~]# ldapadd -x -D "cn=admin,dc=dev,dc=com" -W -f /tmp/base.ldif
Enter LDAP Password:
adding new entry "dc=dev,dc=com"
adding new entry "ou=Hosts,dc=dev,dc=com"
adding new entry "ou=Rpc,dc=dev,dc=com"
adding new entry "ou=Services,dc=dev,dc=com"
adding new entry "nisMapName=netgroup.byuser,dc=dev,dc=com"
adding new entry "ou=Mounts,dc=dev,dc=com"
adding new entry "ou=Networks,dc=dev,dc=com"
adding new entry "ou=People,dc=dev,dc=com"
adding new entry "ou=Group,dc=dev,dc=com"
adding new entry "ou=Netgroup,dc=dev,dc=com"
adding new entry "ou=Protocols,dc=dev,dc=com"
adding new entry "ou=Aliases,dc=dev,dc=com"
adding new entry "nisMapName=netgroup.byhost,dc=dev,dc=com"
#导入passwd
[iyunv@dev ~]# ldapadd -x -D "cn=admin,dc=dev,dc=com" -W -f /tmp/passwd.ldif
Enter LDAP Password:
adding new entry "uid=root,ou=People,dc=dev,dc=com"
adding new entry "uid=bin,ou=People,dc=dev,dc=com"
adding new entry "uid=daemon,ou=People,dc=dev,dc=com"
adding new entry "uid=adm,ou=People,dc=dev,dc=com"
adding new entry "uid=lp,ou=People,dc=dev,dc=com"
adding new entry "uid=sync,ou=People,dc=dev,dc=com"
adding new entry "uid=shutdown,ou=People,dc=dev,dc=com"
adding new entry "uid=halt,ou=People,dc=dev,dc=com"
adding new entry "uid=mail,ou=People,dc=dev,dc=com"
adding new entry "uid=uucp,ou=People,dc=dev,dc=com"
adding new entry "uid=operator,ou=People,dc=dev,dc=com"
adding new entry "uid=games,ou=People,dc=dev,dc=com"
adding new entry "uid=gopher,ou=People,dc=dev,dc=com"
adding new entry "uid=ftp,ou=People,dc=dev,dc=com"
adding new entry "uid=nobody,ou=People,dc=dev,dc=com"
adding new entry "uid=dbus,ou=People,dc=dev,dc=com"
adding new entry "uid=vcsa,ou=People,dc=dev,dc=com"
adding new entry "uid=abrt,ou=People,dc=dev,dc=com"
adding new entry "uid=haldaemon,ou=People,dc=dev,dc=com"
adding new entry "uid=ntp,ou=People,dc=dev,dc=com"
adding new entry "uid=saslauth,ou=People,dc=dev,dc=com"
adding new entry "uid=postfix,ou=People,dc=dev,dc=com"
adding new entry "uid=sshd,ou=People,dc=dev,dc=com"
adding new entry "uid=tcpdump,ou=People,dc=dev,dc=com"
adding new entry "uid=rpc,ou=People,dc=dev,dc=com"
adding new entry "uid=hacluster,ou=People,dc=dev,dc=com"
adding new entry "uid=rpcuser,ou=People,dc=dev,dc=com"
adding new entry "uid=nfsnobody,ou=People,dc=dev,dc=com"
adding new entry "uid=ldap,ou=People,dc=dev,dc=com"
adding new entry "uid=nscd,ou=People,dc=dev,dc=com"
adding new entry "uid=nslcd,ou=People,dc=dev,dc=com"
adding new entry "uid=user1,ou=People,dc=dev,dc=com"
#导入group
[iyunv@dev ~]# ldapadd -x -D "cn=admin,dc=dev,dc=com" -W -f /tmp/group.ldif
|
再次查询ldap的内容
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| [iyunv@dev ~]# ldapsearch -LLL -W -x -H ldap://dev.com -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=user1)"
Enter LDAP Password:
dn: uid=user1,ou=People,dc=dev,dc=com
uid: user1 #这里我们只查询user1
cn: user1
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:: e2NyeXB0fSQxJC5CTHJNWDJEJE9FYnNMc2N4S3NQQ2liLk5uVC5ZMTA=
shadowLastChange: 16629
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 500
gidNumber: 500
homeDirectory: /home/user1
#不用输入密码查询
[iyunv@dev ~]# ldapsearch -LLL -w weyee -x -H ldap://dev.com -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=user1)"
dn: uid=user1,ou=People,dc=dev,dc=com
uid: user1
cn: user1
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:: e2NyeXB0fSQxJC5CTHJNWDJEJE9FYnNMc2N4S3NQQ2liLk5uVC5ZMTA=
shadowLastChange: 16629
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 500
gidNumber: 500
homeDirectory: /home/user1
|
备份ldap数据
1
| [iyunv@dev ~]# ldapsearch -LLL -w weyee -x -H ldap://dev.com -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" >ldap.bak
|
五.安装配置ldap客户端ldap-account-manager
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| #安装软件包
[iyunv@dev ~]# yum install httpd php php-ldap php-gd -y
#下载软件包
[iyunv@dev ~]# wget http://downloads.sourceforge.net ... &use_mirror=ncu
[iyunv@dev ~]# tar xf ldap-account-manager-3.7.tar.gz
[iyunv@dev ~]# cd /var/www/html/
[iyunv@dev html]# cp -r ~/ldap-account-manager-3.7 .
[iyunv@dev html]# mv ldap-account-manager-3.7 ldap
[iyunv@dev html]# cd ldap/config
[iyunv@dev config]# cp config.cfg_sample config.cfg
[iyunv@dev config]# cp lam.conf_sample lam.conf
[iyunv@dev config]# sed -i 's#cn=Manager#cn=admin#g' lam.conf
[iyunv@dev config]# sed -i 's#dc=my-domain#dc=dev#g' lam.conf
[iyunv@dev config]# chown -R apache.apache /var/www/html/ldap
[iyunv@dev config]# /etc/init.d/httpd start
Starting httpd: [ OK ]
|
访问web界面http://192.168.1.13/ldap
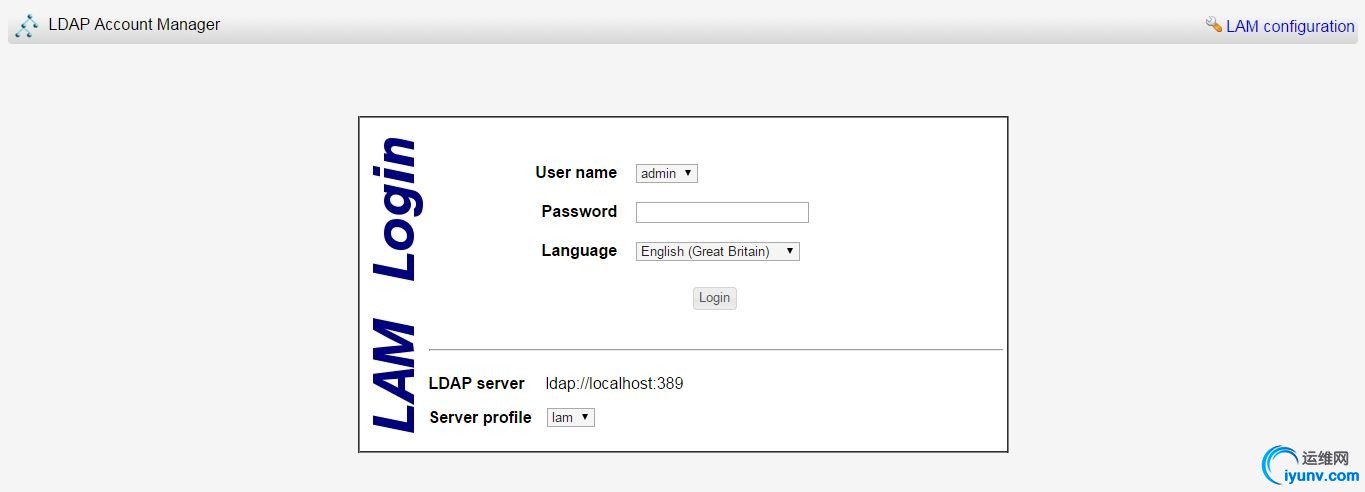
出现这个界面后需要先配置,点击lam configuration,默认密码是lam
登陆后的界面如下
创建一个新用户www
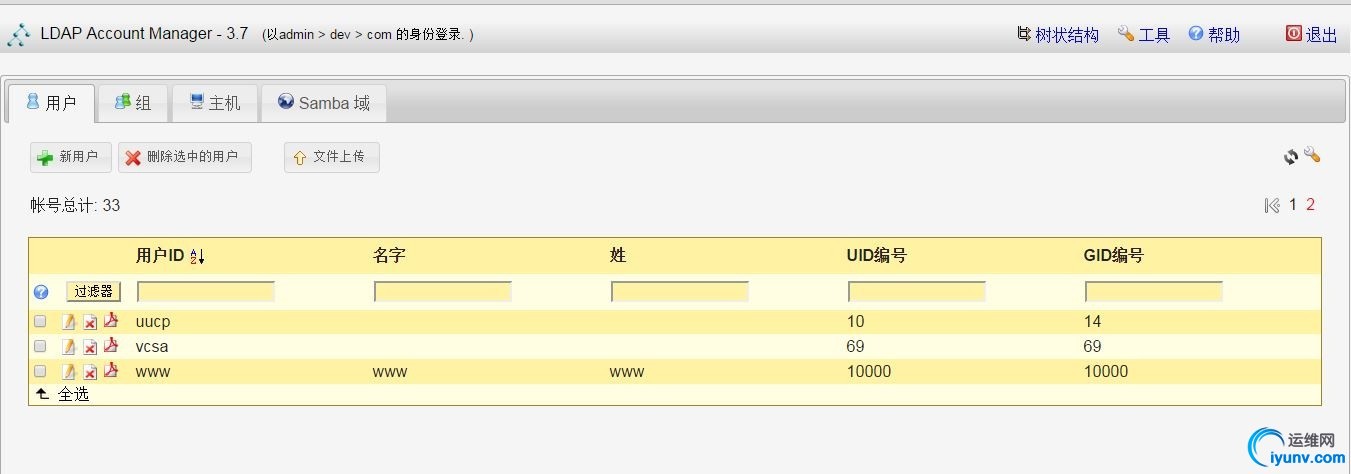
在系统中查询刚才添加的结果
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| [iyunv@dev ~]# ldapsearch -LLL -w weyee -x -H ldap://192.168.1.13 -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=www)"
dn: uid=www,ou=People,dc=dev,dc=com
objectClass: posixAccount
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
homeDirectory: /home/wwww
loginShell: /bin/bash
cn: www www
uidNumber: 10000
gidNumber: 10000
userPassword:: e1NTSEF9K2VUTGdMYmo3WWZ3K25kQlRZNnlRaks5MHVWQUtXK3I=
sn: www
givenName: www
uid: www
|
六、配置svn+sasl通过ldap进行身份认证(独立的svn服务)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
| #安装sasl
[iyunv@dev ~]# yum install *sasl* -y
#查看sasl的认证机制
[iyunv@dev ~]# saslauthd -v
saslauthd 2.1.23
authentication mechanisms: getpwent kerberos5 pam rimap shadow ldap
#默认的认证方式如下
#忽略大小写查询
[iyunv@dev ~]# grep -i mech /etc/sysconfig/saslauthd
# Mechanism to use when checking passwords. Run "saslauthd -v" to get a list
# of which mechanism your installation was compiled with the ablity to use.
MECH=pam
# Options sent to the saslauthd. If the MECH is other than "pam" uncomment the next line.
#将认证方式改成shadow测试一下
[iyunv@dev ~]# sed -i 's#MECH=pam#MECH=shadow#g' /etc/sysconfig/saslauthd
[iyunv@dev ~]# grep -i mech /etc/sysconfig/saslauthd
# Mechanism to use when checking passwords. Run "saslauthd -v" to get a list
# of which mechanism your installation was compiled with the ablity to use.
MECH=shadow
# Options sent to the saslauthd. If the MECH is other than "pam" uncomment the next line.
#重启sasl服务
[iyunv@dev ~]# /etc/init.d/saslauthd restart
Stopping saslauthd: [FAILED]
Starting saslauthd: [ OK ]
[iyunv@dev ~]# ps aux |grep sasl
root 1848 0.0 0.0 66376 1000 ? Ss 21:12 0:00 /usr/sbin/saslauthd -m /var/run/saslauthd -a shadow
root 1850 0.0 0.0 66376 688 ? S 21:12 0:00 /usr/sbin/saslauthd -m /var/run/saslauthd -a shadow
root 1851 0.0 0.0 66376 688 ? S 21:12 0:00 /usr/sbin/saslauthd -m /var/run/saslauthd -a shadow
root 1852 0.0 0.0 66376 688 ? S 21:12 0:00 /usr/sbin/saslauthd -m /var/run/saslauthd -a shadow
root 1853 0.0 0.0 66376 688 ? S 21:12 0:00 /usr/sbin/saslauthd -m /var/run/saslauthd -a shadow
root 1858 0.0 0.0 103248 836 pts/0 S+ 21:13 0:00 grep sasl
#使用本地系统账号进行测试
[iyunv@dev ~]# testsaslauthd -uroot -p123123
0: OK "Success." #测试成功
#配置通过ldap进行认证,修改sasl的认证方式
[iyunv@dev ~]# sed -i 's#MECH=shadow#MECH=ldap#g' /etc/sysconfig/saslauthd
[iyunv@dev ~]# grep MECH /etc/sysconfig/saslauthd
MECH=ldap
[iyunv@dev ~]# /etc/init.d/saslauthd restart
Stopping saslauthd: [ OK ]
Starting saslauthd: [ OK ]
#创建sasl认证配置文件
[iyunv@dev ~]# cat /etc/saslauthd.conf
ldap_servers: ldap://192.168.1.13/
ldap_bind_dn: cn=admin,dc=dev,dc=com
ldap_bind_pw: weyee
ldap_search_base: ou=People,dc=dev,dc=com
ldap_filter: uid=%U
ldap_password_attr: userPassword
#用户www只在ldap中有
[iyunv@dev ~]# id www
id: www: No such user
[iyunv@dev ~]# ldapsearch -LLL -w weyee -x -H ldap://192.168.1.13 -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=www)"
dn: uid=www,ou=People,dc=dev,dc=com
objectClass: posixAccount
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
homeDirectory: /home/wwww
loginShell: /bin/bash
cn: www www
uidNumber: 10000
gidNumber: 10000
userPassword:: e1NTSEF9K2VUTGdMYmo3WWZ3K25kQlRZNnlRaks5MHVWQUtXK3I=
sn: www
givenName: www
uid: www
#从上面的结果中能看出www是ldap中的用户
#测试
[iyunv@dev ~]# testsaslauthd -uwww -pwww
0: OK "Success." #测试成功
|
安装配置svn
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
| [iyunv@dev ~]# yum install subversion -y
#创建相关目录
[iyunv@dev ~]# mkdir -p /data/svndata
[iyunv@dev ~]# mkdir -p /data/svnpasswd
#启动svn
[iyunv@dev ~]# svnserve -d -r /data/svndata/
[iyunv@dev ~]# netstat -tunlp|grep svn
tcp 0 0 0.0.0.0:3690 0.0.0.0:* LISTEN 2259/svnserve
#创建项目
[iyunv@dev ~]# svnadmin create /data/svndata/sadoc
[iyunv@dev ~]# cd /data/svndata/sadoc/
[iyunv@dev sadoc]# cd conf/
[iyunv@dev conf]# cp svnserve.conf svnserve.conf_`date +%Y%m%d`.bak
[iyunv@dev conf]# sed -i 's/#auth-access=write/auth-access=write/' svnserve.conf
#修改后的配置文件内容如下
[iyunv@dev conf]# egrep -v "^$|^#" svnserve.conf
[general]
anon-access = none
auth-access=write
password-db = /data/svnpasswd/passwd
authz-db = /data/svnpasswd/authz
[sasl]
#复制权限配置文件
[iyunv@dev conf]# pwd
/data/svndata/sadoc/conf
[iyunv@dev conf]# cp authz passwd /data/svnpasswd/
[iyunv@dev conf]# chmod 700 /data/svnpasswd/
[iyunv@dev conf]# pkill svnserve
[iyunv@dev conf]# ps aux |grep svn
root 2293 0.0 0.0 103248 848 pts/0 S+ 21:56 0:00 grep svn
#配置svn通过ldap认证
#创建认证配置文件
[iyunv@dev ~]# cat /etc/sasl2/svn.conf
pwcheck_method: saslauthd
mech_list: PLAIN LOGIN
#重启sasl服务
[iyunv@dev ~]# /etc/init.d/saslauthd restart
Stopping saslauthd: [ OK ]
Starting saslauthd: [ OK ]
[iyunv@dev ~]# testsaslauthd -uwww -pwww
0: OK "Success."
#更改svn配置文件sasl参数
[iyunv@dev ~]# cd /data/svndata/sadoc/
[iyunv@dev sadoc]# cd conf/
[iyunv@dev conf]# cp svnserve.conf svnserve.conf_`date +%Y%m%d`.bak
[iyunv@dev conf]# egrep -v "^#|^$" svnserve.conf
[general]
anon-access = none
auth-access=write
password-db = /data/svnpasswd/passwd
authz-db = /data/svnpasswd/authz
[sasl]
use-sasl = true #开启认证
[iyunv@dev ~]# pkill svnserve
[iyunv@dev ~]# svnserve -d -r /data/svndata/
#在authz文件中赋予权限
[iyunv@dev ~]# egrep -v "^$|^#" /data/svnpasswd/authz
[aliases]
[groups]
admin = www
[sadoc:/]
@admin = rw
#测试
[iyunv@dev ~]# id www
id: www: No such user
[iyunv@dev ~]# ldapsearch -LLL -w weyee -x -H ldap://192.168.1.13 -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=www)"
dn: uid=www,ou=People,dc=dev,dc=com
objectClass: posixAccount
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
homeDirectory: /home/wwww
loginShell: /bin/bash
cn: www www
uidNumber: 10000
gidNumber: 10000
userPassword:: e1NTSEF9K2VUTGdMYmo3WWZ3K25kQlRZNnlRaks5MHVWQUtXK3I=
sn: www
givenName: www
uid: www
#访问svn服务器
[iyunv@dev ~]# svn co svn://192.168.1.13/sadoc /tmp --username=www --password=www
-----------------------------------------------------------------------
ATTENTION! Your password for authentication realm:
<svn://192.168.1.13:3690> d3eed2b4-64de-4aec-836a-39bc34d3d957
can only be stored to disk unencrypted! You are advised to configure
your system so that Subversion can store passwords encrypted, if
possible. See the documentation for details.
You can avoid future appearances of this warning by setting the value
of the 'store-plaintext-passwords' option to either 'yes' or 'no' in
'/root/.subversion/servers'.
-----------------------------------------------------------------------
Store password unencrypted (yes/no)? yes
Checked out revision 0.
#结果显示能通过ldap认证正常访问svn服务器
#我们在ldap中添加一个用户ldapsvn,密码是ldapsvn再次认证一次
[iyunv@dev ~]# id ldapsvn
id: ldapsvn: No such user
[iyunv@dev ~]# ldapsearch -LLL -w weyee -x -H ldap://192.168.1.13 -D "cn=admin,dc=dev,dc=com" -b "dc=dev,dc=com" "(uid=ldapsvn)"
dn: uid=ldapsvn,ou=People,dc=dev,dc=com
objectClass: posixAccount
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
homeDirectory: /home/ldapsvn
loginShell: /bin/bash
uid: ldapsvn
cn: ldapsvn ldapsvn
userPassword:: e1NTSEF9Zno4TjZBZ2FwWWo3NUY3ZGl5ZU5uKzJyd0lQVlVHUlc=
uidNumber: 10001
gidNumber: 10000
sn: ldapsvn
givenName: ldapsvn
#将ldapsvn添加到authz文件中,过程略
[iyunv@dev ~]# svn co svn://192.168.1.13/sadoc /tmp/test/ --username=ldapsvn --password=ldapsvn
-----------------------------------------------------------------------
ATTENTION! Your password for authentication realm:
<svn://192.168.1.13:3690> d3eed2b4-64de-4aec-836a-39bc34d3d957
can only be stored to disk unencrypted! You are advised to configure
your system so that Subversion can store passwords encrypted, if
possible. See the documentation for details.
You can avoid future appearances of this warning by setting the value
of the 'store-plaintext-passwords' option to either 'yes' or 'no' in
'/root/.subversion/servers'.
-----------------------------------------------------------------------
Store password unencrypted (yes/no)? yes
Checked out revision 0.
#到此svn+ldap认证配置过程结束
|
|
|